Cybersecurity Market Size, Share & Trends Analysis Report by Solution Type (Network Security, Endpoint Security Solutions, Application Security Solutions, Cloud Security Solutions, Data Security Solutions, Identity & Access Management (IAM)), Deployment Mode, Organization Size, Service Type, Threat Type, End-Use Industry and Geography (North America, Europe, Asia Pacific, Middle East, Africa, and South America) – Global Industry Data, Trends, and Forecasts, 2025–2035
|
Market Structure & Evolution |
|
|
Segmental Data Insights |
|
|
Demand Trends |
|
|
Competitive Landscape |
|
|
Strategic Development |
|
|
Future Outlook & Opportunities |
|
Cybersecurity Market Size, Share, And Growth
The global cybersecurity market is experiencing robust growth, with its estimated value of USD 230.7 billion in the year 2025 and USD 722.9 billion by the period 2035, registering a CAGR of 12.1%. Asia Pacific leads the market with market share of 46% with USD 106.8 billion revenue.

Ava Mitchell, who holds the position of Chief Security Officer at CyberFort Systems, stated, "As we build our cybersecurity platform, we have the focus on making threat protection smarter, faster, and more resilient—offering automation, compliance, and adaptive security frameworks to help organizations stay one step ahead of ever-evolving cyber threats and regulatory challenges, particularly in this ever-increasing digital world.
The global cybersecurity market is mainly the result of rising digital transformation initiatives, increasing cyber threats, and evolving regulatory constraints. Companies across sectors are heavily investing in advanced technologies like AI, machine learning, and zero-trust architectures to improve threat detection, automate response, and protect critical data assets.
In early 2025, for example, SecureNet Solutions launched an AI-based cybersecurity platform that connects real-time threat intelligence and automated incident response, allowing enterprises to proactively mitigate risks and comply with global data privacy compliance. In addition, cloud-native security solutions, and API-first models allow easy integration into enterprise systems such as SIEM, IAM, and endpoint management to improve operational efficiency.
Meanwhile, a remote workforce and use of Internet of Things (IoT) devices continue to elevate the desire for adaptive, scalable cyber protection. Related opportunities for growth center on managed security services, blockchain-based identity assurance, and secure access service edge (SASE) solutions as organizations search for resiliency, and automated defenses against a wide variety of evolving threats.
Cybersecurity Market Dynamics and Trends

Driver: Increasing Demand for Automated Threat Detection and Response in Complex IT Environments
Expansion
- As IT systems become more complex and cyberattacks continue to increase, organizations are driven to utilize sophisticated automated cybersecurity products aimed at increasing threat detection and simplifying the incident response process. These systems help organizations lower operational costs and reduce response times, all while protecting valuable assets.
- For example, in March 2025, Palo Alto Networks introduced an AI camera and security system that combined automated threat intelligence with real-time response features so that organizations could defend against complex and advanced cyberattacks proactively. This offers some perspective into the clear need for flexible security systems that balance operational efficiency with strong protection.
- Owing to an increase in cloud consumption, a remote workforce, and connected devices (IoT), there is a growing need for centralized cybersecurity and a drive for organizations to invest in combined solutions for security management. platforms intended to ensure compliance and an integrated defense across several environments.
Restraint: Rising Security and Compliance Concerns Restricting Adoption of Advanced Cybersecurity Solutions Across Highly Regulated Verticals Globally
- In positing sophisticated cybersecurity solutions offer significant security benefits, regulatory compliance requirements and compliance issues, particularly in industries such as healthcare, finance, and government, can often prevent wide adoption. Privacy concerns, conflicts over other policy, and regulatory fines can create practical roadblocks faced by organizations evaluating new security technology.
- For example, in May 2024, Symantec leveled-up its cybersecurity solutions platform with features that adopted features and capabilities specifically designed for HIPAA, GDPR and other regulatory requirements, both demonstrating and responding to vendor friction about compliance. In practice these descriptions only serve to highlight the organizational complications in acquiring and integrating these solutions so statute level compliance could be achieved.
- Effectively managing the correct balance between best-in-class cybersecurity service delivery and statutory compliance, is an increasingly detainee issue which results in decreased adoption of cyber security in industries with statutory data privacy prevention requirements.
Opportunity: Expanding Opportunities Through AI-Powered Cybersecurity Solutions Enhancing Threat Prediction and Incident Response
- The incorporation of artificial intelligence in cybersecurity platforms is paving the path for new possibilities by facilitating predictive threat detection, automated response, and adaptive defense strategies. AI-enhanced analytics support enhanced risk evaluation and resource allocation, while intelligent automation leads to shorter response times and an improved security posture.
- A notable instance, CrowdStrike made its first mention of AI capabilities within its Falcon platform in February 2025, bringing predictive capabilities powered by continuous behavioral analysis and automated threat hunting to its users to predict and prevent cyber risk. The additional benefits to its customers and organizations are not only enhanced security but a significantly reduced operational burden on cybersecurity teams, thereby making AI-driven/implemented services attractive for enterprises.
- Therefore, this is indicative not only of the better security capabilities that lie ahead, but that organizations would only further evolve from traditional protection into intelligent, proactive security strategies that emphasize predictive (defense/capabilities) and operational efficiency.
Key Trend: Growing Trend of Cloud-Native Cybersecurity Solutions Supporting Scalability and Hybrid IT Environments
- One of the critical trends in the cybersecurity market is the shift to cloud-native cybersecurity platforms driven by organizations' need for scalable and flexible security solutions for hybrid and multi-cloud environments. Cloud-based security provides the necessary capabilities for seamless threat monitoring, automated policy enforcement, and secure access management for dispersed work forces.
- In September 2024, Palo Alto Networks announced its enhancement of its Prisma Cloud platform with newly added cloud-native security capabilities to improve integration with multi-cloud infrastructures and meet the evolving needs of enterprise IT environments. Resolver Viewpoint Cloud-native cybersecurity solutions simplify operations while providing a through-line to scale protection in an organization as it matures.
- This represents a larger shift from traditional perimeter defense systems to full cloud-driven security ecosystems that align with modern and digital-first business models.
Cybersecurity Market Analysis and Segmental Data

Identity & Access Management (IAM) Maintain Dominance in Global Cybersecurity Market amid Rising Cyber Threats and Regulatory Compliance Demands
- Identity & Access Management (IAM) solutions for large enterprises and regulated industries would continue to be the dominant player in the global cybersecurity market. This is primarily due to IAM's vital role in managing complex access controls and facilitating compliance with evolving regulations, including GDPR, HIPAA, CCPA, and NIST standards. Features like centralized user authentication, real-time monitoring of access, and advanced risk-based analytics are necessary for organizations doing business across industries and geographical boundaries.
- Advancements in 2025 included the extension of Okta's IAM platform to include AI-powered adaptive authentication and automated compliance reporting tools designed to support multinational corporations and government agencies. These advancements provide real-time detection of threats, improved identity governance, and faster reaction to regulatory compliance changes resulting in an organization's enhanced security and overall audit readiness.
- The increasing complexity associated with hybrid work environments, zero trust adoption, and cloud migration is driving enterprises to increasingly Adopt more sophisticated, and more modular IAM Solutions. Built-in Identity lifecycle management, customizable policy enforcement, and data governance have all become necessary functional capabilities in the wake of mounting cybersecurity regulations and increasing demand for secure and transparent access management.
Asia Pacific Leads the Cybersecurity Market amid Rapid Digital Transformation and Increasing Cyber Threats
- The Asia Pacific region is quickly becoming an influential player in the global cybersecurity market as a result of accelerated digital transformation across multiple sectors, increased cloud technology adoption, and heightened levels of increasingly sophisticated levels of cyber threat. Increased investments in smart cities, e-commerce, and digital banking are all supporting demand for the region's tailored advanced cybersecurity solutions that meet its evolving regulatory and infrastructural challenges.
- This has been exemplified as major corporations like DBS Bank and Alibaba launched next-generation cybersecurity platforms in 2024 that supported AI powered threat detection, automated compliance monitoring, and integrated identity management. These efforts demonstrate the region’s push towards greater operational resilience, improved data privacy, and delivering customers secure digital environments.
- Additionally, strong governmental endorsement via broader cybersecurity frameworks and data protection laws, paired with a strong fintech ecosystem is driving widespread adoption of AI-enabled, cloud-native security solutions. Together these drivers are enabling Asia Pacific to maintain its prominence and leadership in the global cybersecurity market amidst a rapidly changing regulatory environment and increase cyber risk.
Cybersecurity-Market Ecosystem
The global cybersecurity market for is fairly consolidated, with Tier 1 players like Microsoft, Palo Alto Networks, IBM, and CrowdStrike controlling a significant portion of the market share. These firms have enormous business portfolios and capabilities in innovation. Tier 2 and Tier 3 organizations, such as Darktrace and SentinelOne, help produce some level of competitive variety with their niche offerings. Buyer power is moderate since today's enterprise customers want customized and scalable solutions. Supplier power is also moderate which has resulted in balanced negotiating power due to specialized technology and expertise needed by a vendor.

Recent Development and Strategic Overview:
- In March 2025, Palo Alto Networks, Inc. enhanced its cybersecurity portfolio by launching an AI-powered threat intelligence platform that integrates real-time risk analytics and automated incident response. The solution enables enterprises to detect sophisticated cyberattacks faster, improve compliance monitoring, and streamline security operations, thereby reducing breach impact and operational costs while supporting evolving regulatory mandates across multiple industries.
- In February 2025, Fortinet, Inc. launched a cloud-native, AI-powered solution to broaden the security fabric ecosystem for protecting hybrid IT environments. This enhanced offering provides unified threat management, automated compliance reporting, and adaptive access controls to help organizations efficiently secure critical assets, maximize security workflows, and comply with stringent local and global regulatory requirements.
Report Scope
|
Attribute |
Detail |
|
Market Size in 2025 |
USD 230.7 Bn |
|
Market Forecast Value in 2035 |
USD 722.9 Bn |
|
Growth Rate (CAGR) |
12.1% |
|
Forecast Period |
2025 – 2035 |
|
Historical Data Available for |
2021 – 2024 |
|
Market Size Units |
USD Bn for Value |
|
Report Format |
Electronic (PDF) + Excel |
|
Regions and Countries Covered |
|||||
|
North America |
Europe |
Asia Pacific |
Middle East |
Africa |
South America |
|
|
|
|
|
|
|
Companies Covered |
|||||
|
|
|
|
|
|
Cybersecurity-Market Segmentation and Highlights
|
Segment |
Sub-segment |
|
By Solution Type |
|
|
By Deployment Mode |
|
|
By Organization Size |
|
|
By Service Type |
|
|
By Threat Type |
|
|
By End-Use Industry |
|
Frequently Asked Questions
Table of Contents
- 1. Research Methodology and Assumptions
- 1.1. Definitions
- 1.2. Research Design and Approach
- 1.3. Data Collection Methods
- 1.4. Base Estimates and Calculations
- 1.5. Forecasting Models
- 1.5.1. Key Forecast Factors & Impact Analysis
- 1.6. Secondary Research
- 1.6.1. Open Sources
- 1.6.2. Paid Databases
- 1.6.3. Associations
- 1.7. Primary Research
- 1.7.1. Primary Sources
- 1.7.2. Primary Interviews with Stakeholders across Ecosystem
- 2. Executive Summary
- 2.1. Global Cybersecurity Market Outlook
- 2.1.1. Global Cybersecurity Market Size (Value - USD Bn), and Forecasts, 2021-2035
- 2.1.2. Compounded Annual Growth Rate Analysis
- 2.1.3. Growth Opportunity Analysis
- 2.1.4. Segmental Share Analysis
- 2.1.5. Geographical Share Analysis
- 2.2. Market Analysis and Facts
- 2.3. Supply-Demand Analysis
- 2.4. Competitive Benchmarking
- 2.5. Go-to- Market Strategy
- 2.5.1. Customer/ End-use Industry Assessment
- 2.5.2. Growth Opportunity Data, 2025-2035
- 2.5.2.1. Regional Data
- 2.5.2.2. Country Data
- 2.5.2.3. Segmental Data
- 2.5.3. Identification of Potential Market Spaces
- 2.5.4. GAP Analysis
- 2.5.5. Potential Attractive Price Points
- 2.5.6. Prevailing Market Risks & Challenges
- 2.5.7. Preferred Sales & Marketing Strategies
- 2.5.8. Key Recommendations and Analysis
- 2.5.9. A Way Forward
- 2.1. Global Cybersecurity Market Outlook
- 3. Industry Data and Premium Insights
- 3.1. Global Cybersecurity Industry Overview, 2025
- 3.1.1. Information Technology & Media Ecosystem Analysis
- 3.1.2. Key Trends for Information Technology & Media Industry
- 3.1.3. Regional Distribution for Information Technology & Media Industry
- 3.2. Supplier Customer Data
- 3.3. Source Roadmap and Developments
- 3.4. Trade Analysis
- 3.4.1. Import & Export Analysis, 2025
- 3.4.2. Top Importing Countries
- 3.4.3. Top Exporting Countries
- 3.5. Trump Tariff Impact Analysis
- 3.5.1. Manufacturer
- 3.5.2. Supply Chain
- 3.5.3. End Consumer
- 3.6. Raw Material Analysis
- 3.1. Global Cybersecurity Industry Overview, 2025
- 4. Market Overview
- 4.1. Market Dynamics
- 4.1.1. Drivers
- 4.1.1.1. Increasing Demand for Automated Threat Detection and Response in Complex IT Environments Expansion
- 4.1.2. Restraints
- 4.1.2.1. Rising Security and Compliance Concerns Restricting Adoption of Advanced Cybersecurity Solutions Across Highly Regulated Verticals Globally
- 4.1.1. Drivers
- 4.2. Key Trend Analysis
- 4.3. Regulatory Framework
- 4.3.1. Key Regulations, Norms, and Subsidies, by Key Countries
- 4.3.2. Tariffs and Standards
- 4.3.3. Impact Analysis of Regulations on the Market
- 4.4. Value Chain/ Ecosystem Analysis
- 4.5. Cost Structure Analysis
- 4.5.1. Parameter’s Share for Cost Associated
- 4.5.2. COGP vs COGS
- 4.5.3. Profit Margin Analysis
- 4.6. Pricing Analysis
- 4.6.1. Regional Pricing Analysis
- 4.6.2. Segmental Pricing Trends
- 4.6.3. Factors Influencing Pricing
- 4.7. Porter’s Five Forces Analysis
- 4.8. PESTEL Analysis
- 4.9. Global Cybersecurity Market Demand
- 4.9.1. Historical Market Size - (Value - USD Bn), 2021-2024
- 4.9.2. Current and Future Market Size - (Value - USD Bn), 2025–2035
- 4.9.2.1. Y-o-Y Growth Trends
- 4.9.2.2. Absolute $ Opportunity Assessment
- 4.1. Market Dynamics
- 5. Competition Landscape
- 5.1. Competition structure
- 5.1.1. Fragmented v/s consolidated
- 5.2. Company Share Analysis, 2025
- 5.2.1. Global Company Market Share
- 5.2.2. By Region
- 5.2.2.1. North America
- 5.2.2.2. Europe
- 5.2.2.3. Asia Pacific
- 5.2.2.4. Middle East
- 5.2.2.5. Africa
- 5.2.2.6. South America
- 5.3. Product Comparison Matrix
- 5.3.1. Specifications
- 5.3.2. Market Positioning
- 5.3.3. Pricing
- 5.1. Competition structure
- 6. Global Cybersecurity Market Analysis, by Solution Type
- 6.1. Key Segment Analysis
- 6.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by Solution Type, 2021-2035
- 6.2.1. Network Security Solutions
- 6.2.1.1. Firewalls
- 6.2.1.2. Intrusion Detection & Prevention Systems (IDS/IPS)
- 6.2.1.3. Virtual Private Networks (VPNs)
- 6.2.1.4. Network Access Control (NAC)
- 6.2.1.5. Secure Web Gateways
- 6.2.1.6. Others
- 6.2.2. Endpoint Security Solutions
- 6.2.2.1. Endpoint Detection & Response (EDR)
- 6.2.2.2. Extended Detection & Response (XDR)
- 6.2.2.3. Antivirus/Anti-malware
- 6.2.2.4. Mobile Device Management (MDM)
- 6.2.2.5. Endpoint Privilege Management
- 6.2.2.6. Others
- 6.2.3. Application Security Solutions
- 6.2.3.1. Static Application Security Testing (SAST)
- 6.2.3.2. Dynamic Application Security Testing (DAST)
- 6.2.3.3. Interactive Application Security Testing (IAST)
- 6.2.3.4. Runtime Application Self-Protection (RASP)
- 6.2.3.5. API Security
- 6.2.3.6. Others
- 6.2.4. Cloud Security Solutions
- 6.2.4.1. Cloud Access Security Brokers (CASB)
- 6.2.4.2. Cloud Security Posture Management (CSPM)
- 6.2.4.3. Cloud Workload Protection Platforms (CWPP)
- 6.2.4.4. Container Security
- 6.2.4.5. Multi-Cloud Security Management
- 6.2.4.6. Others
- 6.2.5. Data Security Solutions
- 6.2.5.1. Data Loss Prevention (DLP)
- 6.2.5.2. Database Security
- 6.2.5.3. Data Encryption
- 6.2.5.4. Rights Management
- 6.2.5.5. Data Masking & Tokenization
- 6.2.5.6. Others
- 6.2.6. Identity & Access Management (IAM)
- 6.2.6.1. Privileged Access Management (PAM)
- 6.2.6.2. Single Sign-On (SSO)
- 6.2.6.3. Multi-Factor Authentication (MFA)
- 6.2.6.4. Identity Governance & Administration (IGA)
- 6.2.6.5. Zero Trust Network Access (ZTNA)
- 6.2.6.6. Others
- 6.2.1. Network Security Solutions
- 7. Global Cybersecurity Market Analysis, by Deployment Mode
- 7.1. Key Segment Analysis
- 7.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by Deployment Mode, 2021-2035
- 7.2.1. On-Premises Deployment
- 7.2.2. Cloud-Based Deployment
- 7.2.2.1. Public Cloud
- 7.2.2.2. Private Cloud
- 7.2.2.3. Hybrid Cloud
- 7.2.3. Managed Security Services
- 7.2.4. Software-as-a-Service (SaaS)
- 8. Global Cybersecurity Market Analysis, by Organization Size
- 8.1. Key Segment Analysis
- 8.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, Organization Size, 2021-2035
- 8.2.1. Large Enterprises (>1,000 employees)
- 8.2.2. Medium Enterprises (250-1,000 employees)
- 8.2.3. Small Enterprises (50-249 employees)
- 8.2.4. Small & Medium Businesses (SMBs)
- 8.2.5. Startups (<50 employees)
- 9. Global Cybersecurity Market Analysis, by Service Type
- 9.1. Key Segment Analysis
- 9.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by Service Type, 2021-2035
- 9.2.1. Professional Services
- 9.2.1.1. Consulting Services
- 9.2.1.2. Design & Integration
- 9.2.1.3. Training & Education
- 9.2.1.4. Others
- 9.2.2. Managed Security Services
- 9.2.2.1. Security Monitoring
- 9.2.2.2. Incident Response
- 9.2.2.3. Vulnerability Management
- 9.2.2.4. Compliance Management
- 9.2.2.5. Others
- 9.2.3. Support & Maintenance Services
- 9.2.1. Professional Services
- 10. Global Cybersecurity Market Analysis, by Threat Type
- 10.1. Key Segment Analysis
- 10.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by Threat Type, 2021-2035
- 10.2.1. Malware Protection
- 10.2.2. Ransomware Protection
- 10.2.3. Phishing Protection
- 10.2.4. Advanced Persistent Threats (APTs)
- 10.2.5. Insider Threats
- 10.2.6. DDoS Protection
- 10.2.7. Zero-Day Exploits
- 10.2.8. Social Engineering Attacks
- 10.2.9. Others
- 11. Global Cybersecurity Market Analysis, by End-Use Industry
- 11.1. Key Segment Analysis
- 11.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by End-Use Industry, 2021-2035
- 11.2.1. Banking, Financial Services & Insurance (BFSI)
- 11.2.1.1. Online Banking Security
- 11.2.1.2. Payment Card Security
- 11.2.1.3. Trading Platform Security
- 11.2.1.4. Insurance Fraud Prevention
- 11.2.1.5. Mobile Banking Protection
- 11.2.1.6. Others
- 11.2.2. Healthcare & Life Sciences
- 11.2.2.1. Electronic Health Records (EHR) Protection
- 11.2.2.2. Medical Device Security
- 11.2.2.3. Telemedicine Security
- 11.2.2.4. Clinical Trial Data Protection
- 11.2.2.5. Pharmaceutical Manufacturing
- 11.2.2.6. Healthcare IoT Security
- 11.2.2.7. Others
- 11.2.3. Government & Defense
- 11.2.3.1. Critical Infrastructure Protection
- 11.2.3.2. National Security
- 11.2.3.3. Citizen Services Security
- 11.2.3.4. Military Communications
- 11.2.3.5. Border Security
- 11.2.3.6. Cybersecurity Training
- 11.2.3.7. Others
- 11.2.4. Manufacturing & Industrial
- 11.2.4.1. Industrial Control Systems (ICS) Security
- 11.2.4.2. Supply Chain Security
- 11.2.4.3. Smart Manufacturing
- 11.2.4.4. Intellectual Property Protection
- 11.2.4.5. Quality Control Systems
- 11.2.4.6. Predictive Maintenance Security
- 11.2.4.7. Others
- 11.2.5. Information Technology & Telecommunications
- 11.2.5.1. Network Infrastructure Security
- 11.2.5.2. Data Center Security
- 11.2.5.3. Software Development Security
- 11.2.5.4. Cloud Service Provider Security
- 11.2.5.5. Telecommunications Fraud Prevention
- 11.2.5.6. IoT Platform Security
- 11.2.5.7. Others
- 11.2.6. Retail & E-commerce
- 11.2.7. Energy & Utilities
- 11.2.8. Education & Research
- 11.2.9. Transportation & Logistics
- 11.2.10. Media & Entertainment
- 11.2.11. Real Estate & Construction
- 11.2.12. Agriculture & Food
- 11.2.13. Others
- 11.2.1. Banking, Financial Services & Insurance (BFSI)
- 12. Global Cybersecurity Market Analysis and Forecasts, by Region
- 12.1. Key Findings
- 12.2. Global Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, by Region, 2021-2035
- 12.2.1. North America
- 12.2.2. Europe
- 12.2.3. Asia Pacific
- 12.2.4. Middle East
- 12.2.5. Africa
- 12.2.6. South America
- 13. North America Cybersecurity Market Analysis
- 13.1. Key Segment Analysis
- 13.2. Regional Snapshot
- 13.3. North America Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 13.3.1. Solution Type
- 13.3.2. Deployment Mode
- 13.3.3. Organization Size
- 13.3.4. Service Type
- 13.3.5. Threat Type
- 13.3.6. End-Use Industry
- 13.3.7. Country
- 13.3.7.1. USA
- 13.3.7.2. Canada
- 13.3.7.3. Mexico
- 13.4. USA Cybersecurity Market
- 13.4.1. Country Segmental Analysis
- 13.4.2. Solution Type
- 13.4.3. Deployment Mode
- 13.4.4. Organization Size
- 13.4.5. Service Type
- 13.4.6. Threat Type
- 13.4.7. End-Use Industry
- 13.5. Canada Cybersecurity Market
- 13.5.1. Country Segmental Analysis
- 13.5.2. Solution Type
- 13.5.3. Deployment Mode
- 13.5.4. Organization Size
- 13.5.5. Service Type
- 13.5.6. Threat Type
- 13.5.7. End-Use Industry
- 13.6. Mexico Cybersecurity Market
- 13.6.1. Country Segmental Analysis
- 13.6.2. Solution Type
- 13.6.3. Deployment Mode
- 13.6.4. Organization Size
- 13.6.5. Service Type
- 13.6.6. Threat Type
- 13.6.7. End-Use Industry
- 14. Europe Cybersecurity Market Analysis
- 14.1. Key Segment Analysis
- 14.2. Regional Snapshot
- 14.3. Europe Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 14.3.1. Solution Type
- 14.3.2. Deployment Mode
- 14.3.3. Organization Size
- 14.3.4. Service Type
- 14.3.5. Threat Type
- 14.3.6. End-Use Industry
- 14.3.7. Country
- 14.3.7.1. Germany
- 14.3.7.2. United Kingdom
- 14.3.7.3. France
- 14.3.7.4. Italy
- 14.3.7.5. Spain
- 14.3.7.6. Netherlands
- 14.3.7.7. Nordic Countries
- 14.3.7.8. Poland
- 14.3.7.9. Russia & CIS
- 14.3.7.10. Rest of Europe
- 14.4. Germany Cybersecurity Market
- 14.4.1. Country Segmental Analysis
- 14.4.2. Solution Type
- 14.4.3. Deployment Mode
- 14.4.4. Organization Size
- 14.4.5. Service Type
- 14.4.6. Threat Type
- 14.4.7. End-Use Industry
- 14.5. United Kingdom Cybersecurity Market
- 14.5.1. Country Segmental Analysis
- 14.5.2. Solution Type
- 14.5.3. Deployment Mode
- 14.5.4. Organization Size
- 14.5.5. Service Type
- 14.5.6. Threat Type
- 14.5.7. End-Use Industry
- 14.6. France Cybersecurity Market
- 14.6.1. Country Segmental Analysis
- 14.6.2. Solution Type
- 14.6.3. Deployment Mode
- 14.6.4. Organization Size
- 14.6.5. Service Type
- 14.6.6. Threat Type
- 14.6.7. End-Use Industry
- 14.7. Italy Cybersecurity Market
- 14.7.1. Country Segmental Analysis
- 14.7.2. Solution Type
- 14.7.3. Deployment Mode
- 14.7.4. Organization Size
- 14.7.5. Service Type
- 14.7.6. Threat Type
- 14.7.7. End-Use Industry
- 14.8. Spain Cybersecurity Market
- 14.8.1. Country Segmental Analysis
- 14.8.2. Solution Type
- 14.8.3. Deployment Mode
- 14.8.4. Organization Size
- 14.8.5. Service Type
- 14.8.6. Threat Type
- 14.8.7. End-Use Industry
- 14.9. Netherlands Cybersecurity Market
- 14.9.1. Country Segmental Analysis
- 14.9.2. Solution Type
- 14.9.3. Deployment Mode
- 14.9.4. Organization Size
- 14.9.5. Service Type
- 14.9.6. Threat Type
- 14.9.7. End-Use Industry
- 14.10. Nordic Countries Cybersecurity Market
- 14.10.1. Country Segmental Analysis
- 14.10.2. Solution Type
- 14.10.3. Deployment Mode
- 14.10.4. Organization Size
- 14.10.5. Service Type
- 14.10.6. Threat Type
- 14.10.7. End-Use Industry
- 14.11. Poland Cybersecurity Market
- 14.11.1. Country Segmental Analysis
- 14.11.2. Solution Type
- 14.11.3. Deployment Mode
- 14.11.4. Organization Size
- 14.11.5. Service Type
- 14.11.6. Threat Type
- 14.11.7. End-Use Industry
- 14.12. Russia & CIS Cybersecurity Market
- 14.12.1. Country Segmental Analysis
- 14.12.2. Solution Type
- 14.12.3. Deployment Mode
- 14.12.4. Organization Size
- 14.12.5. Service Type
- 14.12.6. Threat Type
- 14.12.7. End-Use Industry
- 14.13. Rest of Europe Cybersecurity Market
- 14.13.1. Country Segmental Analysis
- 14.13.2. Solution Type
- 14.13.3. Deployment Mode
- 14.13.4. Organization Size
- 14.13.5. Service Type
- 14.13.6. Threat Type
- 14.13.7. End-Use Industry
- 15. Asia Pacific Cybersecurity Market Analysis
- 15.1. Key Segment Analysis
- 15.2. Regional Snapshot
- 15.3. East Asia Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 15.3.1. Solution Type
- 15.3.2. Deployment Mode
- 15.3.3. Organization Size
- 15.3.4. Service Type
- 15.3.5. Threat Type
- 15.3.6. End-Use Industry
- 15.3.7. Country
- 15.3.7.1. China
- 15.3.7.2. India
- 15.3.7.3. Japan
- 15.3.7.4. South Korea
- 15.3.7.5. Australia and New Zealand
- 15.3.7.6. Indonesia
- 15.3.7.7. Malaysia
- 15.3.7.8. Thailand
- 15.3.7.9. Vietnam
- 15.3.7.10. Rest of Asia-Pacific
- 15.4. China Cybersecurity Market
- 15.4.1. Country Segmental Analysis
- 15.4.2. Solution Type
- 15.4.3. Deployment Mode
- 15.4.4. Organization Size
- 15.4.5. Service Type
- 15.4.6. Threat Type
- 15.4.7. End-Use Industry
- 15.5. India Cybersecurity Market
- 15.5.1. Country Segmental Analysis
- 15.5.2. Solution Type
- 15.5.3. Deployment Mode
- 15.5.4. Organization Size
- 15.5.5. Service Type
- 15.5.6. Threat Type
- 15.5.7. End-Use Industry
- 15.6. Japan Cybersecurity Market
- 15.6.1. Country Segmental Analysis
- 15.6.2. Solution Type
- 15.6.3. Deployment Mode
- 15.6.4. Organization Size
- 15.6.5. Service Type
- 15.6.6. Threat Type
- 15.6.7. End-Use Industry
- 15.7. South Korea Cybersecurity Market
- 15.7.1. Country Segmental Analysis
- 15.7.2. Solution Type
- 15.7.3. Deployment Mode
- 15.7.4. Organization Size
- 15.7.5. Service Type
- 15.7.6. Threat Type
- 15.7.7. End-Use Industry
- 15.8. Australia and New Zealand Cybersecurity Market
- 15.8.1. Country Segmental Analysis
- 15.8.2. Solution Type
- 15.8.3. Deployment Mode
- 15.8.4. Organization Size
- 15.8.5. Service Type
- 15.8.6. Threat Type
- 15.8.7. End-Use Industry
- 15.9. Indonesia Cybersecurity Market
- 15.9.1. Country Segmental Analysis
- 15.9.2. Solution Type
- 15.9.3. Deployment Mode
- 15.9.4. Organization Size
- 15.9.5. Service Type
- 15.9.6. Threat Type
- 15.9.7. End-Use Industry
- 15.10. Malaysia Cybersecurity Market
- 15.10.1. Country Segmental Analysis
- 15.10.2. Solution Type
- 15.10.3. Deployment Mode
- 15.10.4. Organization Size
- 15.10.5. Service Type
- 15.10.6. Threat Type
- 15.10.7. End-Use Industry
- 15.11. Thailand Cybersecurity Market
- 15.11.1. Country Segmental Analysis
- 15.11.2. Solution Type
- 15.11.3. Deployment Mode
- 15.11.4. Organization Size
- 15.11.5. Service Type
- 15.11.6. Threat Type
- 15.11.7. End-Use Industry
- 15.12. Vietnam Cybersecurity Market
- 15.12.1. Country Segmental Analysis
- 15.12.2. Solution Type
- 15.12.3. Deployment Mode
- 15.12.4. Organization Size
- 15.12.5. Service Type
- 15.12.6. Threat Type
- 15.12.7. End-Use Industry
- 15.13. Rest of Asia Pacific Cybersecurity Market
- 15.13.1. Country Segmental Analysis
- 15.13.2. Solution Type
- 15.13.3. Deployment Mode
- 15.13.4. Organization Size
- 15.13.5. Service Type
- 15.13.6. Threat Type
- 15.13.7. End-Use Industry
- 16. Middle East Cybersecurity Market Analysis
- 16.1. Key Segment Analysis
- 16.2. Regional Snapshot
- 16.3. Middle East Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 16.3.1. Solution Type
- 16.3.2. Deployment Mode
- 16.3.3. Organization Size
- 16.3.4. Service Type
- 16.3.5. Threat Type
- 16.3.6. End-Use Industry
- 16.3.7. Country
- 16.3.7.1. Turkey
- 16.3.7.2. UAE
- 16.3.7.3. Saudi Arabia
- 16.3.7.4. Israel
- 16.3.7.5. Rest of Middle East
- 16.4. Turkey Cybersecurity Market
- 16.4.1. Country Segmental Analysis
- 16.4.2. Solution Type
- 16.4.3. Deployment Mode
- 16.4.4. Organization Size
- 16.4.5. Service Type
- 16.4.6. Threat Type
- 16.4.7. End-Use Industry
- 16.5. UAE Cybersecurity Market
- 16.5.1. Country Segmental Analysis
- 16.5.2. Solution Type
- 16.5.3. Deployment Mode
- 16.5.4. Organization Size
- 16.5.5. Service Type
- 16.5.6. Threat Type
- 16.5.7. End-Use Industry
- 16.6. Saudi Arabia Cybersecurity Market
- 16.6.1. Country Segmental Analysis
- 16.6.2. Solution Type
- 16.6.3. Deployment Mode
- 16.6.4. Organization Size
- 16.6.5. Service Type
- 16.6.6. Threat Type
- 16.6.7. End-Use Industry
- 16.7. Israel Cybersecurity Market
- 16.7.1. Country Segmental Analysis
- 16.7.2. Solution Type
- 16.7.3. Deployment Mode
- 16.7.4. Organization Size
- 16.7.5. Service Type
- 16.7.6. Threat Type
- 16.7.7. End-Use Industry
- 16.8. Rest of Middle East Cybersecurity Market
- 16.8.1. Country Segmental Analysis
- 16.8.2. Solution Type
- 16.8.3. Deployment Mode
- 16.8.4. Organization Size
- 16.8.5. Service Type
- 16.8.6. Threat Type
- 16.8.7. End-Use Industry
- 17. Africa Cybersecurity Market Analysis
- 17.1. Key Segment Analysis
- 17.2. Regional Snapshot
- 17.3. Africa Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 17.3.1. Solution Type
- 17.3.2. Deployment Mode
- 17.3.3. Organization Size
- 17.3.4. Service Type
- 17.3.5. Threat Type
- 17.3.6. End-Use Industry
- 17.3.7. Country
- 17.3.7.1. South Africa
- 17.3.7.2. Egypt
- 17.3.7.3. Nigeria
- 17.3.7.4. Algeria
- 17.3.7.5. Rest of Africa
- 17.4. South Africa Cybersecurity Market
- 17.4.1. Country Segmental Analysis
- 17.4.2. Solution Type
- 17.4.3. Deployment Mode
- 17.4.4. Organization Size
- 17.4.5. Service Type
- 17.4.6. Threat Type
- 17.4.7. End-Use Industry
- 17.5. Egypt Cybersecurity Market
- 17.5.1. Country Segmental Analysis
- 17.5.2. Solution Type
- 17.5.3. Deployment Mode
- 17.5.4. Organization Size
- 17.5.5. Service Type
- 17.5.6. Threat Type
- 17.5.7. End-Use Industry
- 17.6. Nigeria Cybersecurity Market
- 17.6.1. Country Segmental Analysis
- 17.6.2. Solution Type
- 17.6.3. Deployment Mode
- 17.6.4. Organization Size
- 17.6.5. Service Type
- 17.6.6. Threat Type
- 17.6.7. End-Use Industry
- 17.7. Algeria Cybersecurity Market
- 17.7.1. Country Segmental Analysis
- 17.7.2. Solution Type
- 17.7.3. Deployment Mode
- 17.7.4. Organization Size
- 17.7.5. Service Type
- 17.7.6. Threat Type
- 17.7.7. End-Use Industry
- 17.8. Rest of Africa Cybersecurity Market
- 17.8.1. Country Segmental Analysis
- 17.8.2. Solution Type
- 17.8.3. Deployment Mode
- 17.8.4. Organization Size
- 17.8.5. Service Type
- 17.8.6. Threat Type
- 17.8.7. End-Use Industry
- 18. South America Cybersecurity Market Analysis
- 18.1. Key Segment Analysis
- 18.2. Regional Snapshot
- 18.3. Central and South Africa Cybersecurity Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 18.3.1. Solution Type
- 18.3.2. Deployment Mode
- 18.3.3. Organization Size
- 18.3.4. Service Type
- 18.3.5. Threat Type
- 18.3.6. End-Use Industry
- 18.3.7. Country
- 18.3.7.1. Brazil
- 18.3.7.2. Argentina
- 18.3.7.3. Rest of South America
- 18.4. Brazil Cybersecurity Market
- 18.4.1. Country Segmental Analysis
- 18.4.2. Solution Type
- 18.4.3. Deployment Mode
- 18.4.4. Organization Size
- 18.4.5. Service Type
- 18.4.6. Threat Type
- 18.4.7. End-Use Industry
- 18.5. Argentina Cybersecurity Market
- 18.5.1. Country Segmental Analysis
- 18.5.2. Solution Type
- 18.5.3. Deployment Mode
- 18.5.4. Organization Size
- 18.5.5. Service Type
- 18.5.6. Threat Type
- 18.5.7. End-Use Industry
- 18.6. Rest of South America Cybersecurity Market
- 18.6.1. Country Segmental Analysis
- 18.6.2. Solution Type
- 18.6.3. Deployment Mode
- 18.6.4. Organization Size
- 18.6.5. Service Type
- 18.6.6. Threat Type
- 18.6.7. End-Use Industry
- 19. Key Players/ Company Profile
- 19.1. Amazon Web Services (AWS)
- 19.1.1. Company Details/ Overview
- 19.1.2. Company Financials
- 19.1.3. Key Customers and Competitors
- 19.1.4. Business/ Industry Portfolio
- 19.1.5. Product Portfolio/ Specification Details
- 19.1.6. Pricing Data
- 19.1.7. Strategic Overview
- 19.1.8. Recent Developments
- 19.2. BAE Systems Plc
- 19.3. Check Point Software Technologies
- 19.4. Cisco Systems, Inc.
- 19.5. CrowdStrike Holdings
- 19.6. Darktrace
- 19.7. ESET, spol. s r.o.
- 19.8. F5 Networks, Inc.
- 19.9. Fortinet, Inc.
- 19.10. IBM Corporation
- 19.11. Juniper Networks, Inc.
- 19.12. McAfee Corp.
- 19.13. Microsoft Corporation
- 19.14. Okta, Inc.
- 19.15. Oracle Corporation
- 19.16. Palo Alto Networks, Inc.
- 19.17. SentinelOne
- 19.18. Splunk Inc.
- 19.19. Trend Micro Incorporated
- 19.20. Zscaler, Inc.
- 19.21. Others Key Players
- 19.1. Amazon Web Services (AWS)
Note* - This is just tentative list of players. While providing the report, we will cover more number of players based on their revenue and share for each geography
Research Design
Our research design integrates both demand-side and supply-side analysis through a balanced combination of primary and secondary research methodologies. By utilizing both bottom-up and top-down approaches alongside rigorous data triangulation methods, we deliver robust market intelligence that supports strategic decision-making.
MarketGenics' comprehensive research design framework ensures the delivery of accurate, reliable, and actionable market intelligence. Through the integration of multiple research approaches, rigorous validation processes, and expert analysis, we provide our clients with the insights needed to make informed strategic decisions and capitalize on market opportunities.
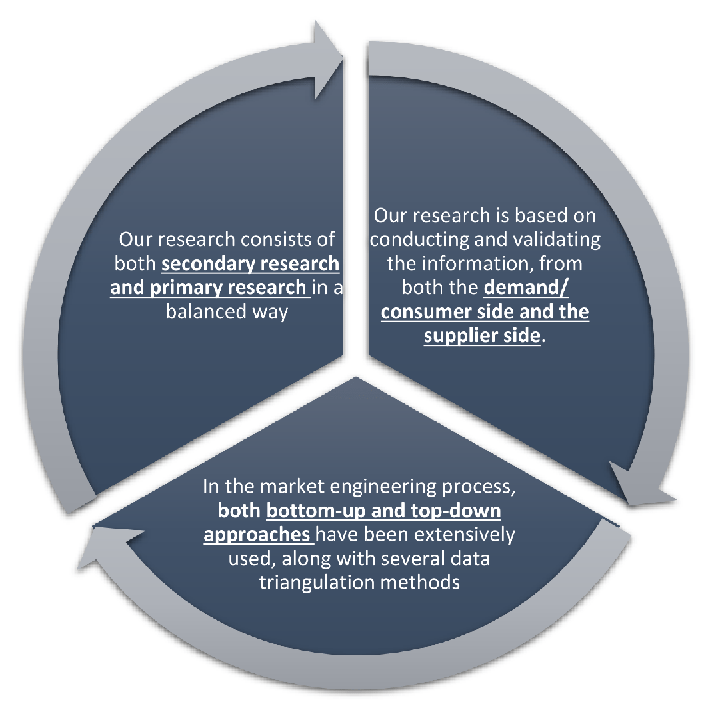
MarketGenics leverages a dedicated industry panel of experts and a comprehensive suite of paid databases to effectively collect, consolidate, and analyze market intelligence.
Our approach has consistently proven to be reliable and effective in generating accurate market insights, identifying key industry trends, and uncovering emerging business opportunities.
Through both primary and secondary research, we capture and analyze critical company-level data such as manufacturing footprints, including technical centers, R&D facilities, sales offices, and headquarters.
Our expert panel further enhances our ability to estimate market size for specific brands based on validated field-level intelligence.
Our data mining techniques incorporate both parametric and non-parametric methods, allowing for structured data collection, sorting, processing, and cleaning.
Demand projections are derived from large-scale data sets analyzed through proprietary algorithms, culminating in robust and reliable market sizing.
Research Approach
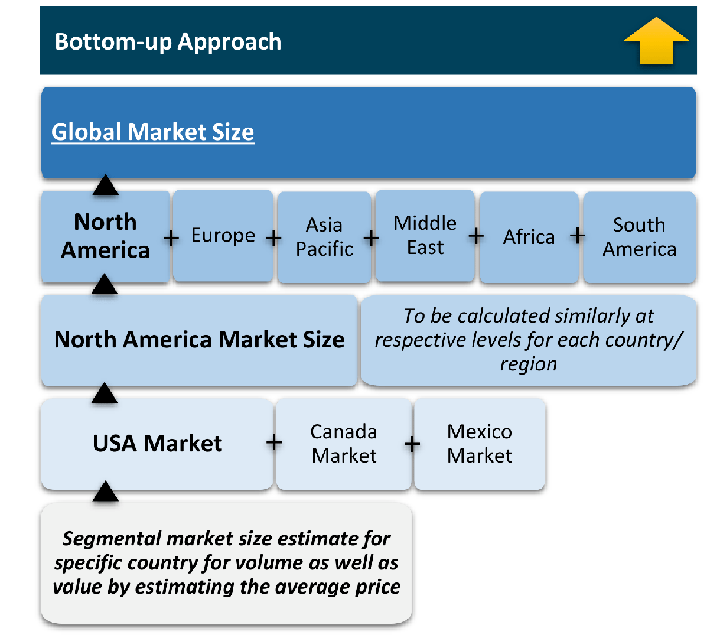
The bottom-up approach builds market estimates by starting with the smallest addressable market units and systematically aggregating them to create comprehensive market size projections.
This method begins with specific, granular data points and builds upward to create the complete market landscape.
Customer Analysis → Segmental Analysis → Geographical Analysis
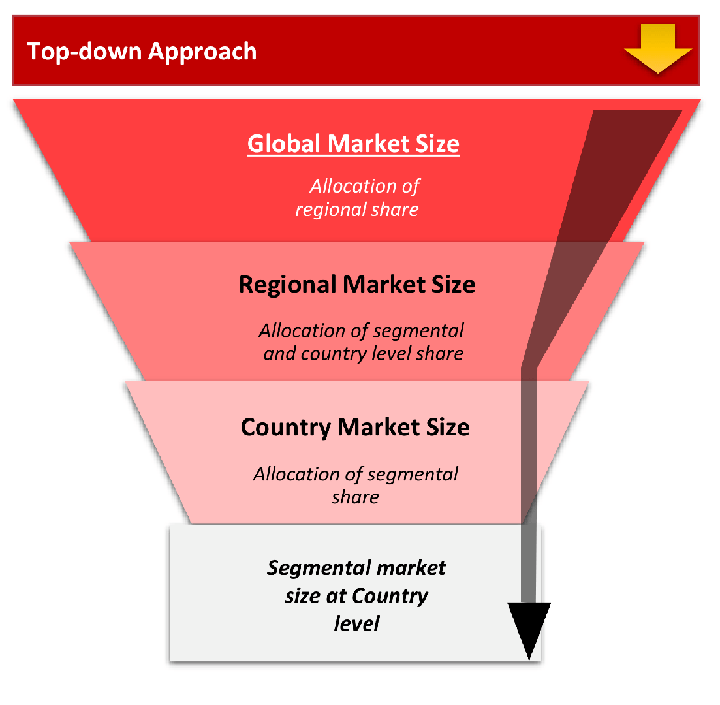
The top-down approach starts with the broadest possible market data and systematically narrows it down through a series of filters and assumptions to arrive at specific market segments or opportunities.
This method begins with the big picture and works downward to increasingly specific market slices.
TAM → SAM → SOM
Research Methods
Desk / Secondary Research
While analysing the market, we extensively study secondary sources, directories, and databases to identify and collect information useful for this technical, market-oriented, and commercial report. Secondary sources that we utilize are not only the public sources, but it is a combination of Open Source, Associations, Paid Databases, MG Repository & Knowledgebase, and others.
- Company websites, annual reports, financial reports, broker reports, and investor presentations
- National government documents, statistical databases and reports
- News articles, press releases and web-casts specific to the companies operating in the market, Magazines, reports, and others
- We gather information from commercial data sources for deriving company specific data such as segmental revenue, share for geography, product revenue, and others
- Internal and external proprietary databases (industry-specific), relevant patent, and regulatory databases
- Governing Bodies, Government Organizations
- Relevant Authorities, Country-specific Associations for Industries
We also employ the model mapping approach to estimate the product level market data through the players' product portfolio
Primary Research
Primary research/ interviews is vital in analyzing the market. Most of the cases involves paid primary interviews. Primary sources include primary interviews through e-mail interactions, telephonic interviews, surveys as well as face-to-face interviews with the different stakeholders across the value chain including several industry experts.
| Type of Respondents | Number of Primaries |
|---|---|
| Tier 2/3 Suppliers | ~20 |
| Tier 1 Suppliers | ~25 |
| End-users | ~25 |
| Industry Expert/ Panel/ Consultant | ~30 |
| Total | ~100 |
MG Knowledgebase
• Repository of industry blog, newsletter and case studies
• Online platform covering detailed market reports, and company profiles
Forecasting Factors and Models
Forecasting Factors
- Historical Trends – Past market patterns, cycles, and major events that shaped how markets behave over time. Understanding past trends helps predict future behavior.
- Industry Factors – Specific characteristics of the industry like structure, regulations, and innovation cycles that affect market dynamics.
- Macroeconomic Factors – Economic conditions like GDP growth, inflation, and employment rates that affect how much money people have to spend.
- Demographic Factors – Population characteristics like age, income, and location that determine who can buy your product.
- Technology Factors – How quickly people adopt new technology and how much technology infrastructure exists.
- Regulatory Factors – Government rules, laws, and policies that can help or restrict market growth.
- Competitive Factors – Analyzing competition structure such as degree of competition and bargaining power of buyers and suppliers.
Forecasting Models / Techniques
Multiple Regression Analysis
- Identify and quantify factors that drive market changes
- Statistical modeling to establish relationships between market drivers and outcomes
Time Series Analysis – Seasonal Patterns
- Understand regular cyclical patterns in market demand
- Advanced statistical techniques to separate trend, seasonal, and irregular components
Time Series Analysis – Trend Analysis
- Identify underlying market growth patterns and momentum
- Statistical analysis of historical data to project future trends
Expert Opinion – Expert Interviews
- Gather deep industry insights and contextual understanding
- In-depth interviews with key industry stakeholders
Multi-Scenario Development
- Prepare for uncertainty by modeling different possible futures
- Creating optimistic, pessimistic, and most likely scenarios
Time Series Analysis – Moving Averages
- Sophisticated forecasting for complex time series data
- Auto-regressive integrated moving average models with seasonal components
Econometric Models
- Apply economic theory to market forecasting
- Sophisticated economic models that account for market interactions
Expert Opinion – Delphi Method
- Harness collective wisdom of industry experts
- Structured, multi-round expert consultation process
Monte Carlo Simulation
- Quantify uncertainty and probability distributions
- Thousands of simulations with varying input parameters
Research Analysis
Our research framework is built upon the fundamental principle of validating market intelligence from both demand and supply perspectives. This dual-sided approach ensures comprehensive market understanding and reduces the risk of single-source bias.
Demand-Side Analysis: We understand end-user/application behavior, preferences, and market needs along with the penetration of the product for specific application.
Supply-Side Analysis: We estimate overall market revenue, analyze the segmental share along with industry capacity, competitive landscape, and market structure.
Validation & Evaluation
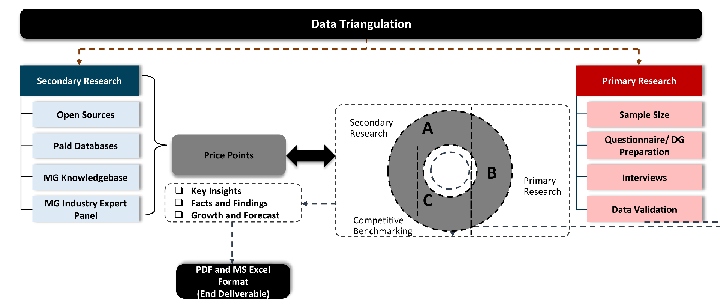
Data triangulation is a validation technique that uses multiple methods, sources, or perspectives to examine the same research question, thereby increasing the credibility and reliability of research findings. In market research, triangulation serves as a quality assurance mechanism that helps identify and minimize bias, validate assumptions, and ensure accuracy in market estimates.
- Data Source Triangulation – Using multiple data sources to examine the same phenomenon
- Methodological Triangulation – Using multiple research methods to study the same research question
- Investigator Triangulation – Using multiple researchers or analysts to examine the same data
- Theoretical Triangulation – Using multiple theoretical perspectives to interpret the same data
Custom Market Research Services
We will customise the research for you, in case the report listed above does not meet your requirements.
Get 10% Free Customisation