Post-Quantum‑Secure Hardware Market Size, Share & Trends Analysis Report by Hardware Component Type (Quantum-Resistant Cryptographic Chips, Secure Hardware Security Modules (HSMs), Post-Quantum TPM (Trusted Platform Modules), Quantum-Safe Network Interface Cards, PQ-Secure Processors/Microcontrollers, Quantum-Resistant Memory Devices, PQ-Safe Communication Chips, Quantum-Secure Storage Controllers, Others), Cryptographic Algorithm Type, Form Factor & Integration, Deployment Model, Processing Architecture, End-Use Industry, and Geography (North America, Europe, Asia Pacific, Middle East, Africa, and South America) – Global Industry Data, Trends, and Forecasts, 2025–2035
|
|
|
Segmental Data Insights |
|
|
Demand Trends |
|
|
Competitive Landscape |
|
|
Strategic Development |
|
|
Future Outlook & Opportunities |
|
Post-Quantum‑Secure Hardware Market Size, Share, and Growth
The global post-quantum‑secure hardware market is experiencing robust growth, with its estimated value of USD 0.7 billion in the year 2025 and USD 20.0 billion by the period 2035, registering a CAGR of 39.8%, during the forecast period. North America leads the market with market share of 47.3% with USD 0.3 billion revenue.

In July 2025, SEALSQ Corp completed the cryptographic toolbox validation stage for its QS7001 post-quantum hardware platform, a key milestone in the company’s development of quantum-resistant security solutions. The validation confirms the performance of post-quantum cryptographic algorithms, including Kyber and Dilithium, on the platform. The QS7001 is a RISC-V-based secure hardware platform designed to implement NIST-standardized post-quantum cryptography algorithms.
The need to use resistant cryptographic hardware due to the development of quantum computing to the practical stage is already making the global post-quantum-secure hardware market grow and the industries are beginning to shift to the use of secure chips and processors to protect sensitive data in the long-term. The demand is increasing due to growing government developments and defense programs especially with agencies now requiring quantum-resistant specifications to ensure the protection of national security. Thales launched its post-quantum hardware security modules (HSMs) with algorithms that are recommended by NIST in January 2025 to make critical infrastructure future-proof.
Moreover, in March 2025, Intel outlined developments in the area of quantum-resistant instructions set extensions to its server-grade processors, aimed at enterprise workloads that will be at risk in the future by quantum threats. Examples of these efforts are how major manufacturers are complying with regulatory frameworks and cybersecurity requirements, driving mass implementations in financial services, cloud computing, and critical infrastructure. Impact Analysis: The increasing investments made by the chipmakers and security leaders are quickly putting post-quantum-safe hardware at the base of the next-generation cybersecurity ecosystems.
The global post-quantum-secure hardware market has adjacent market opportunities such as quantum key distribution systems, quantum-resistant software solutions, blockchain security platforms, secure cloud infrastructure, and AI-based threat detection systems. These domains are also in line with the increasing trend of cybersecurity infrastructures based on quantum-resilience and contributes to industrywide protection.

Post-Quantum‑Secure Hardware Market Dynamics and Trends
Driver: Rising National Security Concerns Driving Adoption of Post-Quantum Hardware
-
Post-quantum security is now a higher priority in governments and defense agencies to ensure protection of critical infrastructure and information held by governments against quantum computer threats, further it is anticipated to boost the growth of post-quantum-secure hardware market. Post-quantum cryptography Hardware solutions based on post-quantum cryptography are considered necessary to counter weaknesses in previous encryption systems.
- As an example, in January 2025, Thales Group added post-quantum cryptography capability to its hardware security module (HSM) line, specifically to the needs of customers in the defense and aerospace sectors who need to be resilient to attacks by quantum-enabled cryptography. This shows the alignment of the leading manufacturers with the national requirements and defense contracts in creating and scaling post-quantum-ready devices.
- Due to the increased geopolitical risks, defense agencies are hastening the purchase of secure chips, HSMs and accelerators to protect sensitive data and operations.
Restraint: High Implementation Costs Limiting Early-Stage Enterprise Adoption Globally
-
Post-quantum secure hardware is expensive to deploy financially because specialized chipsets, hardware security modules, and supporting infrastructures are frequently well beyond the financial ability of small and mid-sized organizations. The process of transitioning to quantum-resilient systems is more complicated than the expansion to a classical system also increases the expenses when combined with compliance.
- As an example, in October 2024, IBM introduced quantum-safe key management solutions that are built on dedicated hardware accelerators, but initially not all large enterprise clients could use it because it was expensive and required integration. This highlights the cost aspect barrier to organizations that do not belong to the highly regulated sectors such as finance or defense.
- Mainstream adoption might be limited until the cost curves fall as a result of economies of scale, which will retard early post-quantum-secure hardware market penetration.
Opportunity: Integration of Post-Quantum Hardware into Financial Sector Infrastructure
-
The financial services sector experiences an increasing pressure to move to quantum-resilient cybersecurity models, which would represent enormous opportunities to post-quantum secure hardware vendors. Fintech and banks need cryptographic solutions that are established on hardware to ensure that transactions and customer data are sealed.
- Mastercard declared a pilot implementation of post quantitative safe HSMs in partnership with Intel in March 2025 to improve the security of transactions in its international payment infrastructure. This is how financial institutions are turning out to be the first to take such hardware, owing to compliance and reputational requirements.
- The manufacturers can provide scalable and interoperable solutions which can integrate directly with existing financial infrastructure that propel the highest growth of the post-quantum-secure hardware market.
Key Trend: Growing Industry Collaborations to Accelerate Post-Quantum Hardware Standardization
-
An emerging trend in the post-quantum secure hardware market with the strategic partnerships of technology companies, standards bodies with governments to speed up interoperability and adoption of standards. The team work will ensure the hardware protection systems, chips and server are in-line with the developing post-quantum cryptographic requirements.
- As an example, in February 2025, Qualcomm collaborated with NXP Semiconductors to design post-quantum secure chipsets to be used in IoT and mobile devices as suggested by the U.S. National Institute of Standards and Technology (NIST). These partnerships are essential to develop compatibility in the ecosystems and decrease post-quantum-secure hardware market fragmentation.
- Standardization also creates confidence in enterprises to invest in long term hardware applications without experiencing obsolescence.
Post-Quantum‑Secure Hardware Market Analysis and Segmental Data

Secure Hardware Security Modules: Cornerstone of Post-Quantum Resilience
-
Secure hardware security modules (HSMs) are in the most demand in the hardware component type segment of the global post-quantum secure hardware market as businesses and governments progressively depend on dedicated cryptographic hardware processors to protect sensitive information against quantum attacks. HSMs offer key management which can be scaled and are tamper-resistant, therefore this are essential to banking, defense, and cloud providers. Thales introduced NIST-compliant post-quantum algorithm upgrades to its Luna HSMs in January 2025, aiming to serve financial institutions that are getting ready to migrate to quantum safety.
- Compliance requirements and the necessity to interoperate between hybrid IT, where secure hardware ensures long-term resilience is also a factor in driving the surge. The vendors are focusing on upgrades of HSM as the main hardware because of their flexibility to various post-quantum cryptographic requirements. As governments and enterprises accelerate the deployment of pilots, HSMs have been the key hardware supporting quantum-safe digital ecosystems.
- HSMs have become the hardware of choice, and the foundation of post-quantum security deployment.
North America Leading Post-Quantum Hardware Innovation and Adoption
-
The North America post-quantum-secure hardware market has the strongest demand of post-quantum secure hardware because the region leads the way in major projects to safeguard national infrastructure and business networks against quantum-supported cybercrimes. The quantum readiness programs by the U.S. government and adoption of chips, servers, and HSMs by the private sector are leading to rapid implementation of the secure chips, servers, and HSMs. Microsoft added support for post-quantum hardware in Azure in February 2025, working with AMD, highlighting the local provision of leadership in cloud and enterprise security deployments.
- With the existence of large technology giants and high regulatory pulse, deployments in the defense, banking, and healthcare segments are fast-tracked, and hence North America is the most established. The alliances of hardware vendors and cloud computing service provider are guaranteeing faster scalability and adherence to changing standards. This is a proactive ecosystem that demands unmatched demand unlike in other regions.
- The post-quantum secure hardware adoption predominates in North America, establishing the international standards in the security of infrastructure and commercial practices.
Post-Quantum‑Secure Hardware Market Ecosystem
The global post-quantum-secure hardware market is a moderately consolidated, with Tier-1 players such as IBM Corporation, Intel Corporation, Thales Group, and Infineon Technologies AG holding significant influence, while Tier-2 and Tier-3 firms like PQShield, Crypto Quantique, and Rambus provide niche innovations. The ecosystem is marked by medium-to-high concentration, as few players dominate quantum-resistant cryptographic hardware. From a Porter’s Five Forces perspective, buyer concentration remains moderate due to diverse enterprise demand, whereas supplier concentration is high, given the limited advanced semiconductor and cryptography technology providers.

Recent Development and Strategic Overview:
-
In May 2025, Microchip Technology has developed its MEC175xB embedded controllers with embedded immutable post-quantum cryptography support, to help system architects meet evolving security demands. MEC175xB controllers incorporate CNSA 2.0-compliant Module-Lattice-Based Digital Signature Algorithms (ML-DSA), Merkle stateful hash-based Leighton-Micali Signature (LMS) verification and Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM) standardized by NIST.
- In January 2025, Broadcom Inc. announced an industry-first, innovative Emulex Secure Fibre Channel Host Bus Adapters (HBA), a cost-effective, easy-to-manage solution that encrypts all data as it moves between servers and storage. The Emulex Secure HBAs feature a Zero Trust platform with security protocol and data model, cryptographic authentication of endpoints and silicon root-of-trust authentication. They are also compliant with the NIST 800-193 framework.
Report Scope
|
Detail |
|
|
Market Size in 2025 |
USD 0.7 Bn |
|
Market Forecast Value in 2035 |
USD 20.0 Bn |
|
Growth Rate (CAGR) |
39.8% |
|
Forecast Period |
2025 – 2035 |
|
Historical Data Available for |
2021 – 2024 |
|
Market Size Units |
US$ Billion for Value Million Units for Volume |
|
Report Format |
Electronic (PDF) + Excel |
|
North America |
Europe |
Asia Pacific |
Middle East |
Africa |
South America |
|
|
|
|
|
|
|
Companies Covered |
|||||
|
|
|
|
|
|
Post-Quantum‑Secure Hardware Market Segmentation and Highlights
|
Segment |
Sub-segment |
|
By Hardware Component Type |
|
|
By Cryptographic Algorithm Type |
|
|
By Form Factor & Integration |
|
|
By Deployment Model |
|
|
By Processing Architecture |
|
|
By End-Use Industry |
|
Frequently Asked Questions
The global post-quantum‑secure hardware market was valued at USD 0.7 Bn in 2025.
The global post-quantum‑secure hardware market industry is expected to grow at a CAGR of 39.8% from 2025 to 2035.
The demand for post-quantum‑secure hardware is driven by escalating cybersecurity threats, the anticipated rise of quantum computing, regulatory compliance requirements, and the need for secure data transmission in critical digital infrastructures.
In terms of hardware component type, the secure hardware security modules segment accounted for the major share in 2025.
North America is a more attractive region for vendors
Key players in the global post-quantum‑secure hardware market include prominent companies such as Advanced Micro Devices (AMD), Analog Devices Inc., Broadcom Inc., Crypto Quantique, IBM Corporation, ID Quantique, Infineon Technologies AG, Intel Corporation, Marvell Technology Group, MediaTek Inc., Microsemi Corporation, NVIDIA Corporation, NXP Semiconductors, PQShield Limited, Qualcomm Technologies Inc., Rambus Inc., Renesas Electronics Corporation, Samsung Electronics, Texas Instruments Incorporated, Thales Group, and Other Key Players
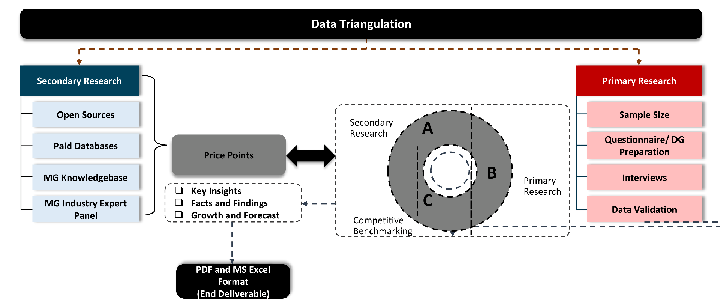
Our research design integrates both demand-side and supply-side analysis through a balanced combination of primary and secondary research methodologies. By utilizing both bottom-up and top-down approaches alongside rigorous data triangulation methods, we deliver robust market intelligence that supports strategic decision-making.
MarketGenics' comprehensive research design framework ensures the delivery of accurate, reliable, and actionable market intelligence. Through the integration of multiple research approaches, rigorous validation processes, and expert analysis, we provide our clients with the insights needed to make informed strategic decisions and capitalize on market opportunities.
MarketGenics leverages a dedicated industry panel of experts and a comprehensive suite of paid databases to effectively collect, consolidate, and analyze market intelligence.
Our approach has consistently proven to be reliable and effective in generating accurate market insights, identifying key industry trends, and uncovering emerging business opportunities.
Through both primary and secondary research, we capture and analyze critical company-level data such as manufacturing footprints, including technical centers, R&D facilities, sales offices, and headquarters.
Our expert panel further enhances our ability to estimate market size for specific brands based on validated field-level intelligence.
Our data mining techniques incorporate both parametric and non-parametric methods, allowing for structured data collection, sorting, processing, and cleaning.
Demand projections are derived from large-scale data sets analyzed through proprietary algorithms, culminating in robust and reliable market sizing.
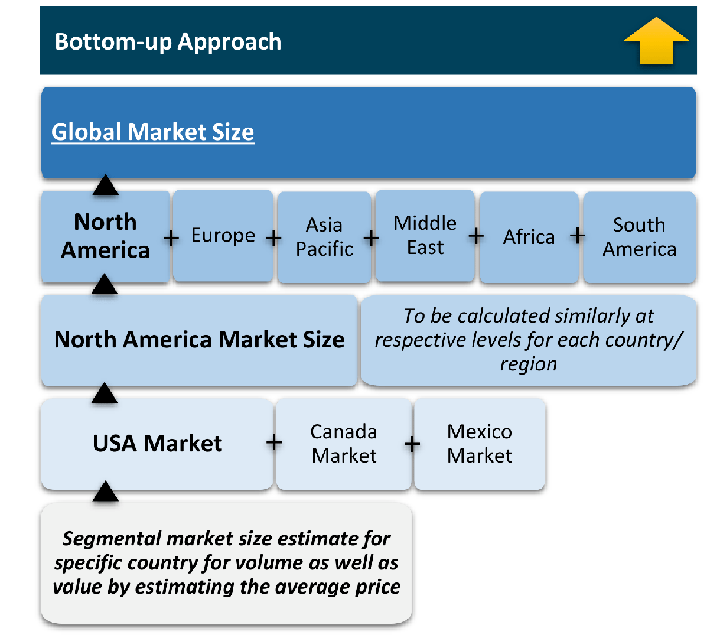
The bottom-up approach builds market estimates by starting with the smallest addressable market units and systematically aggregating them to create comprehensive market size projections.
This method begins with specific, granular data points and builds upward to create the complete market landscape.
Customer Analysis → Segmental Analysis → Geographical Analysis
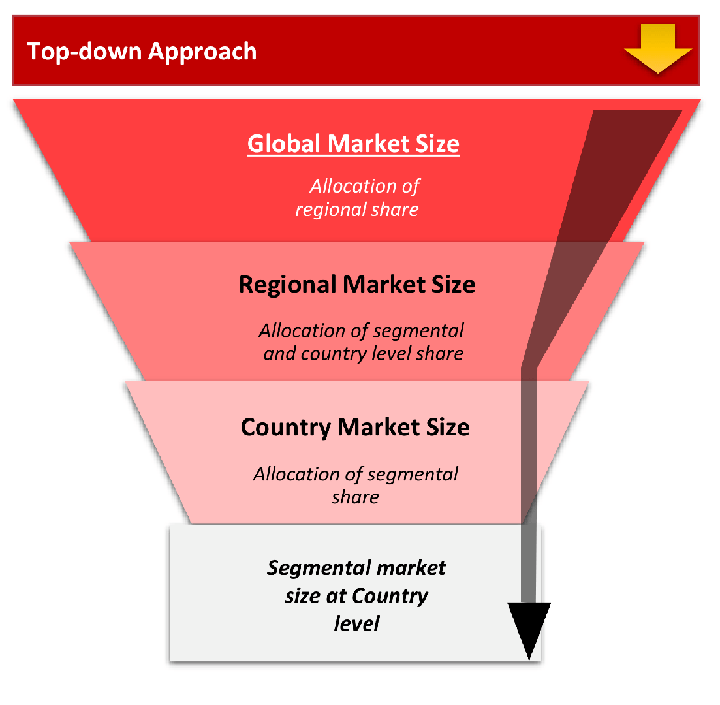
The top-down approach starts with the broadest possible market data and systematically narrows it down through a series of filters and assumptions to arrive at specific market segments or opportunities.
This method begins with the big picture and works downward to increasingly specific market slices.
TAM → SAM → SOM
While analysing the market, we extensively study secondary sources, directories, and databases to identify and collect information useful for this technical, market-oriented, and commercial report. Secondary sources that we utilize are not only the public sources, but it is combination of Open Source, Associations, Paid Databases, MG Repository & Knowledgebase and Others.
- Company websites, annual reports, financial reports, broker reports, and investor presentations
- National government documents, statistical databases and reports
- News articles, press releases and web-casts specific to the companies operating in the market, Magazines, reports, and others
- We gather information from commercial data sources for deriving company specific data such as segmental revenue, share for geography, product revenue, and others
- Internal and external proprietary databases (industry-specific), relevant patent, and regulatory databases
- Governing Bodies, Government Organizations
- Relevant Authorities, Country-specific Associations for Industries
We also employ the model mapping approach to estimate the product level market data through the players product portfolio
Primary research/ interviews is vital in analyzing the market. Most of the cases involves paid primary interviews. Primary sources includes primary interviews through e-mail interactions, telephonic interviews, surveys as well as face-to-face interviews with the different stakeholders across the value chain including several industry experts.
| Type of Respondents | Number of Primaries |
|---|---|
| Tier 2/3 Suppliers | ~20 |
| Tier 1 Suppliers | ~25 |
| End-users | ~25 |
| Industry Expert/ Panel/ Consultant | ~30 |
| Total | ~100 |
MG Knowledgebase
• Repository of industry blog, newsletter and case studies
• Online platform covering detailed market reports, and company profiles
- Historical Trends – Past market patterns, cycles, and major events that shaped how markets behave over time. Understanding past trends helps predict future behavior.
- Industry Factors – Specific characteristics of the industry like structure, regulations, and innovation cycles that affect market dynamics.
- Macroeconomic Factors – Economic conditions like GDP growth, inflation, and employment rates that affect how much money people have to spend.
- Demographic Factors – Population characteristics like age, income, and location that determine who can buy your product.
- Technology Factors – How quickly people adopt new technology and how much technology infrastructure exists.
- Regulatory Factors – Government rules, laws, and policies that can help or restrict market growth.
- Competitive Factors – Analyzing competition structure such as degree of competition and bargaining power of buyers and suppliers.
Multiple Regression Analysis
- Identify and quantify factors that drive market changes
- Statistical modeling to establish relationships between market drivers and outcomes
Time Series Analysis – Seasonal Patterns
- Understand regular cyclical patterns in market demand
- Advanced statistical techniques to separate trend, seasonal, and irregular components
Time Series Analysis – Trend Analysis
- Identify underlying market growth patterns and momentum
- Statistical analysis of historical data to project future trends
Expert Opinion – Expert Interviews
- Gather deep industry insights and contextual understanding
- In-depth interviews with key industry stakeholders
Multi-Scenario Development
- Prepare for uncertainty by modeling different possible futures
- Creating optimistic, pessimistic, and most likely scenarios
Time Series Analysis – Moving Averages
- Sophisticated forecasting for complex time series data
- Auto-regressive integrated moving average models with seasonal components
Econometric Models
- Apply economic theory to market forecasting
- Sophisticated economic models that account for market interactions
Expert Opinion – Delphi Method
- Harness collective wisdom of industry experts
- Structured, multi-round expert consultation process
Monte Carlo Simulation
- Quantify uncertainty and probability distributions
- Thousands of simulations with varying input parameters
Our research framework is built upon the fundamental principle of validating market intelligence from both demand and supply perspectives. This dual-sided approach ensures comprehensive market understanding and reduces the risk of single-source bias.
Demand-Side Analysis: We understand end-user/application behavior, preferences, and market needs along with the penetration of the product for specific application.
Supply-Side Analysis: We estimate overall market revenue, analyze the segmental share along with industry capacity, competitive landscape, and market structure.
Data triangulation is a validation technique that uses multiple methods, sources, or perspectives to examine the same research question, thereby increasing the credibility and reliability of research findings. In market research, triangulation serves as a quality assurance mechanism that helps identify and minimize bias, validate assumptions, and ensure accuracy in market estimates.
- Data Source Triangulation – Using multiple data sources to examine the same phenomenon
- Methodological Triangulation – Using multiple research methods to study the same research question
- Investigator Triangulation – Using multiple researchers or analysts to examine the same data
- Theoretical Triangulation – Using multiple theoretical perspectives to interpret the same data