Email Encryption Market Size, Share & Trends Analysis Report by Offering (Solutions, Services), Deployment Mode, Encryption Type, Enterprise Size, Security Type, Application, End User, Industry Vertical, and Geography (North America, Europe, Asia Pacific, Middle East, Africa, and South America) – Global Industry Data, Trends, and Forecasts, 2025–2035
|
Market Structure & Evolution |
|
|
Segmental Data Insights |
|
|
Demand Trends |
|
|
Competitive Landscape |
|
|
Strategic Development |
|
|
Future Outlook & Opportunities |
|
Email Encryption Market Size, Share, And Growth
The global email encryption market is experiencing robust growth, with its estimated value of USD 7.5 billion in the year 2025 and USD 35.3 billion by the period 2035, registering a CAGR of 16.8%. North America leads the market with market share of 45% with USD 3.3 billion revenue. The global email encryption market is thriving as a result of the increasing need for protecting sensitive data, complying with rigorous data protection policies, along with the overall convergence of cyber insecurity. As businesses are sending even greater volumes of sensitive communications, email encryption solutions have quickly become a fundamental method for protecting data integrity, confidentiality, and authenticity, internally and externally.

Ava Mitchell, who holds the position of Chief Security Officer at CyberFort Systems, stated, "As we build our Email Encryption platform, we have the focus on making threat protection smarter, faster, and more resilient offering automation, compliance, and adaptive security frameworks to help organizations stay one step ahead of ever-evolving cyber threats and regulatory challenges, particularly in this ever-increasing digital world.
Additionally, the advent of cloud-based communication platforms, remote work, and increased use of mobile devices accelerated email encryption's progression. For example, in June, 2025, Google expanded its security features in Gmail by rolling out new encryption protocols and AI detection processes to accelerate the secure email traffic experience and enhance adherence to data privacy standards around the world.
The email encryption market is experiencing rapid growth driven in part by the increasing prevalence of phishing attacks, business email compromises (BEC), and by regulatory frameworks like GDPR, HIPAA, and CCPA. Firm in high GDPR-sensitive industries like finance, healthcare, legal, and government have emerged as the primary adopters of this technology as they are drawn to end-to-end email encryption solutions in order to effectively secure communications while curtailing risk.
Furthermore, there are adjacent opportunities in the international email encryption market in secure file transfer, identity and access management (IAM), data loss prevention (DLP), cloud email security, and zero-trust security. These related technologies increase the overall value of email encryption through improved endpoint security, user authentication, and policy enforcement around enterprise communications.
Email Encryption Market Dynamics and Trends

Driver: Increasing Demand for Automated Email Encryption in Evolving Digital Ecosystems Expansion
- While cyber threats grow in frequency and sophistication, and its underlying infrastructures grow complex, you will find organizations looking for modern, automated options for protecting email data. These modern solutions enable organizations to secure communications, to manage burden on personnel, and to ensure sensitive information is protected throughout distributed channels.
- In March 2025, Proofpoint launched its AI-enabled email security suite that includes real-time encryption, automated policy enforcement, and adaptive threat detection helping organizations detect and respond to phishing, data loss, and compliance threats in an effective manner. This shows a growing demand for intelligent, scalable security solutions that fit a modern style of communication.
- Additionally, the growing use of cloud services, remote work, and IoT-enabled devices factored into a greater reliance on overarching email encryption strategies. Organizations are utilizing unified platforms that combine encryption, compliance management, and policy-based controls to provide end-to-end protection and regulatory compliance across hybrid and multi-cloud environments.
Restraint: Operational Complexity and User Resistance Limiting Broader Adoption of Email Encryption Solutions
- Although email encryption technologies are vital for protecting sensitive communications, their overall proliferation is impeded by usability factors, integration factors and a lack of consistent compliance across industries. In industries with less mature IT infrastructures, users tend to see encryption as either disruptive to workflow or too technical, contributing to lower adoption rates.
- A notable example, in January of 2025, Mimecast conducted a survey which revealed that more than 40% of enterprises cited user resistance and inadequate end-user training as the most significant barriers to implementing full-scale email encryption, even while acknowledging encryption’s value for security.
- Regulatory variations and regional encryption standards also complicate organization-wide implementation, specifically for organizations operating in multiple jurisdictions. Therefore, these compounded factors add to slower adoption rates, especially among small and mid-sized businesses (SMBs) and in industries where communication ease is valued over security controls.
Opportunity: Expanding Opportunities Through AI-Powered Email Encryption Solutions Enhancing Threat Prediction and Incident Response
- The incorporation of artificial intelligence into email encryption services is creating a new array of options through predictive threat analysis, anomaly detection in real-time, and intelligent incident response. AI tools can detect an emerging attack pattern; automate encryption protocols based on the sensitivity of the content and streamline policy enforcement for better security and efficiency in operations.
- A worthy example was in early February in 2025, when CrowdStrike added AI functionality within the Falcon platform, such as behavioral threat modeling, and automated threat response capabilities. These features greatly relieved security teams of workflow and improved proactive security defense across enterprise email environments.
- This is the evolution of a movement away from re-active encryption to coding intelligent, business adaptive security processes. As AI functionality matures, organizations will increasingly be able to shift from perimeter-based protections to autonomous and insight driven frameworks that promote data protection, while also engaging employees.
Key Trend: Shift Toward Cloud-Based Email Encryption Platforms Enabling Agility and Centralized Policy Management
- Cloud-native solutions are a growing trend in the email encryption market as organizations seek agility, centralized control, and easy integration with cloud productivity suites. It is observed that hybrid workforces and distributed teams are the new normal with employees working from anywhere, thereby driving the need for cloud-based encryption solutions for easy scalability, reduction in on-premises deployment time, and real-time policy enforcement across users and endpoints.
- Notably, in August of 2024, Zix (OpenText) announced an updated Secure Cloud Email Suite that now includes AI-powered encryption triggers, Microsoft 365 integrations, and centralized compliance dashboards - showcasing the focus on unified cloud-centric policy-driven security in this market.
- These trends indicate a need for unified "always-on" email protection, that is not reliant on gateway-like mechanisms. Furthermore, cloud-native encryption solutions are now required capabilities for organizations to protect sensitive communications, adhere to compliance regulations, and provide business continuity in today's hybrid IT environments.
Email Encryption Market Analysis and Segmental Data

Services Segment Maintain Dominance in Global Email Encryption Market amid Growing Regulatory Compliance Demands
- The global email encryption market remains led by service-based solutions due to pressures associated with increased regulatory compliance and the need for outsourcing compliance to experts. Enterprises that operate in regulated industries increasingly rely on encryption services to help them meet the increasing number of and complex requirements of GDPR, HIPAA, CCPA regulations, and more.
- During 2025, service providers like Proofpoint and Zix updated their solutions to offer AI-based threat detection systems, enforcement of policies in automated capacity, and real-time auditing of compliance to help meet faster response times to changes in data protection laws. While hybrid work continues and the regulatory environment increases in complexity, organizations are placing priority on scalable, fully-managed encryption services that promise secure communication, ease of integration and auditing for compliance purposes, thereby continuing to make the service segment a pillar of organizations email security strategies.
North America Leads the Email Encryption Market amid Stringent Data Protection Regulations
- North America remains a leader in the global email encryption market partly due to tight regulations concerning data protection, a rising number of cyber threats, and a pervasive digital environment in verticals such as health care, finance, and government. There are laws such as HIPAA, CCPA, and FISMA that have accelerated the transition to advanced forms of email encryption for compliant and secure communication.
- In 2025, companies like Microsoft and Proofpoint enhanced their platforms to include AI-based encryption, automated policy enforcement, and integrated identity management to improve regulatory compliance for data protection with biometric verification and messaging cryptography models for distributed workforces.
- Government-led and supported public-private cyber security efforts will propel North America innovation for email security, putting the jurisdiction at the forefront of the vertical space. As regulation embraces a tighter form for data protection, North America is in a position to lead in compliance, privacy, and business operational resiliency as it relates to the Email Encryption market.
Email-Encryption-Market Ecosystem
The global market for email encryption is moderately fragmented, containing selected Tier 1 players, such as Microsoft, Cisco Systems, and Broadcom (Symantec), in addition to Tier 2 players, like Proofpoint, Mimecast, and Trend Micro. And finally, smaller Tier 3 niche providers, like Virtru, Paubox, and Trustifi. The buyer concentration is moderate, changing as enterprise demand increase across sectors. While supplier concentration is low because encryption solutions are widely available in various market segments. Competitive factors in the market are compliance, integration capabilities, as well as innovation.

Recent Development and Strategic Overview:
- In February 2025, Proofpoint, Inc. has expanded its suite of email encryption capabilities by introducing a zero-trust email gateway that combines advanced data loss prevention (DLP) and machine learning-based anomaly detection. This enables organizations to impose granular encryption policies, receive real-time alerts when individuals try to exfiltrate data inappropriately, and ensure that communication can remain secure even in hybrid work environments - ultimately addressing challenges related to compliance and insider threats.
- In April 2025, Entrust Corporation has launched a cloud-native email encryption service that includes post-quantum cryptography support and automated key lifecycle management in a solution focused on regulated industries like finance and healthcare. The solution provides protection from emerging threats related to cryptography, additional simplification of certificate management, and a regulatory edge in areas with changing privacy laws.
Report Scope
|
Attribute |
Detail |
|
Market Size in 2025 |
USD 7.5 Bn |
|
Market Forecast Value in 2035 |
USD 35.3 Bn |
|
Growth Rate (CAGR) |
16.8% |
|
Forecast Period |
2025 – 2035 |
|
Historical Data Available for |
2021 – 2024 |
|
Market Size Units |
USD Bn for Value |
|
Report Format |
Electronic (PDF) + Excel |
|
Regions and Countries Covered |
|||||
|
North America |
Europe |
Asia Pacific |
Middle East |
Africa |
South America |
|
|
|
|
|
|
|
Companies Covered |
|||||
|
|
|
|
|
|
Email-Encryption-Market Segmentation and Highlights
|
Segment |
Sub-segment |
|
By Offering |
|
|
By Deployment Mode |
|
|
By Encryption Type |
|
|
By Enterprise Size |
|
|
By Security Type |
|
|
By Application |
|
|
By End User |
|
|
By Industry Vertical |
|
Frequently Asked Questions
Table of Contents
- 1. Research Methodology and Assumptions
- 1.1. Definitions
- 1.2. Research Design and Approach
- 1.3. Data Collection Methods
- 1.4. Base Estimates and Calculations
- 1.5. Forecasting Models
- 1.5.1. Key Forecast Factors & Impact Analysis
- 1.6. Secondary Research
- 1.6.1. Open Sources
- 1.6.2. Paid Databases
- 1.6.3. Associations
- 1.7. Primary Research
- 1.7.1. Primary Sources
- 1.7.2. Primary Interviews with Stakeholders across Ecosystem
- 2. Executive Summary
- 2.1. Global Email Encryption Market Outlook
- 2.1.1. Global Email Encryption Market Size (Value - USD Bn), and Forecasts, 2021-2035
- 2.1.2. Compounded Annual Growth Rate Analysis
- 2.1.3. Growth Opportunity Analysis
- 2.1.4. Segmental Share Analysis
- 2.1.5. Geographical Share Analysis
- 2.2. Market Analysis and Facts
- 2.3. Supply-Demand Analysis
- 2.4. Competitive Benchmarking
- 2.5. Go-to- Market Strategy
- 2.5.1. Customer/ End-use Industry Assessment
- 2.5.2. Growth Opportunity Data, 2025-2035
- 2.5.2.1. Regional Data
- 2.5.2.2. Country Data
- 2.5.2.3. Segmental Data
- 2.5.3. Identification of Potential Market Spaces
- 2.5.4. GAP Analysis
- 2.5.5. Potential Attractive Price Points
- 2.5.6. Prevailing Market Risks & Challenges
- 2.5.7. Preferred Sales & Marketing Strategies
- 2.5.8. Key Recommendations and Analysis
- 2.5.9. A Way Forward
- 2.1. Global Email Encryption Market Outlook
- 3. Industry Data and Premium Insights
- 3.1. Global Email Encryption Industry Overview, 2025
- 3.1.1. Information Technology & Media Ecosystem Analysis
- 3.1.2. Key Trends for Information Technology & Media Industry
- 3.1.3. Regional Distribution for Information Technology & Media Industry
- 3.2. Supplier Customer Data
- 3.3. Source Roadmap and Developments
- 3.4. Trade Analysis
- 3.4.1. Import & Export Analysis, 2025
- 3.4.2. Top Importing Countries
- 3.4.3. Top Exporting Countries
- 3.5. Trump Tariff Impact Analysis
- 3.5.1. Manufacturer
- 3.5.2. Supply Chain
- 3.5.3. End Consumer
- 3.6. Raw Material Analysis
- 3.1. Global Email Encryption Industry Overview, 2025
- 4. Market Overview
- 4.1. Market Dynamics
- 4.1.1. Drivers
- 4.1.1.1. Increasing Demand for Automated Email Encryption in Evolving Digital Ecosystems Expansion
- 4.1.2. Restraints
- 4.1.2.1. Operational Complexity and User Resistance Limiting Broader Adoption of Email Encryption Solutions
- 4.1.1. Drivers
- 4.2. Key Trend Analysis
- 4.3. Regulatory Framework
- 4.3.1. Key Regulations, Norms, and Subsidies, by Key Countries
- 4.3.2. Tariffs and Standards
- 4.3.3. Impact Analysis of Regulations on the Market
- 4.4. Eosystem Analysis
- 4.5. Cost Structure Analysis
- 4.5.1. Parameter’s Share for Cost Associated
- 4.5.2. COGP vs COGS
- 4.5.3. Profit Margin Analysis
- 4.6. Pricing Analysis
- 4.6.1. Regional Pricing Analysis
- 4.6.2. Segmental Pricing Trends
- 4.6.3. Factors Influencing Pricing
- 4.7. Porter’s Five Forces Analysis
- 4.8. PESTEL Analysis
- 4.9. Global Email Encryption Market Demand
- 4.9.1. Historical Market Size - (Value - USD Bn), 2021-2024
- 4.9.2. Current and Future Market Size - (Value - USD Bn), 2025–2035
- 4.9.2.1. Y-o-Y Growth Trends
- 4.9.2.2. Absolute $ Opportunity Assessment
- 4.1. Market Dynamics
- 5. Competition Landscape
- 5.1. Competition structure
- 5.1.1. Fragmented v/s consolidated
- 5.2. Company Share Analysis, 2025
- 5.2.1. Global Company Market Share
- 5.2.2. By Region
- 5.2.2.1. North America
- 5.2.2.2. Europe
- 5.2.2.3. Asia Pacific
- 5.2.2.4. Middle East
- 5.2.2.5. Africa
- 5.2.2.6. South America
- 5.3. Product Comparison Matrix
- 5.3.1. Specifications
- 5.3.2. Market Positioning
- 5.3.3. Pricing
- 5.1. Competition structure
- 6. Global Email Encryption Market Analysis, by Offering
- 6.1. Key Segment Analysis
- 6.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Offering, 2021-2035
- 6.2.1. Solutions
- 6.2.1.1. End-to-End Encryption Software
- 6.2.1.2. Gateway Encryption Solutions
- 6.2.1.3. Secure Email Clients
- 6.2.1.4. Cloud-Based Email Encryption Platforms
- 6.2.1.5. Encryption Key Management Tools
- 6.2.1.6. Mobile Email Encryption Solutions
- 6.2.1.7. Others
- 6.2.2. Services
- 6.2.2.1. Professional Services
- 6.2.2.1.1. Consulting Services
- 6.2.2.1.2. Integration & Implementation Services
- 6.2.2.1.3. Training & Education Services
- 6.2.2.1.4. Support & Maintenance
- 6.2.2.2. Managed Services
- 6.2.2.2.1. Managed Encryption Services
- 6.2.2.2.2. Managed Security & Monitoring
- 6.2.2.2.3. Incident Response & Threat Management
- 6.2.2.1. Professional Services
- 6.2.1. Solutions
- 7. Global Email Encryption Market Analysis, by Deployment Mode
- 7.1. Key Segment Analysis
- 7.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Deployment Mode, 2021-2035
- 7.2.1. On-Premises
- 7.2.2. Cloud-Based
- 7.2.3. Hybrid Cloud
- 8. Global Email Encryption Market Analysis, by Encryption Type
- 8.1. Key Segment Analysis
- 8.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, Encryption Type, 2021-2035
- 8.2.1. End-to-End Email Encryption
- 8.2.2. Gateway Email Encryption
- 8.2.3. Client-Side Email Encryption
- 8.2.4. Server-Side Email Encryption
- 9. Global Email Encryption Market Analysis, by Enterprise Size
- 9.1. Key Segment Analysis
- 9.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Enterprise Size, 2021-2035
- 9.2.1. Small and Medium-Sized Enterprises (SMEs)
- 9.2.2. Large Enterprises
- 10. Global Email Encryption Market Analysis, by Security Type
- 10.1. Key Segment Analysis
- 10.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Security Type, 2021-2035
- 10.2.1. Data-at-Rest Protection
- 10.2.2. Data-in-Transit Protection
- 11. Global Email Encryption Market Analysis, by Application
- 11.1. Key Segment Analysis
- 11.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Application, 2021-2035
- 11.2.1. Compliance Management
- 11.2.2. Data Protection
- 11.2.3. Secure Messaging
- 11.2.4. Risk Management
- 11.2.5. Others
- 12. Global Email Encryption Market Analysis, by End User
- 12.1. Key Segment Analysis
- 12.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by End User, 2021-2035
- 12.2.1. Individual/Consumer
- 12.2.2. Enterprises
- 12.2.3. Government Agencies
- 12.2.4. Others
- 13. Global Email Encryption Market Analysis, by Industry Vertical
- 13.1. Key Segment Analysis
- 13.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Industry Vertical, 2021-2035
- 13.2.1. BFSI
- 13.2.2. Healthcare
- 13.2.3. Government & Defense
- 13.2.4. IT & Telecom
- 13.2.5. Retail & E-commerce
- 13.2.6. Manufacturing
- 13.2.7. Education
- 13.2.8. Energy & Utilities
- 13.2.9. Others
- 14. Global Email Encryption Market Analysis and Forecasts, by Region
- 14.1. Key Findings
- 14.2. Global Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, by Region, 2021-2035
- 14.2.1. North America
- 14.2.2. Europe
- 14.2.3. Asia Pacific
- 14.2.4. Middle East
- 14.2.5. Africa
- 14.2.6. South America
- 15. North America Email Encryption Market Analysis
- 15.1. Key Segment Analysis
- 15.2. Regional Snapshot
- 15.3. North America Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 15.3.1. Offering
- 15.3.2. Deployment Mode
- 15.3.3. Encryption Type
- 15.3.4. Enterprise Size
- 15.3.5. Security Type
- 15.3.6. Application
- 15.3.7. End User
- 15.3.8. Industry Vertical
- 15.3.9. Country
- 15.3.9.1. USA
- 15.3.9.2. Canada
- 15.3.9.3. Mexico
- 15.4. USA Email Encryption Market
- 15.4.1. Country Segmental Analysis
- 15.4.2. Offering
- 15.4.3. Deployment Mode
- 15.4.4. Encryption Type
- 15.4.5. Enterprise Size
- 15.4.6. Security Type
- 15.4.7. Application
- 15.4.8. End User
- 15.4.9. Industry Vertical
- 15.5. Canada Email Encryption Market
- 15.5.1. Country Segmental Analysis
- 15.5.2. Offering
- 15.5.3. Deployment Mode
- 15.5.4. Encryption Type
- 15.5.5. Enterprise Size
- 15.5.6. Security Type
- 15.5.7. Application
- 15.5.8. End User
- 15.5.9. Industry Vertical
- 15.6. Mexico Email Encryption Market
- 15.6.1. Country Segmental Analysis
- 15.6.2. Offering
- 15.6.3. Deployment Mode
- 15.6.4. Encryption Type
- 15.6.5. Enterprise Size
- 15.6.6. Security Type
- 15.6.7. Application
- 15.6.8. End User
- 15.6.9. Industry Vertical
- 16. Europe Email Encryption Market Analysis
- 16.1. Key Segment Analysis
- 16.2. Regional Snapshot
- 16.3. Europe Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 16.3.1. Offering
- 16.3.2. Deployment Mode
- 16.3.3. Encryption Type
- 16.3.4. Enterprise Size
- 16.3.5. Security Type
- 16.3.6. Application
- 16.3.7. End User
- 16.3.8. Industry Vertical
- 16.3.9. Country
- 16.3.9.1. Germany
- 16.3.9.2. United Kingdom
- 16.3.9.3. France
- 16.3.9.4. Italy
- 16.3.9.5. Spain
- 16.3.9.6. Netherlands
- 16.3.9.7. Nordic Countries
- 16.3.9.8. Poland
- 16.3.9.9. Russia & CIS
- 16.3.9.10. Rest of Europe
- 16.4. Germany Email Encryption Market
- 16.4.1. Country Segmental Analysis
- 16.4.2. Offering
- 16.4.3. Deployment Mode
- 16.4.4. Encryption Type
- 16.4.5. Enterprise Size
- 16.4.6. Security Type
- 16.4.7. Application
- 16.4.8. End User
- 16.4.9. Industry Vertical
- 16.5. United Kingdom Email Encryption Market
- 16.5.1. Country Segmental Analysis
- 16.5.2. Offering
- 16.5.3. Deployment Mode
- 16.5.4. Encryption Type
- 16.5.5. Enterprise Size
- 16.5.6. Security Type
- 16.5.7. Application
- 16.5.8. End User
- 16.5.9. Industry Vertical
- 16.6. France Email Encryption Market
- 16.6.1. Country Segmental Analysis
- 16.6.2. Offering
- 16.6.3. Deployment Mode
- 16.6.4. Encryption Type
- 16.6.5. Enterprise Size
- 16.6.6. Security Type
- 16.6.7. Application
- 16.6.8. End User
- 16.6.9. Industry Vertical
- 16.7. Italy Email Encryption Market
- 16.7.1. Country Segmental Analysis
- 16.7.2. Offering
- 16.7.3. Deployment Mode
- 16.7.4. Encryption Type
- 16.7.5. Enterprise Size
- 16.7.6. Security Type
- 16.7.7. Application
- 16.7.8. End User
- 16.7.9. Industry Vertical
- 16.8. Spain Email Encryption Market
- 16.8.1. Country Segmental Analysis
- 16.8.2. Offering
- 16.8.3. Deployment Mode
- 16.8.4. Encryption Type
- 16.8.5. Enterprise Size
- 16.8.6. Security Type
- 16.8.7. Application
- 16.8.8. End User
- 16.8.9. Industry Vertical
- 16.9. Netherlands Email Encryption Market
- 16.9.1. Country Segmental Analysis
- 16.9.2. Offering
- 16.9.3. Deployment Mode
- 16.9.4. Encryption Type
- 16.9.5. Enterprise Size
- 16.9.6. Security Type
- 16.9.7. Application
- 16.9.8. End User
- 16.9.9. Industry Vertical
- 16.10. Nordic Countries Email Encryption Market
- 16.10.1. Country Segmental Analysis
- 16.10.2. Offering
- 16.10.3. Deployment Mode
- 16.10.4. Encryption Type
- 16.10.5. Enterprise Size
- 16.10.6. Security Type
- 16.10.7. Application
- 16.10.8. End User
- 16.10.9. Industry Vertical
- 16.11. Poland Email Encryption Market
- 16.11.1. Country Segmental Analysis
- 16.11.2. Offering
- 16.11.3. Deployment Mode
- 16.11.4. Encryption Type
- 16.11.5. Enterprise Size
- 16.11.6. Security Type
- 16.11.7. Application
- 16.11.8. End User
- 16.11.9. Industry Vertical
- 16.12. Russia & CIS Email Encryption Market
- 16.12.1. Country Segmental Analysis
- 16.12.2. Offering
- 16.12.3. Deployment Mode
- 16.12.4. Encryption Type
- 16.12.5. Enterprise Size
- 16.12.6. Security Type
- 16.12.7. Application
- 16.12.8. End User
- 16.12.9. Industry Vertical
- 16.13. Rest of Europe Email Encryption Market
- 16.13.1. Country Segmental Analysis
- 16.13.2. Offering
- 16.13.3. Deployment Mode
- 16.13.4. Encryption Type
- 16.13.5. Enterprise Size
- 16.13.6. Security Type
- 16.13.7. Application
- 16.13.8. End User
- 16.13.9. Industry Vertical
- 17. Asia Pacific Email Encryption Market Analysis
- 17.1. Key Segment Analysis
- 17.2. Regional Snapshot
- 17.3. East Asia Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 17.3.1. Offering
- 17.3.2. Deployment Mode
- 17.3.3. Encryption Type
- 17.3.4. Enterprise Size
- 17.3.5. Security Type
- 17.3.6. Application
- 17.3.7. End User
- 17.3.8. Industry Vertical
- 17.3.9. Country
- 17.3.9.1. China
- 17.3.9.2. India
- 17.3.9.3. Japan
- 17.3.9.4. South Korea
- 17.3.9.5. Australia and New Zealand
- 17.3.9.6. Indonesia
- 17.3.9.7. Malaysia
- 17.3.9.8. Thailand
- 17.3.9.9. Vietnam
- 17.3.9.10. Rest of Asia-Pacific
- 17.4. China Email Encryption Market
- 17.4.1. Country Segmental Analysis
- 17.4.2. Offering
- 17.4.3. Deployment Mode
- 17.4.4. Encryption Type
- 17.4.5. Enterprise Size
- 17.4.6. Security Type
- 17.4.7. Application
- 17.4.8. End User
- 17.4.9. Industry Vertical
- 17.5. India Email Encryption Market
- 17.5.1. Country Segmental Analysis
- 17.5.2. Offering
- 17.5.3. Deployment Mode
- 17.5.4. Encryption Type
- 17.5.5. Enterprise Size
- 17.5.6. Security Type
- 17.5.7. Application
- 17.5.8. End User
- 17.5.9. Industry Vertical
- 17.6. Japan Email Encryption Market
- 17.6.1. Country Segmental Analysis
- 17.6.2. Offering
- 17.6.3. Deployment Mode
- 17.6.4. Encryption Type
- 17.6.5. Enterprise Size
- 17.6.6. Security Type
- 17.6.7. Application
- 17.6.8. End User
- 17.6.9. Industry Vertical
- 17.7. South Korea Email Encryption Market
- 17.7.1. Country Segmental Analysis
- 17.7.2. Offering
- 17.7.3. Deployment Mode
- 17.7.4. Encryption Type
- 17.7.5. Enterprise Size
- 17.7.6. Security Type
- 17.7.7. Application
- 17.7.8. End User
- 17.7.9. Industry Vertical
- 17.8. Australia and New Zealand Email Encryption Market
- 17.8.1. Country Segmental Analysis
- 17.8.2. Offering
- 17.8.3. Deployment Mode
- 17.8.4. Encryption Type
- 17.8.5. Enterprise Size
- 17.8.6. Security Type
- 17.8.7. Application
- 17.8.8. End User
- 17.8.9. Industry Vertical
- 17.9. Indonesia Email Encryption Market
- 17.9.1. Country Segmental Analysis
- 17.9.2. Offering
- 17.9.3. Deployment Mode
- 17.9.4. Encryption Type
- 17.9.5. Enterprise Size
- 17.9.6. Security Type
- 17.9.7. Application
- 17.9.8. End User
- 17.9.9. Industry Vertical
- 17.10. Malaysia Email Encryption Market
- 17.10.1. Country Segmental Analysis
- 17.10.2. Offering
- 17.10.3. Deployment Mode
- 17.10.4. Encryption Type
- 17.10.5. Enterprise Size
- 17.10.6. Security Type
- 17.10.7. Application
- 17.10.8. End User
- 17.10.9. Industry Vertical
- 17.11. Thailand Email Encryption Market
- 17.11.1. Country Segmental Analysis
- 17.11.2. Offering
- 17.11.3. Deployment Mode
- 17.11.4. Encryption Type
- 17.11.5. Enterprise Size
- 17.11.6. Security Type
- 17.11.7. Application
- 17.11.8. End User
- 17.11.9. Industry Vertical
- 17.12. Vietnam Email Encryption Market
- 17.12.1. Country Segmental Analysis
- 17.12.2. Offering
- 17.12.3. Deployment Mode
- 17.12.4. Encryption Type
- 17.12.5. Enterprise Size
- 17.12.6. Security Type
- 17.12.7. Application
- 17.12.8. End User
- 17.12.9. Industry Vertical
- 17.13. Rest of Asia Pacific Email Encryption Market
- 17.13.1. Country Segmental Analysis
- 17.13.2. Offering
- 17.13.3. Deployment Mode
- 17.13.4. Encryption Type
- 17.13.5. Enterprise Size
- 17.13.6. Security Type
- 17.13.7. Application
- 17.13.8. End User
- 17.13.9. Industry Vertical
- 18. Middle East Email Encryption Market Analysis
- 18.1. Key Segment Analysis
- 18.2. Regional Snapshot
- 18.3. Middle East Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 18.3.1. Offering
- 18.3.2. Deployment Mode
- 18.3.3. Encryption Type
- 18.3.4. Enterprise Size
- 18.3.5. Security Type
- 18.3.6. Application
- 18.3.7. End User
- 18.3.8. Industry Vertical
- 18.3.9. Country
- 18.3.9.1. Turkey
- 18.3.9.2. UAE
- 18.3.9.3. Saudi Arabia
- 18.3.9.4. Israel
- 18.3.9.5. Rest of Middle East
- 18.4. Turkey Email Encryption Market
- 18.4.1. Country Segmental Analysis
- 18.4.2. Offering
- 18.4.3. Deployment Mode
- 18.4.4. Encryption Type
- 18.4.5. Enterprise Size
- 18.4.6. Security Type
- 18.4.7. Application
- 18.4.8. End User
- 18.4.9. Industry Vertical
- 18.5. UAE Email Encryption Market
- 18.5.1. Country Segmental Analysis
- 18.5.2. Offering
- 18.5.3. Deployment Mode
- 18.5.4. Encryption Type
- 18.5.5. Enterprise Size
- 18.5.6. Security Type
- 18.5.7. Application
- 18.5.8. End User
- 18.5.9. Industry Vertical
- 18.6. Saudi Arabia Email Encryption Market
- 18.6.1. Country Segmental Analysis
- 18.6.2. Offering
- 18.6.3. Deployment Mode
- 18.6.4. Encryption Type
- 18.6.5. Enterprise Size
- 18.6.6. Security Type
- 18.6.7. Application
- 18.6.8. End User
- 18.6.9. Industry Vertical
- 18.7. Israel Email Encryption Market
- 18.7.1. Country Segmental Analysis
- 18.7.2. Offering
- 18.7.3. Deployment Mode
- 18.7.4. Encryption Type
- 18.7.5. Enterprise Size
- 18.7.6. Security Type
- 18.7.7. Application
- 18.7.8. End User
- 18.7.9. Industry Vertical
- 18.8. Rest of Middle East Email Encryption Market
- 18.8.1. Country Segmental Analysis
- 18.8.2. Offering
- 18.8.3. Deployment Mode
- 18.8.4. Encryption Type
- 18.8.5. Enterprise Size
- 18.8.6. Security Type
- 18.8.7. Application
- 18.8.8. End User
- 18.8.9. Industry Vertical
- 19. Africa Email Encryption Market Analysis
- 19.1. Key Segment Analysis
- 19.2. Regional Snapshot
- 19.3. Africa Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 19.3.1. Offering
- 19.3.2. Deployment Mode
- 19.3.3. Encryption Type
- 19.3.4. Enterprise Size
- 19.3.5. Security Type
- 19.3.6. Application
- 19.3.7. End User
- 19.3.8. Industry Vertical
- 19.3.9. Country
- 19.3.9.1. South Africa
- 19.3.9.2. Egypt
- 19.3.9.3. Nigeria
- 19.3.9.4. Algeria
- 19.3.9.5. Rest of Africa
- 19.4. South Africa Email Encryption Market
- 19.4.1. Country Segmental Analysis
- 19.4.2. Offering
- 19.4.3. Deployment Mode
- 19.4.4. Encryption Type
- 19.4.5. Enterprise Size
- 19.4.6. Security Type
- 19.4.7. Application
- 19.4.8. End User
- 19.4.9. Industry Vertical
- 19.5. Egypt Email Encryption Market
- 19.5.1. Country Segmental Analysis
- 19.5.2. Offering
- 19.5.3. Deployment Mode
- 19.5.4. Encryption Type
- 19.5.5. Enterprise Size
- 19.5.6. Security Type
- 19.5.7. Application
- 19.5.8. End User
- 19.5.9. Industry Vertical
- 19.6. Nigeria Email Encryption Market
- 19.6.1. Country Segmental Analysis
- 19.6.2. Offering
- 19.6.3. Deployment Mode
- 19.6.4. Encryption Type
- 19.6.5. Enterprise Size
- 19.6.6. Security Type
- 19.6.7. Application
- 19.6.8. End User
- 19.6.9. Industry Vertical
- 19.7. Algeria Email Encryption Market
- 19.7.1. Country Segmental Analysis
- 19.7.2. Offering
- 19.7.3. Deployment Mode
- 19.7.4. Encryption Type
- 19.7.5. Enterprise Size
- 19.7.6. Security Type
- 19.7.7. Application
- 19.7.8. End User
- 19.7.9. Industry Vertical
- 19.8. Rest of Africa Email Encryption Market
- 19.8.1. Country Segmental Analysis
- 19.8.2. Offering
- 19.8.3. Deployment Mode
- 19.8.4. Encryption Type
- 19.8.5. Enterprise Size
- 19.8.6. Security Type
- 19.8.7. Application
- 19.8.8. End User
- 19.8.9. Industry Vertical
- 20. South America Email Encryption Market Analysis
- 20.1. Key Segment Analysis
- 20.2. Regional Snapshot
- 20.3. Central and South Africa Email Encryption Market Size (Value - USD Bn), Analysis, and Forecasts, 2021-2035
- 20.3.1. Offering
- 20.3.2. Deployment Mode
- 20.3.3. Encryption Type
- 20.3.4. Enterprise Size
- 20.3.5. Security Type
- 20.3.6. Application
- 20.3.7. End User
- 20.3.8. Industry Vertical
- 20.3.9. Country
- 20.3.9.1. Brazil
- 20.3.9.2. Argentina
- 20.3.9.3. Rest of South America
- 20.4. Brazil Email Encryption Market
- 20.4.1. Country Segmental Analysis
- 20.4.2. Offering
- 20.4.3. Deployment Mode
- 20.4.4. Encryption Type
- 20.4.5. Enterprise Size
- 20.4.6. Security Type
- 20.4.7. Application
- 20.4.8. End User
- 20.4.9. Industry Vertical
- 20.5. Argentina Email Encryption Market
- 20.5.1. Country Segmental Analysis
- 20.5.2. Offering
- 20.5.3. Deployment Mode
- 20.5.4. Encryption Type
- 20.5.5. Enterprise Size
- 20.5.6. Security Type
- 20.5.7. Application
- 20.5.8. End User
- 20.5.9. Industry Vertical
- 20.6. Rest of South America Email Encryption Market
- 20.6.1. Country Segmental Analysis
- 20.6.2. Offering
- 20.6.3. Deployment Mode
- 20.6.4. Encryption Type
- 20.6.5. Enterprise Size
- 20.6.6. Security Type
- 20.6.7. Application
- 20.6.8. End User
- 20.6.9. Industry Vertical
- 21. Key Players/ Company Profile
- 21.1. BAE Systems plc
- 21.1.1. Company Details/ Overview
- 21.1.2. Company Financials
- 21.1.3. Key Customers and Competitors
- 21.1.4. Business/ Industry Portfolio
- 21.1.5. Product Portfolio/ Specification Details
- 21.1.6. Pricing Data
- 21.1.7. Strategic Overview
- 21.1.8. Recent Developments
- 21.2. Barracuda Networks, Inc.
- 21.3. Cisco Systems, Inc.
- 21.4. Egress Software Technologies
- 21.5. Entrust Datacard Corporation
- 21.6. LuxSci
- 21.7. Micro Focus International plc
- 21.8. Microsoft Corporation
- 21.9. Mimecast Limited
- 21.10. OpenText Corporation
- 21.11. Paubox, Inc.
- 21.12. Proofpoint, Inc.
- 21.13. Proton Technologies AG (ProtonMail)
- 21.14. Sophos Group plc
- 21.15. Symantec Corporation (part of Broadcom Inc.)
- 21.16. Trend Micro Incorporated
- 21.17. Trustifi
- 21.18. Vircom Inc.
- 21.19. Virtru Corporation
- 21.20. Zix Corporation
- 21.21. Others Key Players
- 21.1. BAE Systems plc
Note* - This is just tentative list of players. While providing the report, we will cover more number of players based on their revenue and share for each geography
Research Design
Our research design integrates both demand-side and supply-side analysis through a balanced combination of primary and secondary research methodologies. By utilizing both bottom-up and top-down approaches alongside rigorous data triangulation methods, we deliver robust market intelligence that supports strategic decision-making.
MarketGenics' comprehensive research design framework ensures the delivery of accurate, reliable, and actionable market intelligence. Through the integration of multiple research approaches, rigorous validation processes, and expert analysis, we provide our clients with the insights needed to make informed strategic decisions and capitalize on market opportunities.
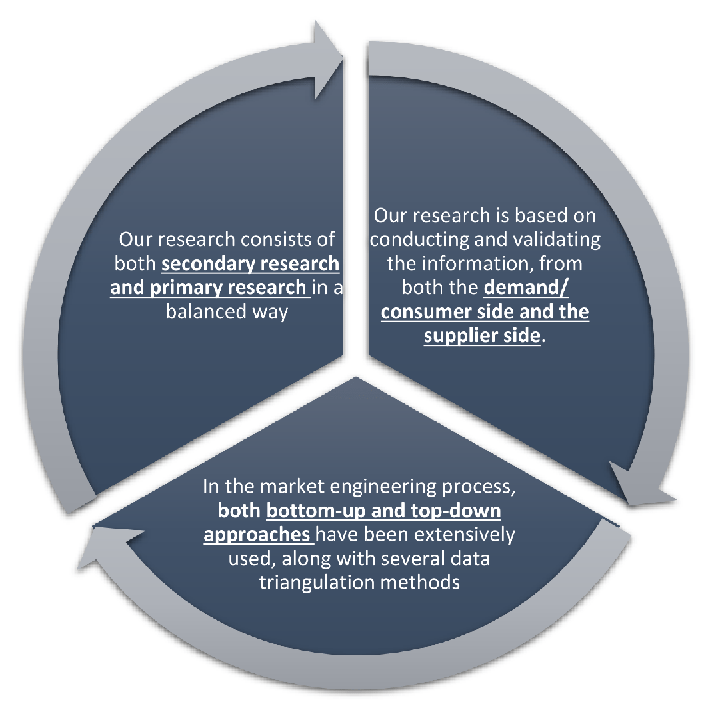
MarketGenics leverages a dedicated industry panel of experts and a comprehensive suite of paid databases to effectively collect, consolidate, and analyze market intelligence.
Our approach has consistently proven to be reliable and effective in generating accurate market insights, identifying key industry trends, and uncovering emerging business opportunities.
Through both primary and secondary research, we capture and analyze critical company-level data such as manufacturing footprints, including technical centers, R&D facilities, sales offices, and headquarters.
Our expert panel further enhances our ability to estimate market size for specific brands based on validated field-level intelligence.
Our data mining techniques incorporate both parametric and non-parametric methods, allowing for structured data collection, sorting, processing, and cleaning.
Demand projections are derived from large-scale data sets analyzed through proprietary algorithms, culminating in robust and reliable market sizing.
Research Approach
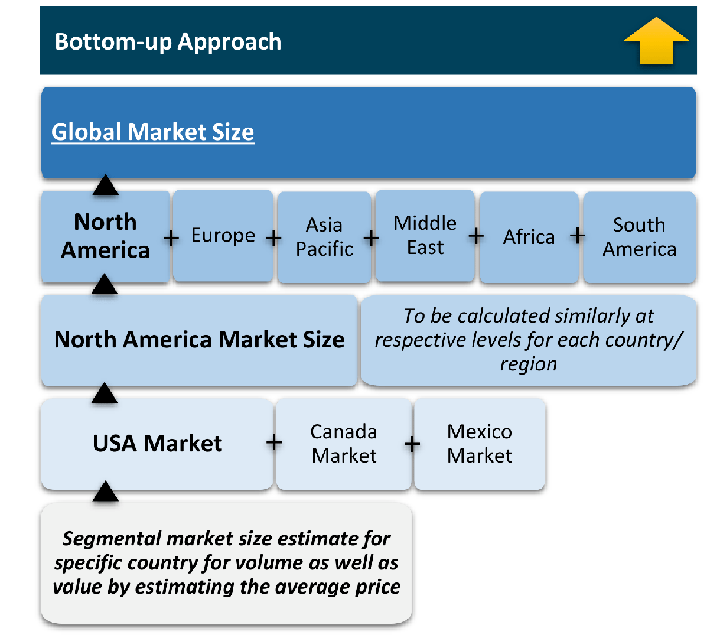
The bottom-up approach builds market estimates by starting with the smallest addressable market units and systematically aggregating them to create comprehensive market size projections.
This method begins with specific, granular data points and builds upward to create the complete market landscape.
Customer Analysis → Segmental Analysis → Geographical Analysis
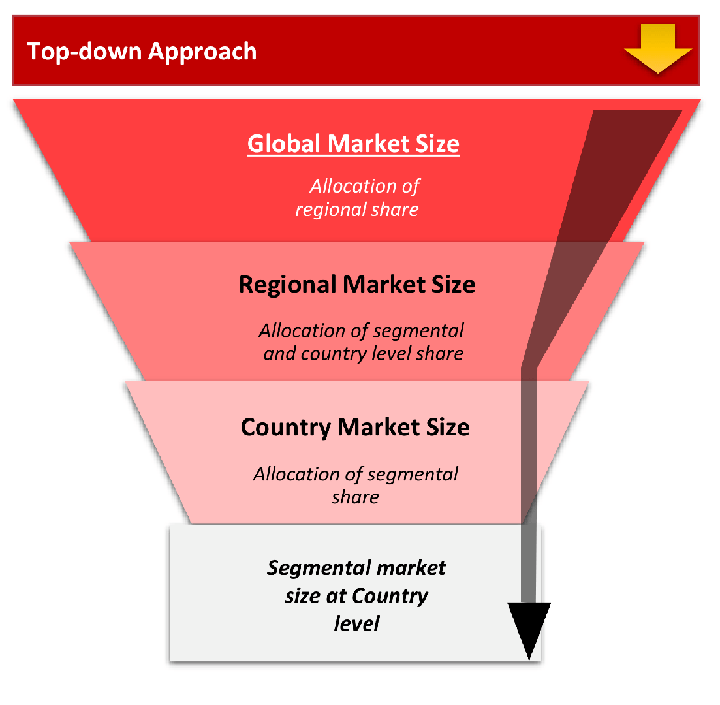
The top-down approach starts with the broadest possible market data and systematically narrows it down through a series of filters and assumptions to arrive at specific market segments or opportunities.
This method begins with the big picture and works downward to increasingly specific market slices.
TAM → SAM → SOM
Research Methods
Desk / Secondary Research
While analysing the market, we extensively study secondary sources, directories, and databases to identify and collect information useful for this technical, market-oriented, and commercial report. Secondary sources that we utilize are not only the public sources, but it is a combination of Open Source, Associations, Paid Databases, MG Repository & Knowledgebase, and others.
- Company websites, annual reports, financial reports, broker reports, and investor presentations
- National government documents, statistical databases and reports
- News articles, press releases and web-casts specific to the companies operating in the market, Magazines, reports, and others
- We gather information from commercial data sources for deriving company specific data such as segmental revenue, share for geography, product revenue, and others
- Internal and external proprietary databases (industry-specific), relevant patent, and regulatory databases
- Governing Bodies, Government Organizations
- Relevant Authorities, Country-specific Associations for Industries
We also employ the model mapping approach to estimate the product level market data through the players' product portfolio
Primary Research
Primary research/ interviews is vital in analyzing the market. Most of the cases involves paid primary interviews. Primary sources include primary interviews through e-mail interactions, telephonic interviews, surveys as well as face-to-face interviews with the different stakeholders across the value chain including several industry experts.
| Type of Respondents | Number of Primaries |
|---|---|
| Tier 2/3 Suppliers | ~20 |
| Tier 1 Suppliers | ~25 |
| End-users | ~25 |
| Industry Expert/ Panel/ Consultant | ~30 |
| Total | ~100 |
MG Knowledgebase
• Repository of industry blog, newsletter and case studies
• Online platform covering detailed market reports, and company profiles
Forecasting Factors and Models
Forecasting Factors
- Historical Trends – Past market patterns, cycles, and major events that shaped how markets behave over time. Understanding past trends helps predict future behavior.
- Industry Factors – Specific characteristics of the industry like structure, regulations, and innovation cycles that affect market dynamics.
- Macroeconomic Factors – Economic conditions like GDP growth, inflation, and employment rates that affect how much money people have to spend.
- Demographic Factors – Population characteristics like age, income, and location that determine who can buy your product.
- Technology Factors – How quickly people adopt new technology and how much technology infrastructure exists.
- Regulatory Factors – Government rules, laws, and policies that can help or restrict market growth.
- Competitive Factors – Analyzing competition structure such as degree of competition and bargaining power of buyers and suppliers.
Forecasting Models / Techniques
Multiple Regression Analysis
- Identify and quantify factors that drive market changes
- Statistical modeling to establish relationships between market drivers and outcomes
Time Series Analysis – Seasonal Patterns
- Understand regular cyclical patterns in market demand
- Advanced statistical techniques to separate trend, seasonal, and irregular components
Time Series Analysis – Trend Analysis
- Identify underlying market growth patterns and momentum
- Statistical analysis of historical data to project future trends
Expert Opinion – Expert Interviews
- Gather deep industry insights and contextual understanding
- In-depth interviews with key industry stakeholders
Multi-Scenario Development
- Prepare for uncertainty by modeling different possible futures
- Creating optimistic, pessimistic, and most likely scenarios
Time Series Analysis – Moving Averages
- Sophisticated forecasting for complex time series data
- Auto-regressive integrated moving average models with seasonal components
Econometric Models
- Apply economic theory to market forecasting
- Sophisticated economic models that account for market interactions
Expert Opinion – Delphi Method
- Harness collective wisdom of industry experts
- Structured, multi-round expert consultation process
Monte Carlo Simulation
- Quantify uncertainty and probability distributions
- Thousands of simulations with varying input parameters
Research Analysis
Our research framework is built upon the fundamental principle of validating market intelligence from both demand and supply perspectives. This dual-sided approach ensures comprehensive market understanding and reduces the risk of single-source bias.
Demand-Side Analysis: We understand end-user/application behavior, preferences, and market needs along with the penetration of the product for specific application.
Supply-Side Analysis: We estimate overall market revenue, analyze the segmental share along with industry capacity, competitive landscape, and market structure.
Validation & Evaluation
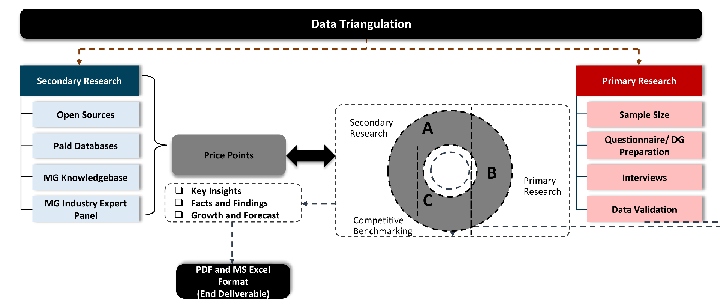
Data triangulation is a validation technique that uses multiple methods, sources, or perspectives to examine the same research question, thereby increasing the credibility and reliability of research findings. In market research, triangulation serves as a quality assurance mechanism that helps identify and minimize bias, validate assumptions, and ensure accuracy in market estimates.
- Data Source Triangulation – Using multiple data sources to examine the same phenomenon
- Methodological Triangulation – Using multiple research methods to study the same research question
- Investigator Triangulation – Using multiple researchers or analysts to examine the same data
- Theoretical Triangulation – Using multiple theoretical perspectives to interpret the same data
Custom Market Research Services
We will customise the research for you, in case the report listed above does not meet your requirements.
Get 10% Free Customisation