Industrial Control System Security Market Size, Share & Trends Analysis Report by Component (Hardware, Software, Services), Security Type, Deployment Mode, Control System Type, Communication Protocol, Threat Type, End-Use Industry, and Geography (North America, Europe, Asia Pacific, Middle East, Africa, and South America) – Global Industry Data, Trends, and Forecasts, 2025 – 2035
|
Market Structure & Evolution |
|
|
Segmental Data Insights |
|
|
Demand Trends |
|
|
Competitive Landscape |
|
|
Strategic Development |
|
|
Future Outlook & Opportunities |
|
Industrial Control System Security Market Size, Share, and Growth
The global industrial control system security market is experiencing robust growth, with its estimated value of USD 17.8 billion in the year 2025 and USD 48.3 billion by the period 2035, registering a CAGR of 10.5% during the forecast period. The need of the security of industrial control systems is mainly predetermined by the growing number of cyberattacks on the critical infrastructures, the growing digitalization of industrial processes, and the involvement of IoT and cloud technologies. The rising government regulations to ensure compliance with cybersecurity and the proliferation of remote monitoring systems also facilitate the adoption, which guarantees the continuity of operations, integrity, and safety of data throughout the industrial industry.

Nozomi Networks Co-founder and CPO Andrea Carcano, stated: "We're honored to partner with innovator and industry leader Mitsubishi Electric to bring Arc Embedded to their PLCs, Arc Embedded can transform how CISOs manage and protect critical infrastructure, extending security to and through industrial control systems, down to the field assets they manage."
The global industrial control system security market is evolving at a high pace as operators of critical infrastructure step up to secure automation networks against increased cyber threats and ransomware attacks. The increasing implementation of IoT, cloud and remote access in manufacturing, energy and utilities have raised vulnerability levels that require industries to enact proactive defense architectures. In April 2025, Honeywell launched its new product called Cyber Insights, which offers real-time visibility and threat analytics to industrial settings to enhance operational resilience.
In the same way, in February 2025, Siemens announced the Siemens Industrial Defender X, which combines zero-trust architecture and AI-based anomaly detection to secure the control systems of processes in the energy and transportation industries. The merging of IT and OT security plans along with increasing the global regulations on cybersecurity keeps on accelerating technological use and innovativeness among vendors.
Adjacent markets to industrial control system security include operational technology (OT) cybersecurity services, industrial IoT platforms, secure network infrastructure, digital twin–based monitoring, and AI-driven predictive maintenance solutions. Expanding adjacent technologies amplify cybersecurity scope, fostering integrated, intelligent, and proactive industrial defense ecosystems.
Industrial Control System Security Market Dynamics and Trends

Driver: Rapid Digitalization and Convergence of IT and OT Environments
- The ever increasing interdependence between operational technology (OT) and information technology (IT) is increasing the need to have strong ICS security solutions. The manufacturing, energy, and other critical infrastructure industries are also becoming more and more dependent on integrated networks to improve the efficiency of their operations, which leaves them susceptible to cybercriminals.
- At the beginning of 2025, Honeywell enhanced its collaboration with Dragos in order to improve the field of industrial cybersecurity with the use of advanced threat detection platforms designed to operate in OT setups. On the same note, ABB incorporated AI-based anomaly detection software into its automation networks in order to detect possible intrusions within an organization in real-time.
- This merging has seen cybersecurity become a central component of operational strategy, which ensures resilience and adherence to the international security standards that are transforming.
Restraint: Complexity and Cost of Deploying Comprehensive ICS Security Frameworks
- Deployment of ICS security in large industrial facilities is still a challenge because of the legacy systems and the high costs of integration. Most key infrastructure, including power systems and refineries, still use decades-old controls, which are not easily modified to meet current cybersecurity standards.
- Rockwell Automation stated in 2025 that it was encountering operational challenges with clients that were adopting the use of new zero-trust architecture into the old SCADA networks. Similarly, Schneider Electric referred to the fact that compliance should be aligned on the global level according to the ISA/IEC 62443 framework and it takes a lot of capital and training to achieve it.
- It is also hard to scale the market due to the complexity of the solution customization in various operational environments, which is why the deployment cycles are longer.
Opportunity: Integration of AI and Predictive Analytics for Threat Intelligence
- ICS security is changing with the advent of artificial intelligence and predictive analytics, which allows identifying and responding to threats proactively. In 2025, Siemens launched an AI-assisted cyber defense unit in the Digital Industries department, which was providing real-time predictive analytics on industrial networks.
- Equally, Nozomi Networks added machine learning algorithms to its Guardian platform in order to detect subtle behavioral anomalies in the process control environment. Such improvements enable operators to prevent possible attacks before they lead to inconvenience especially in industries such as oil and gas and water and electricity suppliers whose downtime is very expensive.
- The increased focus on AI-based, autonomous defense solutions is a profitable avenue to vendors to provide scalable, adaptative security solutions on the international level.
Key Trend: Government-Led Cybersecurity Mandates and Industry Collaboration Initiatives
- Governments around the world are increasing regulatory control and promoting industry co-operation to enhance ICS protection. In 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) extended its crusade on cybersecurity, which is known as the Secure by Design initiative, to industrial manufacturers, compelling it to integrate cybersecurity into the design of their products.
- At the same time, the European Union Agency on Cybersecurity (ENISA) presented the new compliance standards according to the NIS2 directive with the focus on supply chain resiliency and incident response guidelines. The OT Cybersecurity Coalition, consisting of the collaboration of such firms as Claroty and Dragos, is a private sector alliance that promotes a single defense standard.
- These joint programs are establishing an integrated security environment, where industrial processes address new compliance and resilience requirements.
Industrial Control System Security Market Analysis and Segmental Data

Critical Infrastructure Under Siege: Securing the Energy Backbone
- The energy and power industry have the greatest requirements of industrial control system security, since this system is most frequently and most often targeted with attacks of complex and sophisticated cyber-attacks aimed at grids, substations, and SCADA systems. In 2025, Schneider Electric partnered with IBM Security to enhance the ability of cyber defense against smart grid operators by embedding AI based monitoring tools into the substation control systems.
- In March 2025, GE Vernova unveiled superior security modules as part of its digital power platforms, with encryption and anomaly detection of renewable energy activities. With modern energy networks that are becoming smart grids and distributed generation, cybersecurity is becoming an irredeemable component of reliability and national resilience.
- The increasing cyber exposure of critical energy infrastructure is accelerating the implementation of ICS security in the worldwide energy market.
Cyber Defense Modernization Fuels North American ICS Security Demand
- North America has the highest demand of industrial control system security market, because the region has one of the largest adoptions of digitalized critical infrastructure and is exposed to threats of state-sponsored and ransomware attacks. In August 2025, Honeywell developed its Cyber Watch system of industrial establishments in the U.S., with additions of advanced threat identification and automated reaction, to reduce the downtime of work in utilities and manufacturing industries. It underscores the proactive nature of the region in responding to the ever-efficient attacks on industrial networks.
- Rockwell Automation opened a new OT cybersecurity operation center in June 2025 in Texas to assist industrial clients with real-time operations and monitoring around-the-clock and management compliance. These developments can be said to be a strong indication of the regional determination to protect the national infrastructure and ensure that industries remain resilient to the changing threat environment.
- The focus on digitalizing industries and regulatory-based cybersecurity measures in the region perpetuates the leadership of North America in ICS security adoption.
Industrial Control System Security Market Ecosystem
Global industrial control system security market is moderately consolidated, and major players, which include ABB Ltd., Cisco Systems, Inc., Honeywell International Inc., Schneider Electric SE, Siemens AG, and Palo Alto Networks, Inc., with sophisticated cybersecurity architecture and AI-based threat detection systems control the market. These companies also apply their technological strengths to capture the important industrial infrastructures and provide solutions to industries in the form of energy, manufacturing, oil and gas, and utilities.
Key players are increasingly focusing on specialized cybersecurity solutions such as anomaly detection software, zero-trust frameworks, and network segmentation technologies to enhance resilience against cyber threats. For instance, Claroty Ltd. and Nozomi Networks Inc. have developed ICS-specific monitoring platforms that use deep packet inspection to detect real-time vulnerabilities across operational environments.
Government agencies and research institutions are also playing a critical role in shaping this market. In March 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) launched a new initiative integrating AI and behavioral analytics into critical infrastructure protection systems, improving incident response efficiency and reducing attack response times by 30%. Key players are simultaneously pursuing product diversification and ecosystem partnerships to provide integrated security platforms that combine IT and OT defense mechanisms, ensuring end-to-end industrial protection.

Recent Development and Strategic Overview:
- In May 2025, ABB Ltd. and Red Hat, extended collaboration to develop automation systems for the future of industrial IT, enabling more secure and modular deployment of control applications for process industries. The collaboration bridges the IT/OT divide, enhancing predictive insights and real-time monitoring to boost asset performance and operational visibility.
- In May 2025, Honeywell announced partnership with Nutanix, to deliver modernized, secure, and scalable infrastructure for Honeywell’s Integrated Control and Safety System (ICSS). This collaboration will enable enterprises across critical sectors to accelerate digital transformation while enhancing operational efficiency, cybersecurity, and resilience.
Report Scope
|
Attribute |
Detail |
|
Market Size in 2025 |
USD 17.8 Bn |
|
Market Forecast Value in 2035 |
USD 48.3 Bn |
|
Growth Rate (CAGR) |
10.5% |
|
Forecast Period |
2025 – 2035 |
|
Historical Data Available for |
2021 – 2024 |
|
Market Size Units |
US$ Billion for Value |
|
Report Format |
Electronic (PDF) + Excel |
|
Regions and Countries Covered |
|||||
|
North America |
Europe |
Asia Pacific |
Middle East |
Africa |
South America |
|
|
|
|
|
|
|
Companies Covered |
|||||
|
|
|
|
|
|
Industrial Control System Security Market Segmentation and Highlights
|
Segment |
Sub-segment |
|
Industrial Control System Security Market, By Component |
|
|
Industrial Control System Security Market, By Security Type |
|
|
Industrial Control System Security Market, By Deployment Mode |
|
|
Industrial Control System Security Market, By Control System Type |
|
|
Industrial Control System Security Market, By Communication Protocol |
|
|
Industrial Control System Security Market, By Threat Type |
|
|
Industrial Control System Security Market, By End-Use Industry |
|
Frequently Asked Questions
The global industrial control system security market was valued at USD 17.8 Bn in 2025
The global industrial control system security market industry is expected to grow at a CAGR of 10.5% from 2025 to 2035
Rising cyberattacks on critical infrastructure, rapid digitalization of industrial assets, regulatory mandates, and adoption of smart grids and IIoT technologies are major factors driving strong global demand for industrial control system security.
In terms of end-use industry, the energy & power segment accounted for the major share in 2025
North America is a more attractive region for vendors
Key players in the global industrial control system security market include prominent companies such as ABB Ltd., Check Point Software Technologies Ltd., Cisco Systems, Inc., Claroty Ltd., CyberArk Software Ltd., Darktrace plc, Dragos, Inc., Emerson Electric Co., FireEye, Inc. (Mandiant), Fortinet, Inc., Honeywell International Inc., IBM Corporation, Kaspersky Lab, McAfee, LLC, Nozomi Networks Inc., Palo Alto Networks, Inc., Rapid7, Inc., Rockwell Automation, Inc., Schneider Electric SE, Siemens AG, Symantec Corporation, Tenable, Inc., Trend Micro Incorporated, and Other Key Players
Table of Contents
- 1. Research Methodology and Assumptions
- 1.1. Definitions
- 1.2. Research Design and Approach
- 1.3. Data Collection Methods
- 1.4. Base Estimates and Calculations
- 1.5. Forecasting Models
- 1.5.1. Key Forecast Factors & Impact Analysis
- 1.6. Secondary Research
- 1.6.1. Open Sources
- 1.6.2. Paid Databases
- 1.6.3. Associations
- 1.7. Primary Research
- 1.7.1. Primary Sources
- 1.7.2. Primary Interviews with Stakeholders across Ecosystem
- 2. Executive Summary
- 2.1. Global Industrial Control System Security Market Outlook
- 2.1.1. Industrial Control System Security Market Size (Value - US$ Bn), and Forecasts, 2021-2035
- 2.1.2. Compounded Annual Growth Rate Analysis
- 2.1.3. Growth Opportunity Analysis
- 2.1.4. Segmental Share Analysis
- 2.1.5. Geographical Share Analysis
- 2.2. Market Analysis and Facts
- 2.3. Supply-Demand Analysis
- 2.4. Competitive Benchmarking
- 2.5. Go-to- Market Strategy
- 2.5.1. Customer/ End-use Industry Assessment
- 2.5.2. Growth Opportunity Data, 2025-2035
- 2.5.2.1. Regional Data
- 2.5.2.2. Country Data
- 2.5.2.3. Segmental Data
- 2.5.3. Identification of Potential Market Spaces
- 2.5.4. GAP Analysis
- 2.5.5. Potential Attractive Price Points
- 2.5.6. Prevailing Market Risks & Challenges
- 2.5.7. Preferred Sales & Marketing Strategies
- 2.5.8. Key Recommendations and Analysis
- 2.5.9. A Way Forward
- 2.1. Global Industrial Control System Security Market Outlook
- 3. Industry Data and Premium Insights
- 3.1. Global Industrial Control System Security Industry Overview, 2025
- 3.1.1. Automation & Process Control Industry Ecosystem Analysis
- 3.1.2. Key Trends for Automation & Process Control Industry
- 3.1.3. Regional Distribution for Automation & Process Control Industry
- 3.2. Supplier Customer Data
- 3.3. Technology Roadmap and Developments
- 3.4. Trade Analysis
- 3.4.1. Import & Export Analysis, 2025
- 3.4.2. Top Importing Countries
- 3.4.3. Top Exporting Countries
- 3.5. Trump Tariff Impact Analysis
- 3.5.1. Manufacturer
- 3.5.1.1. Based on the component & Raw material
- 3.5.2. Supply Chain
- 3.5.3. End Consumer
- 3.5.1. Manufacturer
- 3.6. Raw Material Analysis
- 3.1. Global Industrial Control System Security Industry Overview, 2025
- 4. Market Overview
- 4.1. Market Dynamics
- 4.1.1. Drivers
- 4.1.1.1. Increasing frequency and sophistication of cyberattacks on industrial infrastructure
- 4.1.1.2. Growing integration of IoT and cloud technologies in operational environments
- 4.1.1.3. Rising regulatory compliance requirements for critical infrastructure protection
- 4.1.2. Restraints
- 4.1.2.1. High deployment and maintenance costs of advanced ICS security solutions
- 4.1.2.2. Limited skilled workforce with expertise in OT and cybersecurity convergence
- 4.1.1. Drivers
- 4.2. Key Trend Analysis
- 4.3. Regulatory Framework
- 4.3.1. Key Regulations, Norms, and Subsidies, by Key Countries
- 4.3.2. Tariffs and Standards
- 4.3.3. Impact Analysis of Regulations on the Market
- 4.4. Value Chain Analysis
- 4.4.1. Component Suppliers
- 4.4.2. Industrial Control System Security Providers
- 4.4.3. System Integrators
- 4.4.4. Dealers/ Distributors
- 4.4.5. End-users/ Customers
- 4.5. Cost Structure Analysis
- 4.6. Pricing Analysis
- 4.7. Porter’s Five Forces Analysis
- 4.8. PESTEL Analysis
- 4.9. Global Industrial Control System Security Market Demand
- 4.9.1. Historical Market Size – in Value (US$ Bn), 2020-2024
- 4.9.2. Current and Future Market Size - in Value (US$ Bn), 2025–2035
- 4.9.2.1. Y-o-Y Growth Trends
- 4.9.2.2. Absolute $ Opportunity Assessment
- 4.1. Market Dynamics
- 5. Competition Landscape
- 5.1. Competition structure
- 5.1.1. Fragmented v/s consolidated
- 5.2. Company Share Analysis, 2025
- 5.2.1. Global Company Market Share
- 5.2.2. By Region
- 5.2.2.1. North America
- 5.2.2.2. Europe
- 5.2.2.3. Asia Pacific
- 5.2.2.4. Middle East
- 5.2.2.5. Africa
- 5.2.2.6. South America
- 5.3. Product Comparison Matrix
- 5.3.1. Specifications
- 5.3.2. Market Positioning
- 5.3.3. Pricing
- 5.1. Competition structure
- 6. Global Industrial Control System Security Market Analysis, by Component
- 6.1. Key Segment Analysis
- 6.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by M Component, 2021-2035
- 6.2.1. Hardware
- 6.2.1.1. Firewalls
- 6.2.1.2. Intrusion Detection Systems (IDS)
- 6.2.1.3. Intrusion Prevention Systems (IPS)
- 6.2.1.4. Security Gateways
- 6.2.1.5. Routers and Switches
- 6.2.1.6. Encryption Devices
- 6.2.1.7. Others
- 6.2.2. Software
- 6.2.2.1. SCADA Security Software
- 6.2.2.2. Application Whitelisting
- 6.2.2.3. Antivirus/Anti-malware
- 6.2.2.4. Security Information and Event Management (SIEM)
- 6.2.2.5. Vulnerability Management Software
- 6.2.2.6. Configuration Management Software
- 6.2.2.7. Others
- 6.2.3. Services
- 6.2.3.1. Professional Services
- 6.2.3.1.1. Consulting
- 6.2.3.1.2. Implementation and Integration
- 6.2.3.1.3. Training and Education
- 6.2.3.2. Managed Services
- 6.2.3.2.1. Monitoring Services
- 6.2.3.2.2. Incident Response Services
- 6.2.3.2.3. Threat Intelligence Services
- 6.2.3.1. Professional Services
- 6.2.1. Hardware
- 7. Global Industrial Control System Security Market Analysis, by Security Type
- 7.1. Key Segment Analysis
- 7.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by Security Type, 2021-2035
- 7.2.1. Network Security
- 7.2.2. Endpoint Security
- 7.2.3. Application Security
- 7.2.4. Database Security
- 7.2.5. Cloud Security
- 7.2.6. Wireless Security
- 8. Global Industrial Control System Security Market Analysis, by Deployment Mode
- 8.1. Key Segment Analysis
- 8.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by Deployment Mode, 2021-2035
- 8.2.1. On-Premises
- 8.2.2. Cloud-Based
- 8.2.3. Hybrid
- 9. Global Industrial Control System Security Market Analysis, by Control System Type
- 9.1. Key Segment Analysis
- 9.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by Control System Type, 2021-2035
- 9.2.1. Supervisory Control and Data Acquisition (SCADA)
- 9.2.2. Distributed Control System (DCS)
- 9.2.3. Programmable Logic Controller (PLC)
- 9.2.4. Human Machine Interface (HMI)
- 9.2.5. Remote Terminal Units (RTU)
- 9.2.6. Safety Instrumented Systems (SIS)
- 9.2.7. Product Lifecycle Management (PLM)
- 9.2.8. Manufacturing Execution Systems (MES)
- 9.2.9. Others
- 10. Global Industrial Control System Security Market Analysis, by Communication Protocol
- 10.1. Key Segment Analysis
- 10.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by Communication Protocol, 2021-2035
- 10.2.1. Modbus
- 10.2.2. DNP3
- 10.2.3. OPC
- 10.2.4. PROFINET
- 10.2.5. EtherNet/IP
- 10.2.6. BACnet
- 10.2.7. HART
- 10.2.8. Foundation Fieldbus
- 10.2.9. Others
- 11. Global Industrial Control System Security Market Analysis, by Threat Type
- 11.1. Key Segment Analysis
- 11.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by Voltage Range, 2021-2035
- 11.2.1. Malware and Ransomware
- 11.2.2. Distributed Denial of Service (DDoS)
- 11.2.3. Advanced Persistent Threats (APT)
- 11.2.4. Insider Threats
- 11.2.5. Phishing and Social Engineering
- 11.2.6. Zero-Day Exploits
- 11.2.7. Man-in-the-Middle Attacks
- 11.2.8. Others
- 12. Global Industrial Control System Security Market Analysis, by End-Use Industry
- 12.1. Key Segment Analysis
- 12.2. Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, by End-Use Industry, 2021-2035
- 12.2.1. Energy & Power
- 12.2.1.1. Power Generation Monitoring
- 12.2.1.2. Transmission & Distribution Control
- 12.2.1.3. Smart Grid Security
- 12.2.1.4. Renewable Energy Management
- 12.2.1.5. Nuclear Facility Protection
- 12.2.1.6. Others
- 12.2.2. Oil & Gas
- 12.2.2.1. Upstream Operations
- 12.2.2.2. Midstream Operations
- 12.2.2.3. Downstream Operations
- 12.2.2.4. Offshore Platform Security
- 12.2.2.5. Storage Facility Protection
- 12.2.2.6. Others
- 12.2.3. Manufacturing
- 12.2.3.1. Discrete Manufacturing
- 12.2.3.2. Process Manufacturing
- 12.2.3.3. Assembly Line Control
- 12.2.3.4. Quality Control Systems
- 12.2.3.5. Inventory Management
- 12.2.3.6. Production Planning
- 12.2.3.7. Others
- 12.2.4. Water & Wastewater Treatment
- 12.2.4.1. Water Quality Monitoring
- 12.2.4.2. Distribution System Control
- 12.2.4.3. Treatment Process Automation
- 12.2.4.4. Pump Station Management
- 12.2.4.5. Leak Detection Systems
- 12.2.4.6. Others
- 12.2.5. Transportation
- 12.2.5.1. Railway Signaling Systems
- 12.2.5.2. Traffic Management Systems
- 12.2.5.3. Airport Operations
- 12.2.5.4. Port and Harbor Management
- 12.2.5.5. Metro and Subway Control
- 12.2.5.6. Others
- 12.2.6. Chemical & Petrochemical
- 12.2.6.1. Process Control and Optimization
- 12.2.6.2. Safety System Management
- 12.2.6.3. Material Handling
- 12.2.6.4. Batch Processing Control
- 12.2.6.5. Others
- 12.2.7. Food & Beverages
- 12.2.8. Pharmaceutical & Healthcare
- 12.2.9. Metals & Mining
- 12.2.10. Automotive
- 12.2.11. Building Automation
- 12.2.12. Data Centers
- 12.2.13. Other Industries
- 12.2.1. Energy & Power
- 13. Global Industrial Control System Security Market Analysis, by Region
- 13.1. Key Findings
- 13.2. Industrial Control System Security Market Size (Value - US$ Mn), Analysis, and Forecasts, by Region, 2021-2035
- 13.2.1. North America
- 13.2.2. Europe
- 13.2.3. Asia Pacific
- 13.2.4. Middle East
- 13.2.5. Africa
- 13.2.6. South America
- 14. North America Industrial Control System Security Market Analysis
- 14.1. Key Segment Analysis
- 14.2. Regional Snapshot
- 14.3. North America Industrial Control System Security Market Size Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 14.3.1. Component
- 14.3.2. Security Type
- 14.3.3. Deployment Mode
- 14.3.4. Control System Type
- 14.3.5. Communication Protocol
- 14.3.6. Threat Type
- 14.3.7. End-Use Industry
- 14.3.8. Country
- 14.3.8.1. USA
- 14.3.8.2. Canada
- 14.3.8.3. Mexico
- 14.4. USA Industrial Control System Security Market
- 14.4.1. Country Segmental Analysis
- 14.4.2. Component
- 14.4.3. Security Type
- 14.4.4. Deployment Mode
- 14.4.5. Control System Type
- 14.4.6. Communication Protocol
- 14.4.7. Threat Type
- 14.4.8. End-Use Industry
- 14.5. Canada Industrial Control System Security Market
- 14.5.1. Country Segmental Analysis
- 14.5.2. Component
- 14.5.3. Security Type
- 14.5.4. Deployment Mode
- 14.5.5. Control System Type
- 14.5.6. Communication Protocol
- 14.5.7. Threat Type
- 14.5.8. End-Use Industry
- 14.6. Mexico Industrial Control System Security Market
- 14.6.1. Country Segmental Analysis
- 14.6.2. Component
- 14.6.3. Security Type
- 14.6.4. Deployment Mode
- 14.6.5. Control System Type
- 14.6.6. Communication Protocol
- 14.6.7. Threat Type
- 14.6.8. End-Use Industry
- 15. Europe Industrial Control System Security Market Analysis
- 15.1. Key Segment Analysis
- 15.2. Regional Snapshot
- 15.3. Europe Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 15.3.1. Component
- 15.3.2. Security Type
- 15.3.3. Deployment Mode
- 15.3.4. Control System Type
- 15.3.5. Communication Protocol
- 15.3.6. Threat Type
- 15.3.7. End-Use Industry
- 15.3.8. Country
- 15.3.8.1. Germany
- 15.3.8.2. United Kingdom
- 15.3.8.3. France
- 15.3.8.4. Italy
- 15.3.8.5. Spain
- 15.3.8.6. Netherlands
- 15.3.8.7. Nordic Countries
- 15.3.8.8. Poland
- 15.3.8.9. Russia & CIS
- 15.3.8.10. Rest of Europe
- 15.4. Germany Industrial Control System Security Market
- 15.4.1. Country Segmental Analysis
- 15.4.2. Component
- 15.4.3. Security Type
- 15.4.4. Deployment Mode
- 15.4.5. Control System Type
- 15.4.6. Communication Protocol
- 15.4.7. Threat Type
- 15.4.8. End-Use Industry
- 15.5. United Kingdom Industrial Control System Security Market
- 15.5.1. Country Segmental Analysis
- 15.5.2. Component
- 15.5.3. Security Type
- 15.5.4. Deployment Mode
- 15.5.5. Control System Type
- 15.5.6. Communication Protocol
- 15.5.7. Threat Type
- 15.5.8. End-Use Industry
- 15.6. France Industrial Control System Security Market
- 15.6.1. Country Segmental Analysis
- 15.6.2. Component
- 15.6.3. Security Type
- 15.6.4. Deployment Mode
- 15.6.5. Control System Type
- 15.6.6. Communication Protocol
- 15.6.7. Threat Type
- 15.6.8. End-Use Industry
- 15.7. Italy Industrial Control System Security Market
- 15.7.1. Country Segmental Analysis
- 15.7.2. Component
- 15.7.3. Security Type
- 15.7.4. Deployment Mode
- 15.7.5. Control System Type
- 15.7.6. Communication Protocol
- 15.7.7. Threat Type
- 15.7.8. End-Use Industry
- 15.8. Spain Industrial Control System Security Market
- 15.8.1. Country Segmental Analysis
- 15.8.2. Component
- 15.8.3. Security Type
- 15.8.4. Deployment Mode
- 15.8.5. Control System Type
- 15.8.6. Communication Protocol
- 15.8.7. Threat Type
- 15.8.8. End-Use Industry
- 15.9. Netherlands Industrial Control System Security Market
- 15.9.1. Country Segmental Analysis
- 15.9.2. Component
- 15.9.3. Security Type
- 15.9.4. Deployment Mode
- 15.9.5. Control System Type
- 15.9.6. Communication Protocol
- 15.9.7. Threat Type
- 15.9.8. End-Use Industry
- 15.10. Nordic Countries Industrial Control System Security Market
- 15.10.1. Country Segmental Analysis
- 15.10.2. Component
- 15.10.3. Security Type
- 15.10.4. Deployment Mode
- 15.10.5. Control System Type
- 15.10.6. Communication Protocol
- 15.10.7. Threat Type
- 15.10.8. End-Use Industry
- 15.11. Poland Industrial Control System Security Market
- 15.11.1. Country Segmental Analysis
- 15.11.2. Component
- 15.11.3. Security Type
- 15.11.4. Deployment Mode
- 15.11.5. Control System Type
- 15.11.6. Communication Protocol
- 15.11.7. Threat Type
- 15.11.8. End-Use Industry
- 15.12. Russia & CIS Industrial Control System Security Market
- 15.12.1. Country Segmental Analysis
- 15.12.2. Component
- 15.12.3. Security Type
- 15.12.4. Deployment Mode
- 15.12.5. Control System Type
- 15.12.6. Communication Protocol
- 15.12.7. Threat Type
- 15.12.8. End-Use Industry
- 15.13. Rest of Europe Industrial Control System Security Market
- 15.13.1. Country Segmental Analysis
- 15.13.2. Component
- 15.13.3. Security Type
- 15.13.4. Deployment Mode
- 15.13.5. Control System Type
- 15.13.6. Communication Protocol
- 15.13.7. Threat Type
- 15.13.8. End-Use Industry
- 16. Asia Pacific Industrial Control System Security Market Analysis
- 16.1. Key Segment Analysis
- 16.2. Regional Snapshot
- 16.3. East Asia Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 16.3.1. Component
- 16.3.2. Security Type
- 16.3.3. Deployment Mode
- 16.3.4. Control System Type
- 16.3.5. Communication Protocol
- 16.3.6. Threat Type
- 16.3.7. End-Use Industry
- 16.3.8. Country
- 16.3.8.1. China
- 16.3.8.2. India
- 16.3.8.3. Japan
- 16.3.8.4. South Korea
- 16.3.8.5. Australia and New Zealand
- 16.3.8.6. Indonesia
- 16.3.8.7. Malaysia
- 16.3.8.8. Thailand
- 16.3.8.9. Vietnam
- 16.3.8.10. Rest of Asia Pacific
- 16.4. China Industrial Control System Security Market
- 16.4.1. Country Segmental Analysis
- 16.4.2. Component
- 16.4.3. Security Type
- 16.4.4. Deployment Mode
- 16.4.5. Control System Type
- 16.4.6. Communication Protocol
- 16.4.7. Threat Type
- 16.4.8. End-Use Industry
- 16.5. India Industrial Control System Security Market
- 16.5.1. Country Segmental Analysis
- 16.5.2. Component
- 16.5.3. Security Type
- 16.5.4. Deployment Mode
- 16.5.5. Control System Type
- 16.5.6. Communication Protocol
- 16.5.7. Threat Type
- 16.5.8. End-Use Industry
- 16.6. Japan Industrial Control System Security Market
- 16.6.1. Country Segmental Analysis
- 16.6.2. Component
- 16.6.3. Security Type
- 16.6.4. Deployment Mode
- 16.6.5. Control System Type
- 16.6.6. Communication Protocol
- 16.6.7. Threat Type
- 16.6.8. End-Use Industry
- 16.7. South Korea Industrial Control System Security Market
- 16.7.1. Country Segmental Analysis
- 16.7.2. Component
- 16.7.3. Security Type
- 16.7.4. Deployment Mode
- 16.7.5. Control System Type
- 16.7.6. Communication Protocol
- 16.7.7. Threat Type
- 16.7.8. End-Use Industry
- 16.8. Australia and New Zealand Industrial Control System Security Market
- 16.8.1. Country Segmental Analysis
- 16.8.2. Component
- 16.8.3. Security Type
- 16.8.4. Deployment Mode
- 16.8.5. Control System Type
- 16.8.6. Communication Protocol
- 16.8.7. Threat Type
- 16.8.8. End-Use Industry
- 16.9. Indonesia Industrial Control System Security Market
- 16.9.1. Country Segmental Analysis
- 16.9.2. Component
- 16.9.3. Security Type
- 16.9.4. Deployment Mode
- 16.9.5. Control System Type
- 16.9.6. Communication Protocol
- 16.9.7. Threat Type
- 16.9.8. End-Use Industry
- 16.10. Malaysia Industrial Control System Security Market
- 16.10.1. Country Segmental Analysis
- 16.10.2. Component
- 16.10.3. Security Type
- 16.10.4. Deployment Mode
- 16.10.5. Control System Type
- 16.10.6. Communication Protocol
- 16.10.7. Threat Type
- 16.10.8. End-Use Industry
- 16.11. Thailand Industrial Control System Security Market
- 16.11.1. Country Segmental Analysis
- 16.11.2. Component
- 16.11.3. Security Type
- 16.11.4. Deployment Mode
- 16.11.5. Control System Type
- 16.11.6. Communication Protocol
- 16.11.7. Threat Type
- 16.11.8. End-Use Industry
- 16.12. Vietnam Industrial Control System Security Market
- 16.12.1. Country Segmental Analysis
- 16.12.2. Component
- 16.12.3. Security Type
- 16.12.4. Deployment Mode
- 16.12.5. Control System Type
- 16.12.6. Communication Protocol
- 16.12.7. Threat Type
- 16.12.8. End-Use Industry
- 16.13. Rest of Asia Pacific Industrial Control System Security Market
- 16.13.1. Country Segmental Analysis
- 16.13.2. Component
- 16.13.3. Security Type
- 16.13.4. Deployment Mode
- 16.13.5. Control System Type
- 16.13.6. Communication Protocol
- 16.13.7. Threat Type
- 16.13.8. End-Use Industry
- 17. Middle East Industrial Control System Security Market Analysis
- 17.1. Key Segment Analysis
- 17.2. Regional Snapshot
- 17.3. Middle East Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 17.3.1. Component
- 17.3.2. Security Type
- 17.3.3. Deployment Mode
- 17.3.4. Control System Type
- 17.3.5. Communication Protocol
- 17.3.6. Threat Type
- 17.3.7. End-Use Industry
- 17.3.8. Country
- 17.3.8.1. Turkey
- 17.3.8.2. UAE
- 17.3.8.3. Saudi Arabia
- 17.3.8.4. Israel
- 17.3.8.5. Rest of Middle East
- 17.4. Turkey Industrial Control System Security Market
- 17.4.1. Country Segmental Analysis
- 17.4.2. Component
- 17.4.3. Security Type
- 17.4.4. Deployment Mode
- 17.4.5. Control System Type
- 17.4.6. Communication Protocol
- 17.4.7. Threat Type
- 17.4.8. End-Use Industry
- 17.5. UAE Industrial Control System Security Market
- 17.5.1. Country Segmental Analysis
- 17.5.2. Component
- 17.5.3. Security Type
- 17.5.4. Deployment Mode
- 17.5.5. Control System Type
- 17.5.6. Communication Protocol
- 17.5.7. Threat Type
- 17.5.8. End-Use Industry
- 17.6. Saudi Arabia Industrial Control System Security Market
- 17.6.1. Country Segmental Analysis
- 17.6.2. Component
- 17.6.3. Security Type
- 17.6.4. Deployment Mode
- 17.6.5. Control System Type
- 17.6.6. Communication Protocol
- 17.6.7. Threat Type
- 17.6.8. End-Use Industry
- 17.7. Israel Industrial Control System Security Market
- 17.7.1. Country Segmental Analysis
- 17.7.2. Component
- 17.7.3. Security Type
- 17.7.4. Deployment Mode
- 17.7.5. Control System Type
- 17.7.6. Communication Protocol
- 17.7.7. Threat Type
- 17.7.8. End-Use Industry
- 17.8. Rest of Middle East Industrial Control System Security Market
- 17.8.1. Country Segmental Analysis
- 17.8.2. Component
- 17.8.3. Security Type
- 17.8.4. Deployment Mode
- 17.8.5. Control System Type
- 17.8.6. Communication Protocol
- 17.8.7. Threat Type
- 17.8.8. End-Use Industry
- 18. Africa Industrial Control System Security Market Analysis
- 18.1. Key Segment Analysis
- 18.2. Regional Snapshot
- 18.3. Africa Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 18.3.1. Component
- 18.3.2. Security Type
- 18.3.3. Deployment Mode
- 18.3.4. Control System Type
- 18.3.5. Communication Protocol
- 18.3.6. Threat Type
- 18.3.7. End-Use Industry
- 18.3.8. Country
- 18.3.8.1. South Africa
- 18.3.8.2. Egypt
- 18.3.8.3. Nigeria
- 18.3.8.4. Algeria
- 18.3.8.5. Rest of Africa
- 18.4. South Africa Industrial Control System Security Market
- 18.4.1. Country Segmental Analysis
- 18.4.2. Component
- 18.4.3. Security Type
- 18.4.4. Deployment Mode
- 18.4.5. Control System Type
- 18.4.6. Communication Protocol
- 18.4.7. Threat Type
- 18.4.8. End-Use Industry
- 18.5. Egypt Industrial Control System Security Market
- 18.5.1. Country Segmental Analysis
- 18.5.2. Component
- 18.5.3. Security Type
- 18.5.4. Deployment Mode
- 18.5.5. Control System Type
- 18.5.6. Communication Protocol
- 18.5.7. Threat Type
- 18.5.8. End-Use Industry
- 18.6. Nigeria Industrial Control System Security Market
- 18.6.1. Country Segmental Analysis
- 18.6.2. Component
- 18.6.3. Security Type
- 18.6.4. Deployment Mode
- 18.6.5. Control System Type
- 18.6.6. Communication Protocol
- 18.6.7. Threat Type
- 18.6.8. End-Use Industry
- 18.7. Algeria Industrial Control System Security Market
- 18.7.1. Country Segmental Analysis
- 18.7.2. Component
- 18.7.3. Security Type
- 18.7.4. Deployment Mode
- 18.7.5. Control System Type
- 18.7.6. Communication Protocol
- 18.7.7. Threat Type
- 18.7.8. End-Use Industry
- 18.8. Rest of Africa Industrial Control System Security Market
- 18.8.1. Country Segmental Analysis
- 18.8.2. Component
- 18.8.3. Security Type
- 18.8.4. Deployment Mode
- 18.8.5. Control System Type
- 18.8.6. Communication Protocol
- 18.8.7. Threat Type
- 18.8.8. End-Use Industry
- 19. South America Industrial Control System Security Market Analysis
- 19.1. Key Segment Analysis
- 19.2. Regional Snapshot
- 19.3. Central and South Africa Industrial Control System Security Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 19.3.1. Component
- 19.3.2. Security Type
- 19.3.3. Deployment Mode
- 19.3.4. Control System Type
- 19.3.5. Communication Protocol
- 19.3.6. Threat Type
- 19.3.7. End-Use Industry
- 19.3.8. Country
- 19.3.8.1. Brazil
- 19.3.8.2. Argentina
- 19.3.8.3. Rest of South America
- 19.4. Brazil Industrial Control System Security Market
- 19.4.1. Country Segmental Analysis
- 19.4.2. Component
- 19.4.3. Security Type
- 19.4.4. Deployment Mode
- 19.4.5. Control System Type
- 19.4.6. Communication Protocol
- 19.4.7. Threat Type
- 19.4.8. End-Use Industry
- 19.5. Argentina Industrial Control System Security Market
- 19.5.1. Country Segmental Analysis
- 19.5.2. Component
- 19.5.3. Security Type
- 19.5.4. Deployment Mode
- 19.5.5. Control System Type
- 19.5.6. Communication Protocol
- 19.5.7. Threat Type
- 19.5.8. End-Use Industry
- 19.6. Rest of South America Industrial Control System Security Market
- 19.6.1. Country Segmental Analysis
- 19.6.2. Component
- 19.6.3. Security Type
- 19.6.4. Deployment Mode
- 19.6.5. Control System Type
- 19.6.6. Communication Protocol
- 19.6.7. Threat Type
- 19.6.8. End-Use Industry
- 20. Key Players/ Company Profile
- 20.1. ABB Ltd.
- 20.1.1. Company Details/ Overview
- 20.1.2. Company Financials
- 20.1.3. Key Customers and Competitors
- 20.1.4. Business/ Industry Portfolio
- 20.1.5. Product Portfolio/ Specification Details
- 20.1.6. Pricing Data
- 20.1.7. Strategic Overview
- 20.1.8. Recent Developments
- 20.2. Check Point Software Technologies Ltd.
- 20.3. Cisco Systems, Inc.
- 20.4. Claroty Ltd.
- 20.5. CyberArk Software Ltd.
- 20.6. Darktrace plc
- 20.7. Dragos, Inc.
- 20.8. Emerson Electric Co.
- 20.9. FireEye, Inc.
- 20.10. Fortinet, Inc.
- 20.11. Honeywell International Inc.
- 20.12. IBM Corporation
- 20.13. Kaspersky Lab
- 20.14. McAfee, LLC
- 20.15. Nozomi Networks Inc.
- 20.16. Palo Alto Networks, Inc.
- 20.17. Rapid7, Inc.
- 20.18. Rockwell Automation, Inc.
- 20.19. Schneider Electric SE
- 20.20. Siemens AG
- 20.21. Symantec Corporation
- 20.22. Tenable, Inc.
- 20.23. Trend Micro Incorporated
- 20.24. Other Key Players
- 20.1. ABB Ltd.
Note* - This is just tentative list of players. While providing the report, we will cover more number of players based on their revenue and share for each geography
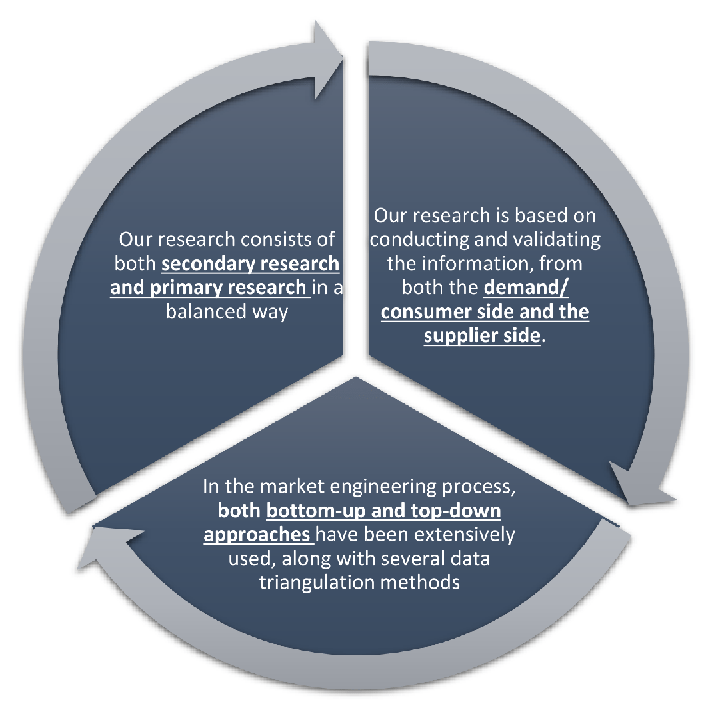
Our research design integrates both demand-side and supply-side analysis through a balanced combination of primary and secondary research methodologies. By utilizing both bottom-up and top-down approaches alongside rigorous data triangulation methods, we deliver robust market intelligence that supports strategic decision-making.
MarketGenics' comprehensive research design framework ensures the delivery of accurate, reliable, and actionable market intelligence. Through the integration of multiple research approaches, rigorous validation processes, and expert analysis, we provide our clients with the insights needed to make informed strategic decisions and capitalize on market opportunities.
MarketGenics leverages a dedicated industry panel of experts and a comprehensive suite of paid databases to effectively collect, consolidate, and analyze market intelligence.
Our approach has consistently proven to be reliable and effective in generating accurate market insights, identifying key industry trends, and uncovering emerging business opportunities.
Through both primary and secondary research, we capture and analyze critical company-level data such as manufacturing footprints, including technical centers, R&D facilities, sales offices, and headquarters.
Our expert panel further enhances our ability to estimate market size for specific brands based on validated field-level intelligence.
Our data mining techniques incorporate both parametric and non-parametric methods, allowing for structured data collection, sorting, processing, and cleaning.
Demand projections are derived from large-scale data sets analyzed through proprietary algorithms, culminating in robust and reliable market sizing.
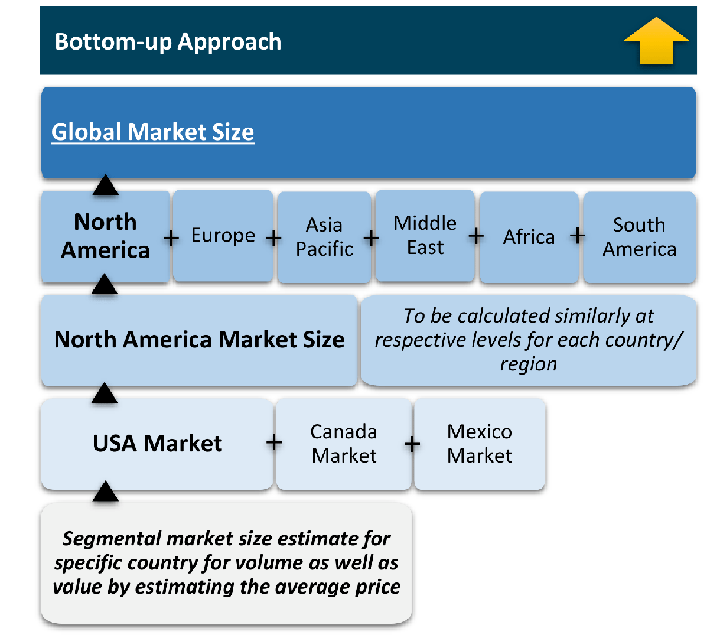
The bottom-up approach builds market estimates by starting with the smallest addressable market units and systematically aggregating them to create comprehensive market size projections.
This method begins with specific, granular data points and builds upward to create the complete market landscape.
Customer Analysis → Segmental Analysis → Geographical Analysis
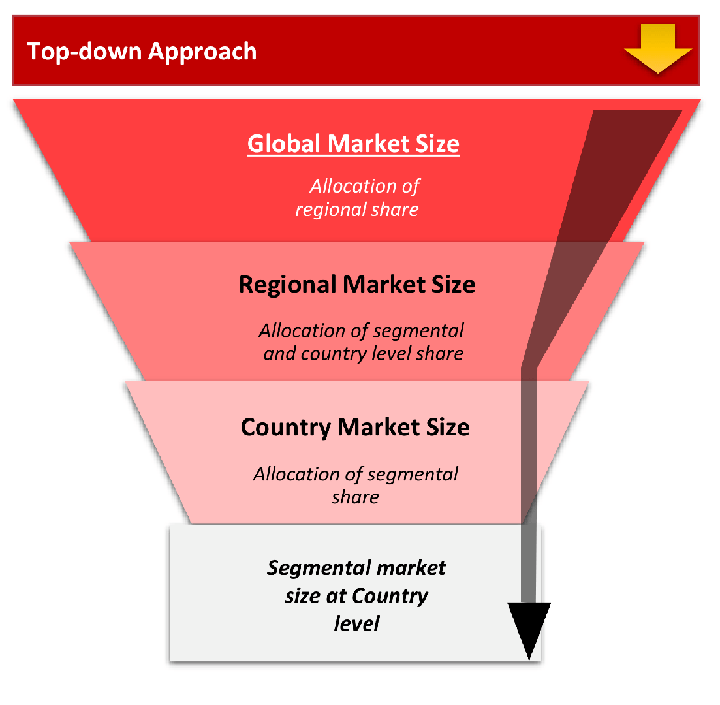
The top-down approach starts with the broadest possible market data and systematically narrows it down through a series of filters and assumptions to arrive at specific market segments or opportunities.
This method begins with the big picture and works downward to increasingly specific market slices.
TAM → SAM → SOM
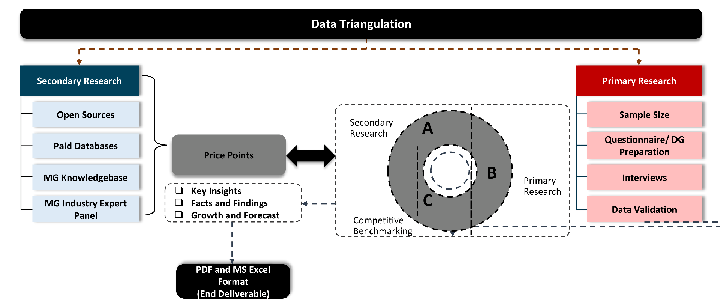
While analysing the market, we extensively study secondary sources, directories, and databases to identify and collect information useful for this technical, market-oriented, and commercial report. Secondary sources that we utilize are not only the public sources, but it is combination of Open Source, Associations, Paid Databases, MG Repository & Knowledgebase and Others.
- Company websites, annual reports, financial reports, broker reports, and investor presentations
- National government documents, statistical databases and reports
- News articles, press releases and web-casts specific to the companies operating in the market, Magazines, reports, and others
- We gather information from commercial data sources for deriving company specific data such as segmental revenue, share for geography, product revenue, and others
- Internal and external proprietary databases (industry-specific), relevant patent, and regulatory databases
- Governing Bodies, Government Organizations
- Relevant Authorities, Country-specific Associations for Industries
We also employ the model mapping approach to estimate the product level market data through the players product portfolio
Primary research/ interviews is vital in analyzing the market. Most of the cases involves paid primary interviews. Primary sources includes primary interviews through e-mail interactions, telephonic interviews, surveys as well as face-to-face interviews with the different stakeholders across the value chain including several industry experts.
| Type of Respondents | Number of Primaries |
|---|---|
| Tier 2/3 Suppliers | ~20 |
| Tier 1 Suppliers | ~25 |
| End-users | ~25 |
| Industry Expert/ Panel/ Consultant | ~30 |
| Total | ~100 |
MG Knowledgebase
• Repository of industry blog, newsletter and case studies
• Online platform covering detailed market reports, and company profiles
- Historical Trends – Past market patterns, cycles, and major events that shaped how markets behave over time. Understanding past trends helps predict future behavior.
- Industry Factors – Specific characteristics of the industry like structure, regulations, and innovation cycles that affect market dynamics.
- Macroeconomic Factors – Economic conditions like GDP growth, inflation, and employment rates that affect how much money people have to spend.
- Demographic Factors – Population characteristics like age, income, and location that determine who can buy your product.
- Technology Factors – How quickly people adopt new technology and how much technology infrastructure exists.
- Regulatory Factors – Government rules, laws, and policies that can help or restrict market growth.
- Competitive Factors – Analyzing competition structure such as degree of competition and bargaining power of buyers and suppliers.
Multiple Regression Analysis
- Identify and quantify factors that drive market changes
- Statistical modeling to establish relationships between market drivers and outcomes
Time Series Analysis – Seasonal Patterns
- Understand regular cyclical patterns in market demand
- Advanced statistical techniques to separate trend, seasonal, and irregular components
Time Series Analysis – Trend Analysis
- Identify underlying market growth patterns and momentum
- Statistical analysis of historical data to project future trends
Expert Opinion – Expert Interviews
- Gather deep industry insights and contextual understanding
- In-depth interviews with key industry stakeholders
Multi-Scenario Development
- Prepare for uncertainty by modeling different possible futures
- Creating optimistic, pessimistic, and most likely scenarios
Time Series Analysis – Moving Averages
- Sophisticated forecasting for complex time series data
- Auto-regressive integrated moving average models with seasonal components
Econometric Models
- Apply economic theory to market forecasting
- Sophisticated economic models that account for market interactions
Expert Opinion – Delphi Method
- Harness collective wisdom of industry experts
- Structured, multi-round expert consultation process
Monte Carlo Simulation
- Quantify uncertainty and probability distributions
- Thousands of simulations with varying input parameters
Our research framework is built upon the fundamental principle of validating market intelligence from both demand and supply perspectives. This dual-sided approach ensures comprehensive market understanding and reduces the risk of single-source bias.
Demand-Side Analysis: We understand end-user/application behavior, preferences, and market needs along with the penetration of the product for specific application.
Supply-Side Analysis: We estimate overall market revenue, analyze the segmental share along with industry capacity, competitive landscape, and market structure.
Data triangulation is a validation technique that uses multiple methods, sources, or perspectives to examine the same research question, thereby increasing the credibility and reliability of research findings. In market research, triangulation serves as a quality assurance mechanism that helps identify and minimize bias, validate assumptions, and ensure accuracy in market estimates.
- Data Source Triangulation – Using multiple data sources to examine the same phenomenon
- Methodological Triangulation – Using multiple research methods to study the same research question
- Investigator Triangulation – Using multiple researchers or analysts to examine the same data
- Theoretical Triangulation – Using multiple theoretical perspectives to interpret the same data