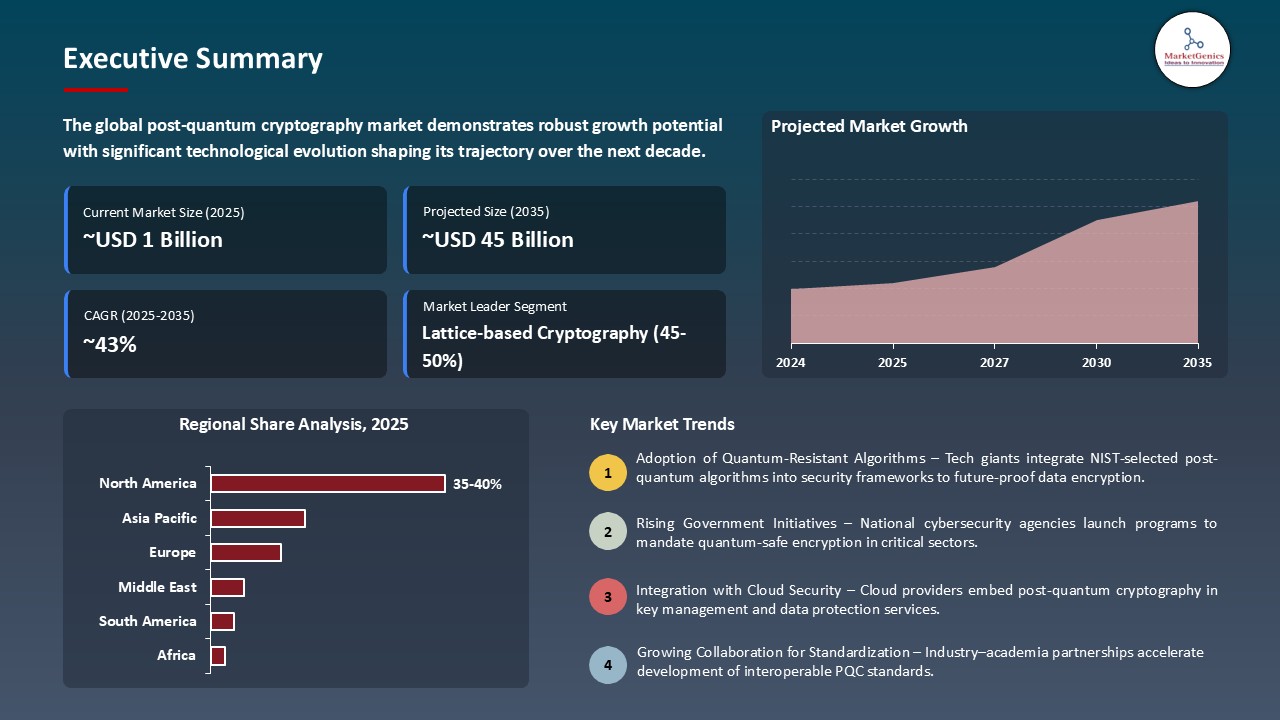
- The global post-quantum cryptography market is valued at USD 1.3 billion in 2025.
- The market is projected to grow at a CAGR of 42.5% during the forecast period of 2026 to 2035.
- The lattice-based cryptography segment dominates the global post-quantum cryptography market, accounting for ~49% share, due to its strong security foundation and efficiency against quantum attacks
- Rising demand for post-quantum cryptography is driven by increasing concerns over quantum threats to existing encryption systems
- Growing adoption of quantum-safe security solutions across government and financial sectors is fueling market demand
- The top five players account for over 30% of the global post-quantum-cryptography-market in 2025
- In August 2025, Palo Alto Networks launched new multi-cloud security solutions including a Quantum Readiness Dashboard, cipher translation for quantum-safe encryption, and 14 Next-Gen Firewall models with post-quantum cryptography support
- In November 2025, PQShield partnered with Keysight to validate the robustness of its quantum-safe cryptography solutions
- Global Post-Quantum Cryptography Market is likely to create the total forecasting opportunity of ~USD 44 Bn till 2035
- North America’s post-quantum cryptography market offers strong opportunities in government defense modernization, secure financial infrastructure, and quantum-resilient cybersecurity solutions
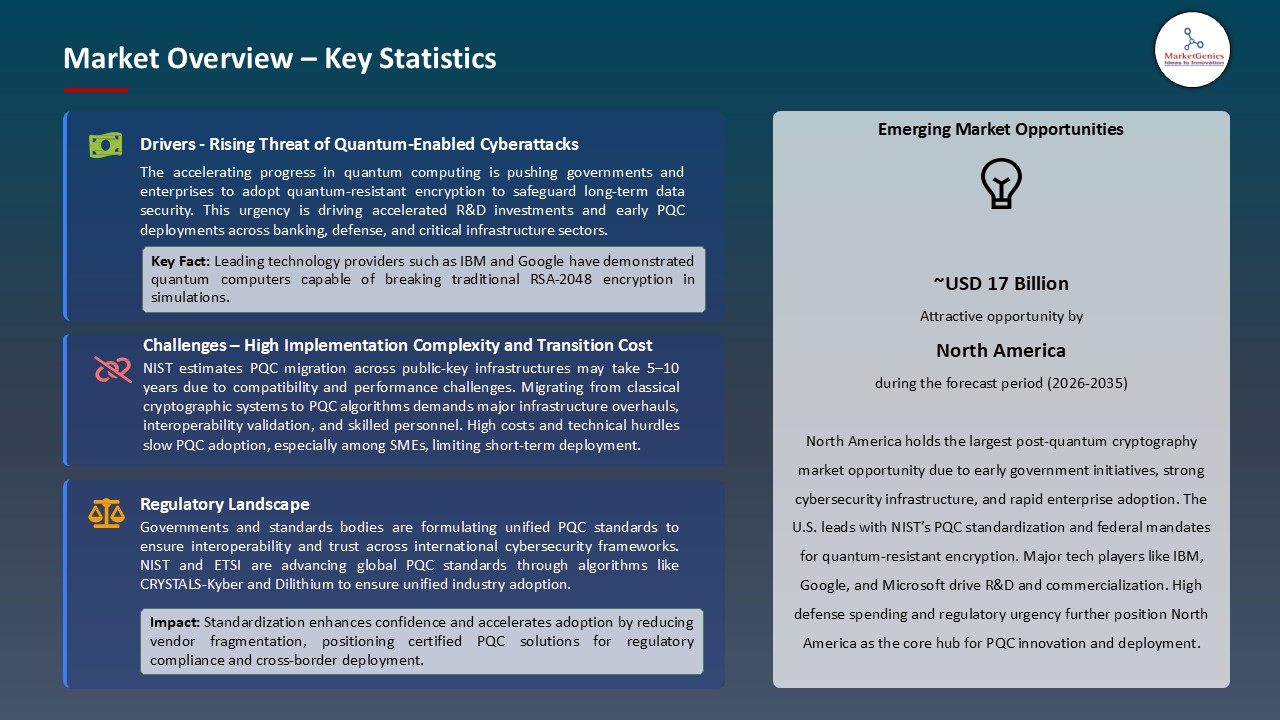
- The fast development in the field of quantum computing leads to an urgent demand of cryptographic solutions which can resist quantum attacks. Classical encryption schemes (RSA, ECC) use mathematical problems which can be effectively addressed using quantum algorithms (including the Shor algorithm). With the advancement of quantum hardware and its availability, the possibility of data breach with sensitive information such as financial transactions, communications of the government, and personal data increases exponentially.
- Investments in post-quantum cryptography are being hastened among organizations in various sectors to protect the security of the long-term data and regulatory requirements. This increase of demand is also supported by governments and standard organizations, including NIST, which is actively advocating the move towards the use of quantum-resistant algorithms.
- Infineon Technologies together with the BSI of Germany became the first to have a Common Criteria certification of a security controller using a post-quantum cryptography (PQC) algorithm in 2025. This achievement shows the initial use of quantum-resistant encryption in the business, which will guarantee protection of sensitive data over time against the emerging quantum threat.
- The intersection of quantum computing and proactive adoption of PQC is a crucial change moving towards the future, resistant to quantum cybersecurity in industries.
- The performance requirements and complexity of quantum-resistant algorithms deter the adoption of post-quantum cryptography by a large factor. The key sizes, the computational resources and the integration required by PQC solutions are typically larger than the classical encryption algorithms such as RSA or ECC. These conditions can lead to the increased latency, increased memory usage, and even incompatibility with the legacy hardware and software systems.
- Moreover, companies are required to spend a lot of money on testing, validation, and training of employees to make sure that the implementation of PQC solutions is safe, efficient, and reliable. These technical and operational difficulties expand the implementation costs and the implementation time, thus posing a challenge to organizations, especially those with high-volume and real-time applications, such as cloud computing, IoT networks, financial transactions, and telecommunication systems.
- Further, the absence of standardized tools and industry practices also makes deployment challenging. Thus, the market demand of quantum resistant security is increasing, but its practical implementation is slow due to the performance trade-offs and the difficulty in implementing PQC into existing infrastructure.
- Governments around the world are focusing on the security of critical infrastructure such as energy grids, transportation, health, and defense communications against any new cyber threat. The emergence of quantum computing poses a threat to the conventional encryption tools, and as a result, post-quantum cryptography (PQC) may have a growing role in the government as a means of ensuring a long-term guarantee of data security and continuity of operation.
- The regulatory programs and systems, including the PQC standardization work of NIST, are also driving the uptake by the government as a whole, making PQC vendors able to collaborate with government agencies, military, and infrastructure providers.
- Arqit, a quantum-safe encryption pioneer, was chosen in the UK NCSC PQC Pilot in 2025, and in the UK NCSC PQC Pilot, with its Encryption Intelligence product, Arqit will aid critical organizations in evaluating cryptographic risks and convert to quantum-safe security.
- The increasing national cybersecurity and the need to protect vulnerable systems and the demand of post-quantum cryptography solutions are highlighted by governmental developments and market demand.
- The cryptographic agility architectures are becoming one of the prominent trends in the post-quantum cryptography market that enables organizations to be able to switch between classical and quantum-resistant algorithms without significant system reengineering. This interoperability allows businesses to meet changing security risks, undertake hybrid cryptography approaches and keep pace with new standards including NIST guidelines on PQC.
- Agility assimilation within the cryptographic designs, enterprises are able to future-proof digital infrastructure, mitigate operational risk, and make the process of transitioning to quantum-resistant encryption easier as PQC algorithms keep developing and advancing.
- Accenture invested in QuSecure to build on its QuProtect platform to offer crypto-agility solutions to organizations in 2025, allowing organizations to effortlessly transition to classical and post-quantum cryptographic algorithms and maintain the ability to seamlessly encrypt their data with flexible encryption against newly appearing quantum threats.
- Cryptographic agility is driving the post-quantum cryptography market to the point of adaptive, robust, and future secure encryption.
- Lattice-based cryptography has turned out to be the most successful category in the global post-quantum cryptography market, owing to its high security guarantees, performance, and flexibility. The algorithms have been described to be extremely resistant to quantum computer attacks, and are thus the best in securing sensitive data in various industries including the finance sector, healthcare, government and the critical infrastructure.
- A lattice-based scheme can provide the high-level cryptographic functions, such as key exchange, digital signature, and fully homomorphic encryption, allowing safe computation of encrypted data without loss of confidentiality. The implementation of lattice-based cryptography is motivated by the PQC standardization of NIST and investments in scalable, high-performance, quantum-resistant systems by vendors, this guarantees long-term privacy of digital assets and communications.
- Lattice Semiconductor became the first manufacturer to introduce an FPGA family with secure control FPGAs, the MachXO5-NX TDQ, in 2025, based on CNSA 2.0-compliant post-quantum cryptography, crypto-agility, and hardware Root of Trust, in an intended to offer quantum-resistant security to computing, communications, industrial, and automotive applications.
- Lattice-based cryptography is still the dominant segment in post-quantum cryptography market because of its strong level of security, efficiency, and versatility.
- North America has become the most influential region in the post-quantum cryptography market, based on the massive investments in the sphere of cybersecurity, the development of advanced research, and the implementation of the quantum-resistant technologies. There are also large PQC vendors, government agencies and technology hubs in the region that are in the process of preparing to be affected by quantum computing on sensitive digital assets.
- Effective regulatory measures, including the PQC standardization activities by NIST, and government activities to protect critical infrastructure, defense communications, and financial systems, are driving the implementation of post-quantum encryption solutions.
- Furthermore, the high demand is inspired by the rising rates of chronic musculoskeletal disorders, the aging trends and rising tendency of patients to same-day operations. The North American providers also early adopt innovations in imaging and AI-enabled surgical devices and telemedicine services, which function to enhance the quality of the provided procedures and patient outcomes. Moreover, the growing risk of cyberattacks on organizations in the business world and the state sector has increased the need to have a highly secure system resistant to quantum attacks.
- Commvault added to its PQC products HQC, CRYSTALS-Kyber, Dilithium, SPHINCS+, and FALCON in a crypto-agility architecture, allowing financial and healthcare enterprises in the North America region to protect their data against quantum-enabled attacks and spur regional PQC market development.
- Adoption of post-quantum cryptography is increasing at a high pace all over the world boosting data security and leading to market expansion within industries.
- In August 2025, Palo Alto Networks introduced new multi-cloud security built-ins such as a Quantum Readiness Dashboard, quantum-safe encryption cipher translation, and 14 Next-Gen Firewall models with post-quantum cryptography help to enable enterprises to evaluate, secure, and future-proof workloads in cloud and artificial intelligence environments.
- In November 2025, PQShield collaborated with Keysight to test the resiliency of its quantum-safe cryptography products, with PQShield post-quantum algorithms and Keysight security testing and measurement skills, guaranteeing high-assurance deployment of their solutions in enterprises and critical infrastructure.
- United States
- Canada
- Mexico
- Germany
- United Kingdom
- France
- Italy
- Spain
- Netherlands
- Nordic Countries
- Poland
- Russia & CIS
- China
- India
- Japan
- South Korea
- Australia and New Zealand
- Indonesia
- Malaysia
- Thailand
- Vietnam
- Turkey
- UAE
- Saudi Arabia
- Israel
- South Africa
- Egypt
- Nigeria
- Algeria
- Brazil
- Argentina
- Amazon Web Services (AWS)
- Cisco Systems
- Crypto4A Technologies
- Cryptomathic
- evolutionQ
- Fortinet
- Google LLC
- IBM Corporation
- ISARA Corporation
- ID Quantique
- Infineon Technologies
- Intel Corporation
- Juniper Networks
- KETS Quantum Security
- Microsoft Corporation
- NXP Semiconductors
- Palo Alto Networks
- PQShield
- Qrypt
- Qualcomm Technologies
- Quantinuum
- QuintessenceLabs
- QuSecure
- Thales Group
- Utimaco
- Other Key Players
- Lattice-based Cryptography
- Learning with Errors (LWE)
- Ring Learning with Errors (Ring-LWE)
- Module Learning with Errors (Module-LWE)
- NTRU-based algorithms
- Others
- Hash-based Cryptography
- SPHINCS+
- XMSS (eXtended Merkle Signature Scheme)
- LMS (Leighton-Micali Signature)
- Others
- Code-based Cryptography
- Classic McEliece
- BIKE (Bit Flipping Key Encapsulation)
- HQC (Hamming Quasi-Cyclic)
- Others
- Multivariate Polynomial Cryptography
- Rainbow
- GeMSS
- LUOV
- Others
- Isogeny-based Cryptography
- SIKE (Supersingular Isogeny Key Encapsulation)
- CSIDH
- Others
- Solutions/Software
- Encryption Software
- Key Management Systems
- Authentication Solutions
- Digital Signature Solutions
- Others
- Services
- Consulting Services
- Implementation & Integration Services
- Support & Maintenance Services
- Training & Education Services
- Others
- On-premises
- Cloud-based
- Edge Computing
- Network Security
- Application Security
- Endpoint Security
- Cloud Security
- IoT Security
- Database Security
- Others
- Quantum Key Distribution (QKD) Integration
- Blockchain Integration
- Artificial Intelligence/Machine Learning Integration
- Zero Trust Architecture Integration
- Hardware Security Module (HSM) Integration
- Others
- 128-bit
- 192-bit
- 256-bit
- 512-bit and Above
- BFSI (Banking, Financial Services & Insurance)
- Payment Processing & Transactions
- Digital Banking & Mobile Banking
- Fraud Detection & Prevention
- Customer Data Protection
- Regulatory Compliance
- Others
- Government & Defense
- National Security & Intelligence
- Military Communications
- Critical Infrastructure Protection
- Secure Government Communications
- Border Security & Surveillance
- Others
- IT & Telecommunications
- 5G/6G Network Security
- Data Center Security
- Cloud Service Protection
- Telecom Infrastructure Security
- Satellite Communications
- Others
- Healthcare & Life Sciences
- Electronic Health Records (EHR) Protection
- Medical Device Security
- Patient Data Privacy
- Clinical Trial Data Security
- Telemedicine Security
- Others
- Retail & E-commerce
- Online Transaction Security
- Customer Payment Information Protection
- Supply Chain Security
- Point-of-Sale (POS) Security
- Loyalty Program Data Protection
- Others
- Energy & Utilities
- Smart Grid Security
- SCADA System Protection
- Power Plant Security
- Oil & Gas Infrastructure Security
- Renewable Energy Systems Security
- Others
- Manufacturing & Industrial
- Industrial IoT (IIoT) Security
- Intellectual Property Protection
- Supply Chain Management Security
- Automation System Security
- Quality Control Data Protection
- Others
- Transportation & Logistics
- Connected Vehicle Security
- Air Traffic Control Systems
- Maritime Security Systems
- Fleet Management Security
- Autonomous Vehicle Communication
- Others
- Education & Research
- Academic Research Data Protection
- Student Information Systems Security
- Online Learning Platform Security
- Library Systems Security
- Collaboration Tools Security
- Others
- Media & Entertainment
- Digital Rights Management (DRM)
- Content Distribution Security
- Streaming Platform Protection
- Gaming Platform Security
- Intellectual Property Protection
- Others
- Other Industries
- 1. Research Methodology and Assumptions
- 1.1. Definitions
- 1.2. Research Design and Approach
- 1.3. Data Collection Methods
- 1.4. Base Estimates and Calculations
- 1.5. Forecasting Models
- 1.5.1. Key Forecast Factors & Impact Analysis
- 1.6. Secondary Research
- 1.6.1. Open Sources
- 1.6.2. Paid Databases
- 1.6.3. Associations
- 1.7. Primary Research
- 1.7.1. Primary Sources
- 1.7.2. Primary Interviews with Stakeholders across Ecosystem
- 2. Executive Summary
- 2.1. Global Post-Quantum Cryptography Market Outlook
- 2.1.1. Post-Quantum Cryptography Market Size (Value - US$ Bn), and Forecasts, 2021-2035
- 2.1.2. Compounded Annual Growth Rate Analysis
- 2.1.3. Growth Opportunity Analysis
- 2.1.4. Segmental Share Analysis
- 2.1.5. Geographical Share Analysis
- 2.2. Market Analysis and Facts
- 2.3. Supply-Demand Analysis
- 2.4. Competitive Benchmarking
- 2.5. Go-to- Market Strategy
- 2.5.1. Customer/ End-use Industry Assessment
- 2.5.2. Growth Opportunity Data, 2026-2035
- 2.5.2.1. Regional Data
- 2.5.2.2. Country Data
- 2.5.2.3. Segmental Data
- 2.5.3. Identification of Potential Market Spaces
- 2.5.4. GAP Analysis
- 2.5.5. Potential Attractive Price Points
- 2.5.6. Prevailing Market Risks & Challenges
- 2.5.7. Preferred Sales & Marketing Strategies
- 2.5.8. Key Recommendations and Analysis
- 2.5.9. A Way Forward
- 2.1. Global Post-Quantum Cryptography Market Outlook
- 3. Industry Data and Premium Insights
- 3.1. Global Information Technology & Media Industry Overview, 2025
- 3.1.1. Information Technology & Media Industry Ecosystem Analysis
- 3.1.2. Key Trends for Information Technology & Media Industry
- 3.1.3. Regional Distribution for Information Technology & Media Industry
- 3.2. Supplier Customer Data
- 3.3. Technology Roadmap and Developments
- 3.4. Trade Analysis
- 3.4.1. Import & Export Analysis, 2025
- 3.4.2. Top Importing Countries
- 3.4.3. Top Exporting Countries
- 3.5. Trump Tariff Impact Analysis
- 3.5.1. Manufacturer
- 3.5.1.1. Based on the component & Raw material
- 3.5.2. Supply Chain
- 3.5.3. End Consumer
- 3.5.1. Manufacturer
- 3.6. Raw Material Analysis
- 3.1. Global Information Technology & Media Industry Overview, 2025
- 4. Market Overview
- 4.1. Market Dynamics
- 4.1.1. Drivers
- 4.1.1.1. Imminent threat from quantum computing breaking current cryptographic systems
- 4.1.1.2. Rising cyber‑attack incidents and heightened security awareness
- 4.1.1.3. Increasing investments in PQC research and standardization efforts
- 4.1.2. Restraints
- 4.1.2.1. High implementation and migration costs for adopting PQC
- 4.1.2.2. Lack of standardized PQC algorithms and integration complexity
- 4.1.1. Drivers
- 4.2. Key Trend Analysis
- 4.3. Regulatory Framework
- 4.3.1. Key Regulations, Norms, and Subsidies, by Key Countries
- 4.3.2. Tariffs and Standards
- 4.3.3. Impact Analysis of Regulations on the Market
- 4.4. Value Chain Analysis
- 4.4.1. Raw Material & Component Suppliers
- 4.4.2. Hardware Manufacturers & Software & Platform Providers
- 4.4.3. Service Providers
- 4.4.4. End-Users
- 4.5. Porter’s Five Forces Analysis
- 4.6. PESTEL Analysis
- 4.7. Global Post-Quantum Cryptography Market Demand
- 4.7.1. Historical Market Size –Value (US$ Bn), 2020-2024
- 4.7.2. Current and Future Market Size –Value (US$ Bn), 2026–2035
- 4.7.2.1. Y-o-Y Growth Trends
- 4.7.2.2. Absolute $ Opportunity Assessment
- 4.1. Market Dynamics
- 5. Competition Landscape
- 5.1. Competition structure
- 5.1.1. Fragmented v/s consolidated
- 5.2. Company Share Analysis, 2025
- 5.2.1. Global Company Market Share
- 5.2.2. By Region
- 5.2.2.1. North America
- 5.2.2.2. Europe
- 5.2.2.3. Asia Pacific
- 5.2.2.4. Middle East
- 5.2.2.5. Africa
- 5.2.2.6. South America
- 5.3. Product Comparison Matrix
- 5.3.1. Specifications
- 5.3.2. Market Positioning
- 5.3.3. Pricing
- 5.1. Competition structure
- 6. Global Post-Quantum Cryptography Market Analysis, By Algorithm Type
- 6.1. Key Segment Analysis
- 6.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Algorithm Type, 2021-2035
- 6.2.1. Lattice-based Cryptography
- 6.2.1.1. Learning With Errors (LWE)
- 6.2.1.2. Ring Learning With Errors (Ring-LWE)
- 6.2.1.3. Module Learning With Errors (Module-LWE)
- 6.2.1.4. NTRU-based algorithms
- 6.2.1.5. Others
- 6.2.2. Hash-based Cryptography
- 6.2.2.1. SPHINCS+
- 6.2.2.2. XMSS (eXtended Merkle Signature Scheme)
- 6.2.2.3. LMS (Leighton-Micali Signature)
- 6.2.2.4. Others
- 6.2.3. Code-based Cryptography
- 6.2.3.1. Classic McEliece
- 6.2.3.2. BIKE (Bit Flipping Key Encapsulation)
- 6.2.3.3. HQC (Hamming Quasi-Cyclic)
- 6.2.3.4. Others
- 6.2.4. Multivariate Polynomial Cryptography
- 6.2.4.1. Rainbow
- 6.2.4.2. GeMSS
- 6.2.4.3. LUOV
- 6.2.4.4. Others
- 6.2.5. Isogeny-based Cryptography
- 6.2.5.1. SIKE (Supersingular Isogeny Key Encapsulation)
- 6.2.5.2. CSIDH
- 6.2.5.3. Others
- 6.2.1. Lattice-based Cryptography
- 7. Global Post-Quantum Cryptography Market Analysis, By Component
- 7.1. Key Segment Analysis
- 7.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Component, 2021-2035
- 7.2.1. Solutions/Software
- 7.2.1.1. Encryption Software
- 7.2.1.2. Key Management Systems
- 7.2.1.3. Authentication Solutions
- 7.2.1.4. Digital Signature Solutions
- 7.2.1.5. Others
- 7.2.2. Services
- 7.2.2.1. Consulting Services
- 7.2.2.2. Implementation & Integration Services
- 7.2.2.3. Support & Maintenance Services
- 7.2.2.4. Training & Education Services
- 7.2.2.5. Others
- 7.2.1. Solutions/Software
- 8. Global Post-Quantum Cryptography Market Analysis,By Deployment Mode
- 8.1. Key Segment Analysis
- 8.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Deployment Mode, 2021-2035
- 8.2.1. On-premises
- 8.2.2. Cloud-based
- 8.2.3. Edge Computing
- 9. Global Post-Quantum Cryptography Market Analysis, By Security Type
- 9.1. Key Segment Analysis
- 9.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Security Type, 2021-2035
- 9.2.1. Network Security
- 9.2.2. Application Security
- 9.2.3. Endpoint Security
- 9.2.4. Cloud Security
- 9.2.5. IoT Security
- 9.2.6. Database Security
- 9.2.7. Others
- 10. Global Post-Quantum Cryptography Market Analysis, By Technology Integration
- 10.1. Key Segment Analysis
- 10.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Technology Integration, 2021-2035
- 10.2.1. Quantum Key Distribution (QKD) Integration
- 10.2.2. Blockchain Integration
- 10.2.3. Artificial Intelligence/Machine Learning Integration
- 10.2.4. Zero Trust Architecture Integration
- 10.2.5. Hardware Security Module (HSM) Integration
- 10.2.6. Others
- 11. Global Post-Quantum Cryptography Market Analysis, By Encryption Key Size
- 11.1. Key Segment Analysis
- 11.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, By Encryption Key Size, 2021-2035
- 11.2.1. 128-bit
- 11.2.2. 192-bit
- 11.2.3. 256-bit
- 11.2.4. 512-bit and Above
- 12. Global Post-Quantum Cryptography Market Analysis, By End-use Industry
- 12.1. Key Segment Analysis
- 12.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, End-use Industry, 2021-2035
- 12.2.1. BFSI (Banking, Financial Services & Insurance)
- 12.2.1.1. Payment Processing & Transactions
- 12.2.1.2. Digital Banking & Mobile Banking
- 12.2.1.3. Fraud Detection & Prevention
- 12.2.1.4. Customer Data Protection
- 12.2.1.5. Regulatory Compliance
- 12.2.1.6. Others
- 12.2.2. Government & Defense
- 12.2.2.1. National Security & Intelligence
- 12.2.2.2. Military Communications
- 12.2.2.3. Critical Infrastructure Protection
- 12.2.2.4. Secure Government Communications
- 12.2.2.5. Border Security & Surveillance
- 12.2.2.6. Others
- 12.2.3. IT & Telecommunications
- 12.2.3.1. 5G/6G Network Security
- 12.2.3.2. Data Center Security
- 12.2.3.3. Cloud Service Protection
- 12.2.3.4. Telecom Infrastructure Security
- 12.2.3.5. Satellite Communications
- 12.2.3.6. Others
- 12.2.4. Healthcare & Life Sciences
- 12.2.4.1. Electronic Health Records (EHR) Protection
- 12.2.4.2. Medical Device Security
- 12.2.4.3. Patient Data Privacy
- 12.2.4.4. Clinical Trial Data Security
- 12.2.4.5. Telemedicine Security
- 12.2.4.6. Others
- 12.2.5. Retail & E-commerce
- 12.2.5.1. Online Transaction Security
- 12.2.5.2. Customer Payment Information Protection
- 12.2.5.3. Supply Chain Security
- 12.2.5.4. Point-of-Sale (POS) Security
- 12.2.5.5. Loyalty Program Data Protection
- 12.2.5.6. Others
- 12.2.6. Energy & Utilities
- 12.2.6.1. Smart Grid Security
- 12.2.6.2. SCADA System Protection
- 12.2.6.3. Power Plant Security
- 12.2.6.4. Oil & Gas Infrastructure Security
- 12.2.6.5. Renewable Energy Systems Security
- 12.2.6.6. Others
- 12.2.7. Manufacturing & Industrial
- 12.2.7.1. Industrial IoT (IIoT) Security
- 12.2.7.2. Intellectual Property Protection
- 12.2.7.3. Supply Chain Management Security
- 12.2.7.4. Automation System Security
- 12.2.7.5. Quality Control Data Protection
- 12.2.7.6. Others
- 12.2.8. Transportation & Logistics
- 12.2.8.1. Connected Vehicle Security
- 12.2.8.2. Air Traffic Control Systems
- 12.2.8.3. Maritime Security Systems
- 12.2.8.4. Fleet Management Security
- 12.2.8.5. Autonomous Vehicle Communication
- 12.2.8.6. Others
- 12.2.9. Education & Research
- 12.2.9.1. Academic Research Data Protection
- 12.2.9.2. Student Information Systems Security
- 12.2.9.3. Online Learning Platform Security
- 12.2.9.4. Library Systems Security
- 12.2.9.5. Collaboration Tools Security
- 12.2.9.6. Others
- 12.2.10. Media & Entertainment
- 12.2.10.1. Digital Rights Management (DRM)
- 12.2.10.2. Content Distribution Security
- 12.2.10.3. Streaming Platform Protection
- 12.2.10.4. Gaming Platform Security
- 12.2.10.5. Intellectual Property Protection
- 12.2.10.6. Others
- 12.2.11. Other Industries
- 12.2.1. BFSI (Banking, Financial Services & Insurance)
- 13. Global Post-Quantum Cryptography Market Analysis and Forecasts, by Region
- 13.1. Key Findings
- 13.2. Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, by Region, 2021-2035
- 13.2.1. North America
- 13.2.2. Europe
- 13.2.3. Asia Pacific
- 13.2.4. Middle East
- 13.2.5. Africa
- 13.2.6. South America
- 14. North America Post-Quantum Cryptography Market Analysis
- 14.1. Key Segment Analysis
- 14.2. Regional Snapshot
- 14.3. North America Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 14.3.1. Algorithm Type
- 14.3.2. Component
- 14.3.3. Deployment Mode
- 14.3.4. Security Type
- 14.3.5. Technology Integration
- 14.3.6. Encryption Key Size
- 14.3.7. End-use Industry
- 14.3.8. Country
- 14.3.8.1. USA
- 14.3.8.2. Canada
- 14.3.8.3. Mexico
- 14.4. USA Post-Quantum Cryptography Market
- 14.4.1. Country Segmental Analysis
- 14.4.2. Algorithm Type
- 14.4.3. Component
- 14.4.4. Deployment Mode
- 14.4.5. Security Type
- 14.4.6. Technology Integration
- 14.4.7. Encryption Key Size
- 14.4.8. End-use Industry
- 14.5. Canada Post-Quantum Cryptography Market
- 14.5.1. Country Segmental Analysis
- 14.5.2. Algorithm Type
- 14.5.3. Component
- 14.5.4. Deployment Mode
- 14.5.5. Security Type
- 14.5.6. Technology Integration
- 14.5.7. Encryption Key Size
- 14.5.8. End-use Industry
- 14.6. Mexico Post-Quantum Cryptography Market
- 14.6.1. Country Segmental Analysis
- 14.6.2. Algorithm Type
- 14.6.3. Component
- 14.6.4. Deployment Mode
- 14.6.5. Security Type
- 14.6.6. Technology Integration
- 14.6.7. Encryption Key Size
- 14.6.8. End-use Industry
- 15. Europe Post-Quantum Cryptography Market Analysis
- 15.1. Key Segment Analysis
- 15.2. Regional Snapshot
- 15.3. Europe Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 15.3.1. Algorithm Type
- 15.3.2. Component
- 15.3.3. Deployment Mode
- 15.3.4. Security Type
- 15.3.5. Technology Integration
- 15.3.6. Encryption Key Size
- 15.3.7. End-use Industry
- 15.3.8. Country
- 15.3.8.1. Germany
- 15.3.8.2. United Kingdom
- 15.3.8.3. France
- 15.3.8.4. Italy
- 15.3.8.5. Spain
- 15.3.8.6. Netherlands
- 15.3.8.7. Nordic Countries
- 15.3.8.8. Poland
- 15.3.8.9. Russia & CIS
- 15.3.8.10. Rest of Europe
- 15.4. Germany Post-Quantum Cryptography Market
- 15.4.1. Country Segmental Analysis
- 15.4.2. Algorithm Type
- 15.4.3. Component
- 15.4.4. Deployment Mode
- 15.4.5. Security Type
- 15.4.6. Technology Integration
- 15.4.7. Encryption Key Size
- 15.4.8. End-use Industry
- 15.5. United Kingdom Post-Quantum Cryptography Market
- 15.5.1. Country Segmental Analysis
- 15.5.2. Algorithm Type
- 15.5.3. Component
- 15.5.4. Deployment Mode
- 15.5.5. Security Type
- 15.5.6. Technology Integration
- 15.5.7. Encryption Key Size
- 15.5.8. End-use Industry
- 15.6. France Post-Quantum Cryptography Market
- 15.6.1. Country Segmental Analysis
- 15.6.2. Algorithm Type
- 15.6.3. Component
- 15.6.4. Deployment Mode
- 15.6.5. Security Type
- 15.6.6. Technology Integration
- 15.6.7. Encryption Key Size
- 15.6.8. End-use Industry
- 15.7. Italy Post-Quantum Cryptography Market
- 15.7.1. Country Segmental Analysis
- 15.7.2. Algorithm Type
- 15.7.3. Component
- 15.7.4. Deployment Mode
- 15.7.5. Security Type
- 15.7.6. Technology Integration
- 15.7.7. Encryption Key Size
- 15.7.8. End-use Industry
- 15.8. Spain Post-Quantum Cryptography Market
- 15.8.1. Country Segmental Analysis
- 15.8.2. Algorithm Type
- 15.8.3. Component
- 15.8.4. Deployment Mode
- 15.8.5. Security Type
- 15.8.6. Technology Integration
- 15.8.7. Encryption Key Size
- 15.8.8. End-use Industry
- 15.9. Netherlands Post-Quantum Cryptography Market
- 15.9.1. Country Segmental Analysis
- 15.9.2. Algorithm Type
- 15.9.3. Component
- 15.9.4. Deployment Mode
- 15.9.5. Security Type
- 15.9.6. Technology Integration
- 15.9.7. Encryption Key Size
- 15.9.8. End-use Industry
- 15.10. Nordic Countries Post-Quantum Cryptography Market
- 15.10.1. Country Segmental Analysis
- 15.10.2. Algorithm Type
- 15.10.3. Component
- 15.10.4. Deployment Mode
- 15.10.5. Security Type
- 15.10.6. Technology Integration
- 15.10.7. Encryption Key Size
- 15.10.8. End-use Industry
- 15.11. Poland Post-Quantum Cryptography Market
- 15.11.1. Country Segmental Analysis
- 15.11.2. Algorithm Type
- 15.11.3. Component
- 15.11.4. Deployment Mode
- 15.11.5. Security Type
- 15.11.6. Technology Integration
- 15.11.7. Encryption Key Size
- 15.11.8. End-use Industry
- 15.12. Russia & CIS Post-Quantum Cryptography Market
- 15.12.1. Country Segmental Analysis
- 15.12.2. Algorithm Type
- 15.12.3. Component
- 15.12.4. Deployment Mode
- 15.12.5. Security Type
- 15.12.6. Technology Integration
- 15.12.7. Encryption Key Size
- 15.12.8. End-use Industry
- 15.13. Rest of Europe Post-Quantum Cryptography Market
- 15.13.1. Country Segmental Analysis
- 15.13.2. Algorithm Type
- 15.13.3. Component
- 15.13.4. Deployment Mode
- 15.13.5. Security Type
- 15.13.6. Technology Integration
- 15.13.7. Encryption Key Size
- 15.13.8. End-use Industry
- 16. Asia Pacific Post-Quantum Cryptography Market Analysis
- 16.1. Key Segment Analysis
- 16.2. Regional Snapshot
- 16.3. Asia Pacific Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 16.3.1. Algorithm Type
- 16.3.2. Component
- 16.3.3. Deployment Mode
- 16.3.4. Security Type
- 16.3.5. Technology Integration
- 16.3.6. Encryption Key Size
- 16.3.7. End-use Industry
- 16.3.8. Country
- 16.3.8.1. China
- 16.3.8.2. India
- 16.3.8.3. Japan
- 16.3.8.4. South Korea
- 16.3.8.5. Australia and New Zealand
- 16.3.8.6. Indonesia
- 16.3.8.7. Malaysia
- 16.3.8.8. Thailand
- 16.3.8.9. Vietnam
- 16.3.8.10. Rest of Asia Pacific
- 16.4. China Post-Quantum Cryptography Market
- 16.4.1. Country Segmental Analysis
- 16.4.2. Algorithm Type
- 16.4.3. Component
- 16.4.4. Deployment Mode
- 16.4.5. Security Type
- 16.4.6. Technology Integration
- 16.4.7. Encryption Key Size
- 16.4.8. End-use Industry
- 16.5. India Post-Quantum Cryptography Market
- 16.5.1. Country Segmental Analysis
- 16.5.2. Algorithm Type
- 16.5.3. Component
- 16.5.4. Deployment Mode
- 16.5.5. Security Type
- 16.5.6. Technology Integration
- 16.5.7. Encryption Key Size
- 16.5.8. End-use Industry
- 16.6. Japan Post-Quantum Cryptography Market
- 16.6.1. Country Segmental Analysis
- 16.6.2. Algorithm Type
- 16.6.3. Component
- 16.6.4. Deployment Mode
- 16.6.5. Security Type
- 16.6.6. Technology Integration
- 16.6.7. Encryption Key Size
- 16.6.8. End-use Industry
- 16.7. South Korea Post-Quantum Cryptography Market
- 16.7.1. Country Segmental Analysis
- 16.7.2. Algorithm Type
- 16.7.3. Component
- 16.7.4. Deployment Mode
- 16.7.5. Security Type
- 16.7.6. Technology Integration
- 16.7.7. Encryption Key Size
- 16.7.8. End-use Industry
- 16.8. Australia and New Zealand Post-Quantum Cryptography Market
- 16.8.1. Country Segmental Analysis
- 16.8.2. Algorithm Type
- 16.8.3. Component
- 16.8.4. Deployment Mode
- 16.8.5. Security Type
- 16.8.6. Technology Integration
- 16.8.7. Encryption Key Size
- 16.8.8. End-use Industry
- 16.9. Indonesia Post-Quantum Cryptography Market
- 16.9.1. Country Segmental Analysis
- 16.9.2. Algorithm Type
- 16.9.3. Component
- 16.9.4. Deployment Mode
- 16.9.5. Security Type
- 16.9.6. Technology Integration
- 16.9.7. Encryption Key Size
- 16.9.8. End-use Industry
- 16.10. Malaysia Post-Quantum Cryptography Market
- 16.10.1. Country Segmental Analysis
- 16.10.2. Algorithm Type
- 16.10.3. Component
- 16.10.4. Deployment Mode
- 16.10.5. Security Type
- 16.10.6. Technology Integration
- 16.10.7. Encryption Key Size
- 16.10.8. End-use Industry
- 16.11. Thailand Post-Quantum Cryptography Market
- 16.11.1. Country Segmental Analysis
- 16.11.2. Algorithm Type
- 16.11.3. Component
- 16.11.4. Deployment Mode
- 16.11.5. Security Type
- 16.11.6. Technology Integration
- 16.11.7. Encryption Key Size
- 16.11.8. End-use Industry
- 16.12. Vietnam Post-Quantum Cryptography Market
- 16.12.1. Country Segmental Analysis
- 16.12.2. Algorithm Type
- 16.12.3. Component
- 16.12.4. Deployment Mode
- 16.12.5. Security Type
- 16.12.6. Technology Integration
- 16.12.7. Encryption Key Size
- 16.12.8. End-use Industry
- 16.13. Rest of Asia Pacific Post-Quantum Cryptography Market
- 16.13.1. Country Segmental Analysis
- 16.13.2. Algorithm Type
- 16.13.3. Component
- 16.13.4. Deployment Mode
- 16.13.5. Security Type
- 16.13.6. Technology Integration
- 16.13.7. Encryption Key Size
- 16.13.8. End-use Industry
- 17. Middle East Post-Quantum Cryptography Market Analysis
- 17.1. Key Segment Analysis
- 17.2. Regional Snapshot
- 17.3. Middle East Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 17.3.1. Algorithm Type
- 17.3.2. Component
- 17.3.3. Deployment Mode
- 17.3.4. Security Type
- 17.3.5. Technology Integration
- 17.3.6. Encryption Key Size
- 17.3.7. End-use Industry
- 17.3.8. Country
- 17.3.8.1. Turkey
- 17.3.8.2. UAE
- 17.3.8.3. Saudi Arabia
- 17.3.8.4. Israel
- 17.3.8.5. Rest of Middle East
- 17.4. Turkey Post-Quantum Cryptography Market
- 17.4.1. Country Segmental Analysis
- 17.4.2. Algorithm Type
- 17.4.3. Component
- 17.4.4. Deployment Mode
- 17.4.5. Security Type
- 17.4.6. Technology Integration
- 17.4.7. Encryption Key Size
- 17.4.8. End-use Industry
- 17.5. UAE Post-Quantum Cryptography Market
- 17.5.1. Country Segmental Analysis
- 17.5.2. Algorithm Type
- 17.5.3. Component
- 17.5.4. Deployment Mode
- 17.5.5. Security Type
- 17.5.6. Technology Integration
- 17.5.7. Encryption Key Size
- 17.5.8. End-use Industry
- 17.6. Saudi Arabia Post-Quantum Cryptography Market
- 17.6.1. Country Segmental Analysis
- 17.6.2. Algorithm Type
- 17.6.3. Component
- 17.6.4. Deployment Mode
- 17.6.5. Security Type
- 17.6.6. Technology Integration
- 17.6.7. Encryption Key Size
- 17.6.8. End-use Industry
- 17.7. Israel Post-Quantum Cryptography Market
- 17.7.1. Country Segmental Analysis
- 17.7.2. Algorithm Type
- 17.7.3. Component
- 17.7.4. Deployment Mode
- 17.7.5. Security Type
- 17.7.6. Technology Integration
- 17.7.7. Encryption Key Size
- 17.7.8. End-use Industry
- 17.8. Rest of Middle East Post-Quantum Cryptography Market
- 17.8.1. Country Segmental Analysis
- 17.8.2. Algorithm Type
- 17.8.3. Component
- 17.8.4. Deployment Mode
- 17.8.5. Security Type
- 17.8.6. Technology Integration
- 17.8.7. Encryption Key Size
- 17.8.8. End-use Industry y
- 18. Africa Post-Quantum Cryptography Market Analysis
- 18.1. Key Segment Analysis
- 18.2. Regional Snapshot
- 18.3. Africa Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 18.3.1. Algorithm Type
- 18.3.2. Component
- 18.3.3. Deployment Mode
- 18.3.4. Security Type
- 18.3.5. Technology Integration
- 18.3.6. Encryption Key Size
- 18.3.7. End-use Industry
- 18.3.8. Country
- 18.3.8.1. South Africa
- 18.3.8.2. Egypt
- 18.3.8.3. Nigeria
- 18.3.8.4. Algeria
- 18.3.8.5. Rest of Africa
- 18.4. South Africa Post-Quantum Cryptography Market
- 18.4.1. Country Segmental Analysis
- 18.4.2. Algorithm Type
- 18.4.3. Component
- 18.4.4. Deployment Mode
- 18.4.5. Security Type
- 18.4.6. Technology Integration
- 18.4.7. Encryption Key Size
- 18.4.8. End-use Industry
- 18.5. Egypt Post-Quantum Cryptography Market
- 18.5.1. Country Segmental Analysis
- 18.5.2. Algorithm Type
- 18.5.3. Component
- 18.5.4. Deployment Mode
- 18.5.5. Security Type
- 18.5.6. Technology Integration
- 18.5.7. Encryption Key Size
- 18.5.8. End-use Industry
- 18.6. Nigeria Post-Quantum Cryptography Market
- 18.6.1. Country Segmental Analysis
- 18.6.2. Algorithm Type
- 18.6.3. Component
- 18.6.4. Deployment Mode
- 18.6.5. Security Type
- 18.6.6. Technology Integration
- 18.6.7. Encryption Key Size
- 18.6.8. End-use Industry
- 18.7. Algeria Post-Quantum Cryptography Market
- 18.7.1. Country Segmental Analysis
- 18.7.2. Algorithm Type
- 18.7.3. Component
- 18.7.4. Deployment Mode
- 18.7.5. Security Type
- 18.7.6. Technology Integration
- 18.7.7. Encryption Key Size
- 18.7.8. End-use Industry
- 18.8. Rest of Africa Post-Quantum Cryptography Market
- 18.8.1. Country Segmental Analysis
- 18.8.2. Algorithm Type
- 18.8.3. Component
- 18.8.4. Deployment Mode
- 18.8.5. Security Type
- 18.8.6. Technology Integration
- 18.8.7. Encryption Key Size
- 18.8.8. End-use Industry
- 19. South America Post-Quantum Cryptography Market Analysis
- 19.1. Key Segment Analysis
- 19.2. Regional Snapshot
- 19.3. South America Post-Quantum Cryptography Market Size (Value - US$ Bn), Analysis, and Forecasts, 2021-2035
- 19.3.1. Algorithm Type
- 19.3.2. Component
- 19.3.3. Deployment Mode
- 19.3.4. Security Type
- 19.3.5. Technology Integration
- 19.3.6. Encryption Key Size
- 19.3.7. End-use Industry
- 19.3.8. Country
- 19.3.8.1. Brazil
- 19.3.8.2. Argentina
- 19.3.8.3. Rest of South America
- 19.4. Brazil Post-Quantum Cryptography Market
- 19.4.1. Country Segmental Analysis
- 19.4.2. Algorithm Type
- 19.4.3. Component
- 19.4.4. Deployment Mode
- 19.4.5. Security Type
- 19.4.6. Technology Integration
- 19.4.7. Encryption Key Size
- 19.4.8. End-use Industry
- 19.5. Argentina Post-Quantum Cryptography Market
- 19.5.1. Country Segmental Analysis
- 19.5.2. Algorithm Type
- 19.5.3. Component
- 19.5.4. Deployment Mode
- 19.5.5. Security Type
- 19.5.6. Technology Integration
- 19.5.7. Encryption Key Size
- 19.5.8. End-use Industry
- 19.6. Rest of South America Post-Quantum Cryptography Market
- 19.6.1. Country Segmental Analysis
- 19.6.2. Algorithm Type
- 19.6.3. Component
- 19.6.4. Deployment Mode
- 19.6.5. Security Type
- 19.6.6. Technology Integration
- 19.6.7. Encryption Key Size
- 19.6.8. End-use Industry
- 20. Key Players/ Company Profile
- 20.1. Amazon Web Services (AWS)
- 20.1.1. Company Details/ Overview
- 20.1.2. Company Financials
- 20.1.3. Key Customers and Competitors
- 20.1.4. Business/ Industry Portfolio
- 20.1.5. Product Portfolio/ Specification Details
- 20.1.6. Pricing Data
- 20.1.7. Strategic Overview
- 20.1.8. Recent Developments
- 20.2. Cisco Systems
- 20.3. Crypto4A Technologies
- 20.4. Cryptomathic
- 20.5. evolutionQ
- 20.6. Fortinet
- 20.7. Google LLC
- 20.8. IBM Corporation
- 20.9. ID Quantique
- 20.10. Infineon Technologies
- 20.11. Intel Corporation
- 20.12. ISARA Corporation
- 20.13. Juniper Networks
- 20.14. KETS Quantum Security
- 20.15. Microsoft Corporation
- 20.16. NXP Semiconductors
- 20.17. Palo Alto Networks
- 20.18. PQShield
- 20.19. Qrypt
- 20.20. Qualcomm Technologies
- 20.21. Quantinuum
- 20.22. QuintessenceLabs
- 20.23. QuSecure
- 20.24. Thales Group
- 20.25. Utimaco
- 20.26. Other Key Players
- 20.1. Amazon Web Services (AWS)
- Company websites, annual reports, financial reports, broker reports, and investor presentations
- National government documents, statistical databases and reports
- News articles, press releases and web-casts specific to the companies operating in the market, Magazines, reports, and others
- We gather information from commercial data sources for deriving company specific data such as segmental revenue, share for geography, product revenue, and others
- Internal and external proprietary databases (industry-specific), relevant patent, and regulatory databases
- Governing Bodies, Government Organizations
- Relevant Authorities, Country-specific Associations for Industries
- Historical Trends – Past market patterns, cycles, and major events that shaped how markets behave over time. Understanding past trends helps predict future behavior.
- Industry Factors – Specific characteristics of the industry like structure, regulations, and innovation cycles that affect market dynamics.
- Macroeconomic Factors – Economic conditions like GDP growth, inflation, and employment rates that affect how much money people have to spend.
- Demographic Factors – Population characteristics like age, income, and location that determine who can buy your product.
- Technology Factors – How quickly people adopt new technology and how much technology infrastructure exists.
- Regulatory Factors – Government rules, laws, and policies that can help or restrict market growth.
- Competitive Factors – Analyzing competition structure such as degree of competition and bargaining power of buyers and suppliers.
- Identify and quantify factors that drive market changes
- Statistical modeling to establish relationships between market drivers and outcomes
- Understand regular cyclical patterns in market demand
- Advanced statistical techniques to separate trend, seasonal, and irregular components
- Identify underlying market growth patterns and momentum
- Statistical analysis of historical data to project future trends
- Gather deep industry insights and contextual understanding
- In-depth interviews with key industry stakeholders
- Prepare for uncertainty by modeling different possible futures
- Creating optimistic, pessimistic, and most likely scenarios
- Sophisticated forecasting for complex time series data
- Auto-regressive integrated moving average models with seasonal components
- Apply economic theory to market forecasting
- Sophisticated economic models that account for market interactions
- Harness collective wisdom of industry experts
- Structured, multi-round expert consultation process
- Quantify uncertainty and probability distributions
- Thousands of simulations with varying input parameters
- Data Source Triangulation – Using multiple data sources to examine the same phenomenon
- Methodological Triangulation – Using multiple research methods to study the same research question
- Investigator Triangulation – Using multiple researchers or analysts to examine the same data
- Theoretical Triangulation – Using multiple theoretical perspectives to interpret the same data
Insightified
Mid-to-large firms spend $20K–$40K quarterly on systematic research and typically recover multiples through improved growth and profitability
Research is no longer optional. Leading firms use it to uncover $10M+ in hidden revenue opportunities annually
Our research-consulting programs yields measurable ROI: 20–30% revenue increases from new markets, 11% profit upticks from pricing, and 20–30% cost savings from operations
Post-Quantum Cryptography Market Size, Share & Trends Analysis Report by Algorithm Type (Lattice-based Cryptography, Hash-based Cryptography, Code-based Cryptography, Multivariate Polynomial Cryptography, Isogeny-based Cryptography), Component, Deployment Mode, Security Type, Technology Integration, Encryption Key Size, End-use Industry and Geography (North America, Europe, Asia Pacific, Middle East, Africa, and South America) – Global Industry Data, Trends, and Forecasts, 2026–2035
|
|
|
|
Segmental Data Insights |
|
|
Demand Trends |
|
|
Competitive Landscape |
|
|
Strategic Development |
|
|
Future Outlook & Opportunities |
|
Post-Quantum Cryptography Market Size, Share, and Growth
The global post-quantum cryptography market is witnessing strong growth, valued at USD 1.3 billion in 2025 and projected to reach USD 44.9 billion by 2035, expanding at a CAGR of 42.5% during the forecast period. The Asia-Pacific region is the fastest-growing for the post-quantum cryptography market because of increasing digital transformation, expanding cybersecurity investments, and government-led quantum technology initiatives.
Thomas Rosteck, Division President Connected Secure Systems at Infineon said that, “With our innovations in post-quantum cryptography and active contribution to algorithm development, Infineon is an integral part in finding future-proof PQC solutions, there is no question that quantum computers will be a reality; Therefore, we need to push forward with the migration to post-quantum cryptography decisively”.
The post-quantum cryptography market is driven by the rapid innovations of the post-quantum cryptography algorithms and hardware to support the cryptography algorithms. Researchers and companies are coming up with more efficient and standard quantum resistant algorithms that are highly secure with minimal computational and energy overheads. As an example, SEALSQ Corp demonstrated the release of their QuantumShield QS7001 chip, which is planned to be released in the middle of November of 2025. It is claimed to be the first chip to provide the National Institute of Standards and Technology (NIST)-standardized PQC algorithms CRYSTALSthat is, CRYSTALS-Kyber (ML-KEM) and CRYSTALS-Dilithium (ML-DSA) implemented directly on hardware.
The partnerships between the vendors of PQC, technology firms, and governments contribute to faster development, wider adoption, compliance, and lower costs and make the general market aware of the innovation, stimulating its overall expansion. An example is that in 2025, PQShield collaborated with Carahsoft Technology Corp. to make its post-quantum cryptography (PQC) solutions available to governmental organizations. Through this partnership, it is possible to move the public sector organizations to quantum-resistant encryption, responding to the arising cybersecurity issues and providing protection to sensitive data in the long term.
Post-quantum cryptography is an opportunity to optimize digital identity and authentication solutions, which allows managing identities safely and securing the online platform, preventing fraud and identity theft. As an example, in 2025, WISeKey released its second generation WISeID system, in which people and objects are unified into a decentralized model under post-quantum security, allowing secure and autonomous authentication and management of digital identities of people and devices worldwide.
Post-Quantum Cryptography Market Dynamics and Trends
Driver: Quantum Computing Progress Creates Urgent Cryptographic Imperative
Restraint: Implementation Complexity and Performance Overhead Slow Adoption
Opportunity: Critical Infrastructure Protection Creates Government Demand
Key Trend: Cryptographic Agility Architectures Enable Algorithm Flexibility
Post Quantum Cryptography Market Analysis and Segmental Data
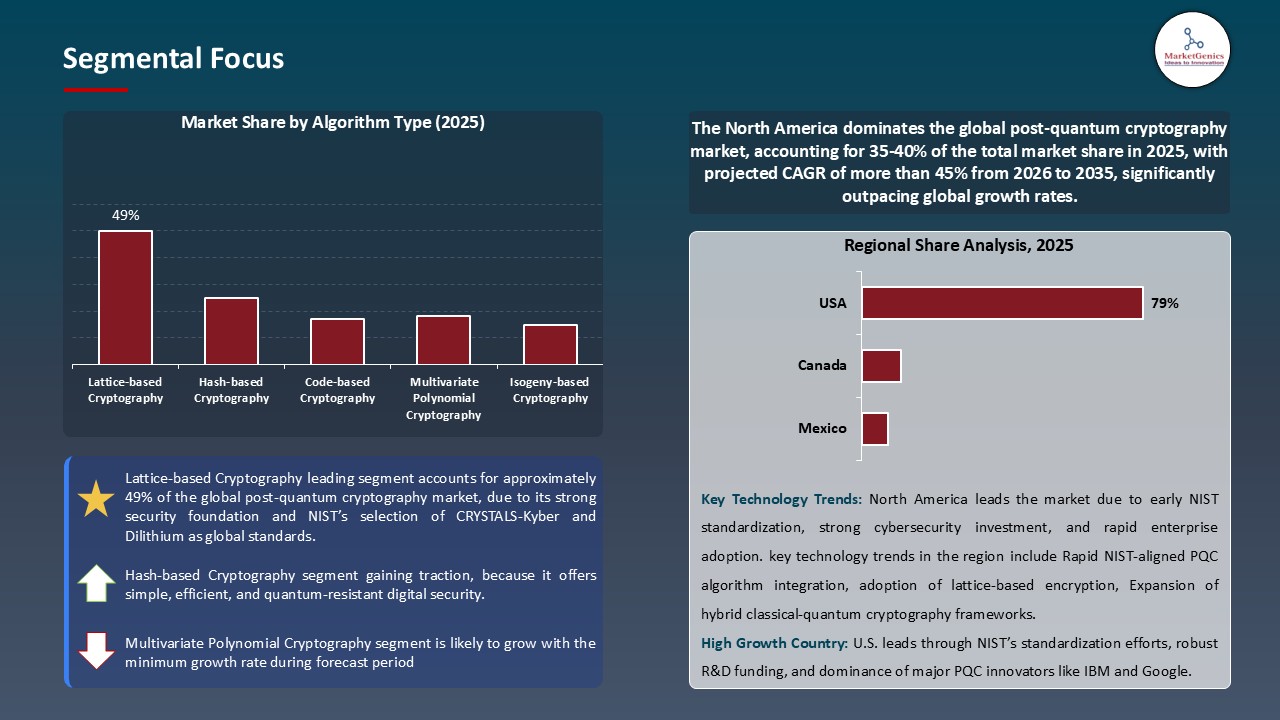
Lattice-based Cryptography Dominate Global Post-Quantum Cryptography Market
North America Leads Global Post-Quantum Cryptography Market Demand
Post-Quantum-Cryptography-Market Ecosystem
The worldwide post-quantum cryptography market is fragmented with key players like IBM Corporation, Microsoft Corporation, PQShield, ISARA Corporation, and Thales Group sharing about 27% of the market share as a group. These industry leaders have largely influenced the business landscape through their invention and implementation of highly developed quantum-resistant cryptographic schemes, such as lattice-based schemes, hash-based signatures, and crypto-agility designs. Their high-level R&D, large body of intellectual property, and proven technology ecosystems impose a high barrier of entry to new entrants.
There is also a strategic partnership with governments, enterprise IT and cloud service platforms to further hasten the integration of PQC solutions with important infrastructures, financial systems and digital identity platforms. Such alliances increase efficiency in operations, enable compliance with new standards like the NIST guidelines on PQC, and increase the adoption of the product across the industries, leading to market expansion and entrenching top PQC vendors.
The concentration of buyers is moderate as government agencies and big enterprises constitute significant initial revenue. The concentration of intellectual property in suppliers of algorithm is low considering the standards-based approach, but implementation expertise gives competitive differentiation.

Recent Development and Strategic Overview:
Report Scope
|
Detail |
|
|
Market Size in 2025 |
USD 1.3 Bn |
|
Market Forecast Value in 2035 |
USD 44.9 Bn |
|
Growth Rate (CAGR) |
42.5% |
|
Forecast Period |
2026 – 2035 |
|
Historical Data Available for |
2021 – 2024 |
|
Market Size Units |
US$ Billion for Value |
|
Report Format |
Electronic (PDF) + Excel |
|
North America |
Europe |
Asia Pacific |
Middle East |
Africa |
South America |
|
|
|
|
|
|
|
|
Companies Covered |
|||||
|
|
|
|
|
|
|
Post-Quantum-Cryptography-Market Segmentation and Highlights
|
Segment |
Sub-segment |
|
Post-Quantum Cryptography Market, By Algorithm Type |
|
|
Post-Quantum Cryptography Market, By Component |
|
|
Post-Quantum Cryptography Market, By Deployment Mode |
|
|
Post-Quantum Cryptography Market, By Security Type |
|
|
Post-Quantum Cryptography Market, By Technology Integration |
|
|
Post-Quantum Cryptography Market, By Encryption Key Size |
|
|
Post-Quantum Cryptography Market, By End-use Industry |
|
Frequently Asked Questions
Table of Contents
Note* - This is just tentative list of players. While providing the report, we will cover more number of players based on their revenue and share for each geography
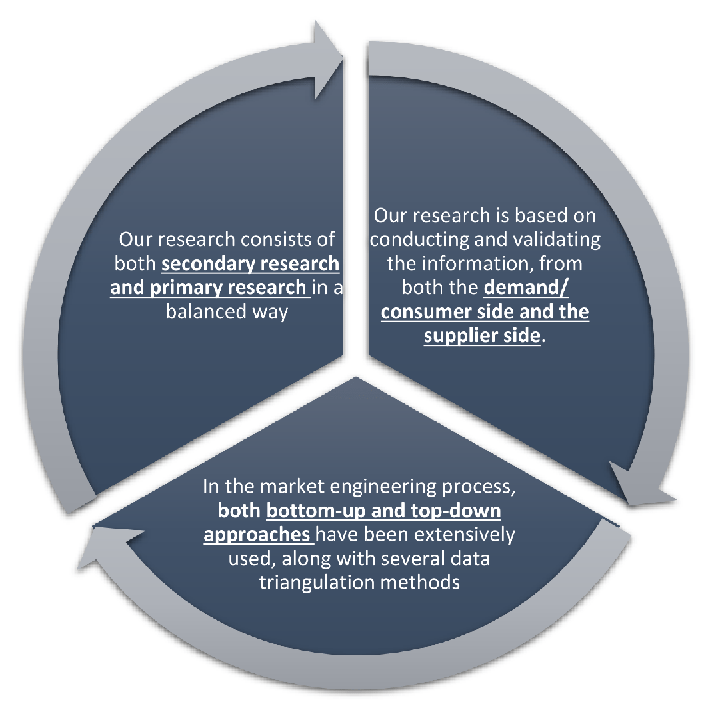
Research Design
Our research design integrates both demand-side and supply-side analysis through a balanced combination of primary and secondary research methodologies. By utilizing both bottom-up and top-down approaches alongside rigorous data triangulation methods, we deliver robust market intelligence that supports strategic decision-making.
MarketGenics' comprehensive research design framework ensures the delivery of accurate, reliable, and actionable market intelligence. Through the integration of multiple research approaches, rigorous validation processes, and expert analysis, we provide our clients with the insights needed to make informed strategic decisions and capitalize on market opportunities.
MarketGenics leverages a dedicated industry panel of experts and a comprehensive suite of paid databases to effectively collect, consolidate, and analyze market intelligence.
Our approach has consistently proven to be reliable and effective in generating accurate market insights, identifying key industry trends, and uncovering emerging business opportunities.
Through both primary and secondary research, we capture and analyze critical company-level data such as manufacturing footprints, including technical centers, R&D facilities, sales offices, and headquarters.
Our expert panel further enhances our ability to estimate market size for specific brands based on validated field-level intelligence.
Our data mining techniques incorporate both parametric and non-parametric methods, allowing for structured data collection, sorting, processing, and cleaning.
Demand projections are derived from large-scale data sets analyzed through proprietary algorithms, culminating in robust and reliable market sizing.
Research Approach
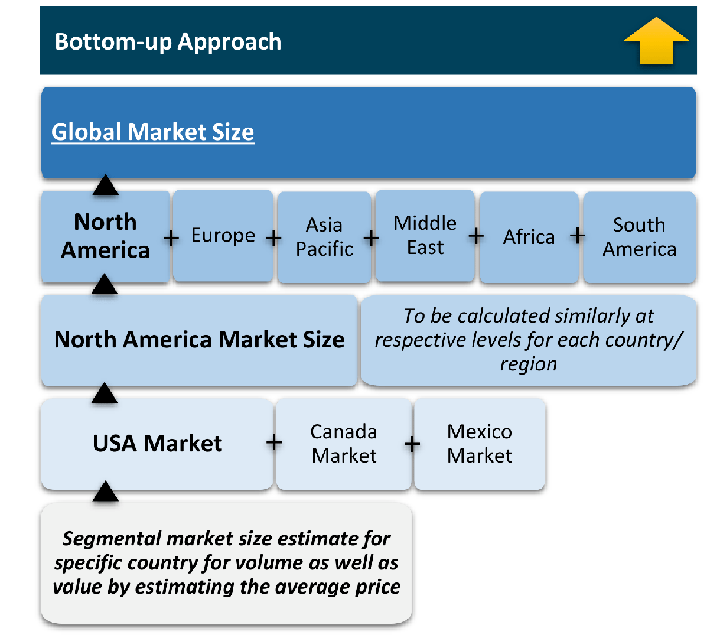
The bottom-up approach builds market estimates by starting with the smallest addressable market units and systematically aggregating them to create comprehensive market size projections.
This method begins with specific, granular data points and builds upward to create the complete market landscape.
Customer Analysis → Segmental Analysis → Geographical Analysis
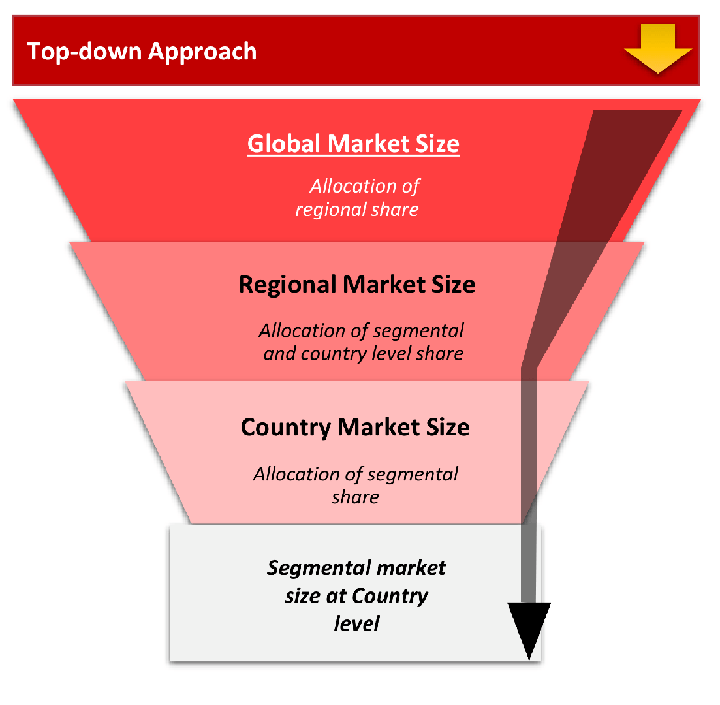
The top-down approach starts with the broadest possible market data and systematically narrows it down through a series of filters and assumptions to arrive at specific market segments or opportunities.
This method begins with the big picture and works downward to increasingly specific market slices.
TAM → SAM → SOM
Research Methods
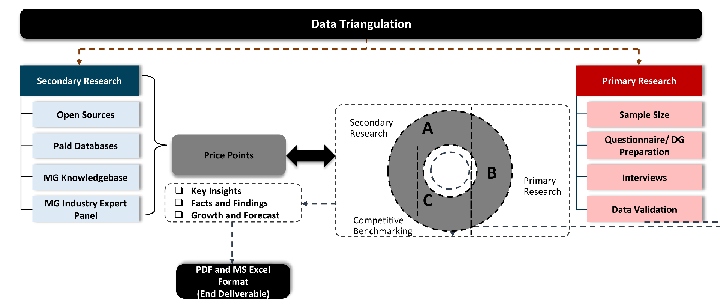
Desk / Secondary Research
While analysing the market, we extensively study secondary sources, directories, and databases to identify and collect information useful for this technical, market-oriented, and commercial report. Secondary sources that we utilize are not only the public sources, but it is a combination of Open Source, Associations, Paid Databases, MG Repository & Knowledgebase, and others.
We also employ the model mapping approach to estimate the product level market data through the players' product portfolio
Primary Research
Primary research/ interviews is vital in analyzing the market. Most of the cases involves paid primary interviews. Primary sources include primary interviews through e-mail interactions, telephonic interviews, surveys as well as face-to-face interviews with the different stakeholders across the value chain including several industry experts.
| Type of Respondents | Number of Primaries |
|---|---|
| Tier 2/3 Suppliers | ~20 |
| Tier 1 Suppliers | ~25 |
| End-users | ~25 |
| Industry Expert/ Panel/ Consultant | ~30 |
| Total | ~100 |
MG Knowledgebase
• Repository of industry blog, newsletter and case studies
• Online platform covering detailed market reports, and company profiles
Forecasting Factors and Models
Forecasting Factors
Forecasting Models / Techniques
Multiple Regression Analysis
Time Series Analysis – Seasonal Patterns
Time Series Analysis – Trend Analysis
Expert Opinion – Expert Interviews
Multi-Scenario Development
Time Series Analysis – Moving Averages
Econometric Models
Expert Opinion – Delphi Method
Monte Carlo Simulation
Research Analysis
Our research framework is built upon the fundamental principle of validating market intelligence from both demand and supply perspectives. This dual-sided approach ensures comprehensive market understanding and reduces the risk of single-source bias.
Demand-Side Analysis: We understand end-user/application behavior, preferences, and market needs along with the penetration of the product for specific application.
Supply-Side Analysis: We estimate overall market revenue, analyze the segmental share along with industry capacity, competitive landscape, and market structure.
Validation & Evaluation
Data triangulation is a validation technique that uses multiple methods, sources, or perspectives to examine the same research question, thereby increasing the credibility and reliability of research findings. In market research, triangulation serves as a quality assurance mechanism that helps identify and minimize bias, validate assumptions, and ensure accuracy in market estimates.
Custom Market Research Services
We will customise the research for you, in case the report listed above does not meet your requirements.
Get 10% Free Customisation